Home Assistant: Auto-renewing Let’s Encrypt SSL
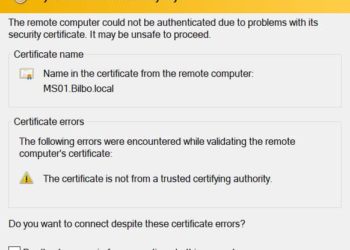
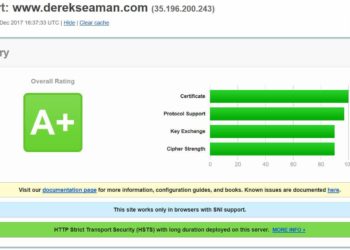
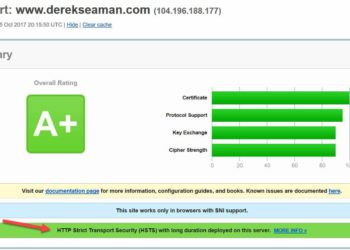
If you are running Home Assistant and wish to increase its security by using a FREE trusted SSL certificate from Let's Encrypt, then you are in luck! This post will walk you through the entire process. The process is quick and easy, assuming you already have a public domain via...