Introduction
I'm a huge fan of WordPress, and I've had this blog hosted on WordPress for many years. Given my security background, I always try and make my site as secure as possible, while not breaking functionality. One important feature, both for SEO and security is SSL. All you need a SSL certificate, right? Nope! And that's the basis of this post.
Not all SSL Configurations are the Same
Under the hood of SSL are a number of configuration options that you are probably not even aware of. Most of these relate to the supported protocols and cipher suites that can be negotiated with your site. These are generally web server back-end settings. A lot of SSL protocols and cipher suites have not lasted the test of time and are deemed flat out insecure or weak. For example, RC4, is pathetically insecure and should never be used.
Most quality WordPress hosting companies provide free SSL certificates. So many people think it's just a single click (or even automated) to get your site secure with SSL. Not so! Your hosting company configured which protocols and cipher suites are available. And if your hoster isn't security conscious they can leave your website vulnerable and degrade your site's security. Never for a second think just because you have a SSL certificate that you are secure!
How to test your SSL
Fortunately, it's dead easy even for a non-techie to test the SSL security of your site. All you need to do is go over to SSL labs and run a test against your domain. After a couple of minutes it will give your site a letter grade, and a lot of tech details about what it found. For example, on my WP Engine hosted WordPress sites I have an A+ rating. With a shared hosting plan with another company I got a poor B score with numerous security warnings. Take a minute and check your site now so you can see a full report.
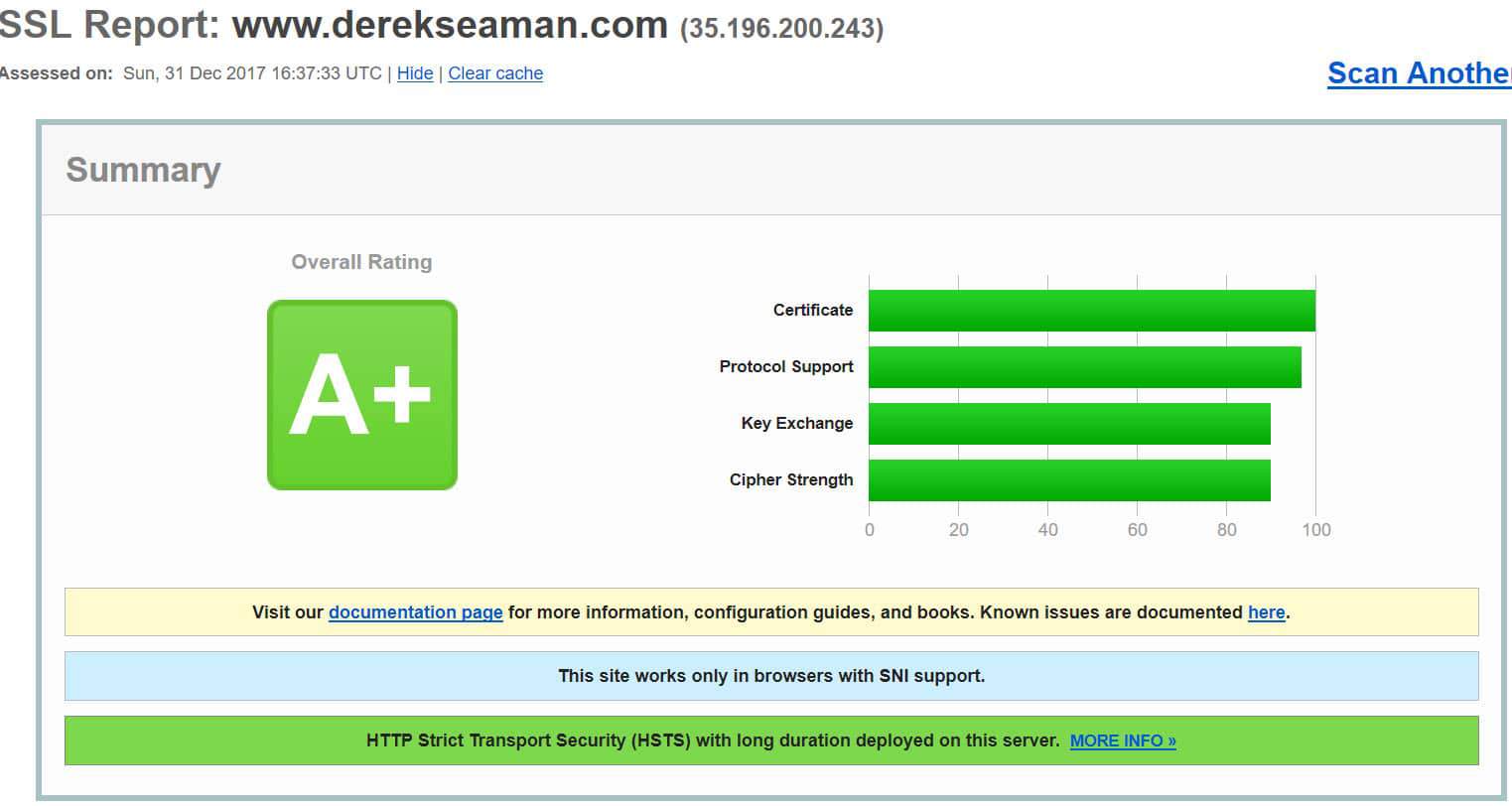
The "A+" SSL Lab Report
First let me start with a site that passes with flying colors, this blog site. As you can see in the graphic below, it scores an A+ and also uses HSTS. HSTS is a super-strict form of TLS/SSL that you can read more about how to configure in a blog post I wrote here. This test result is from my current provider, WP Engine, using their managed WordPress offering. It's not cheap by any means, but frankly you get what you pay for with hosting, in most cases.

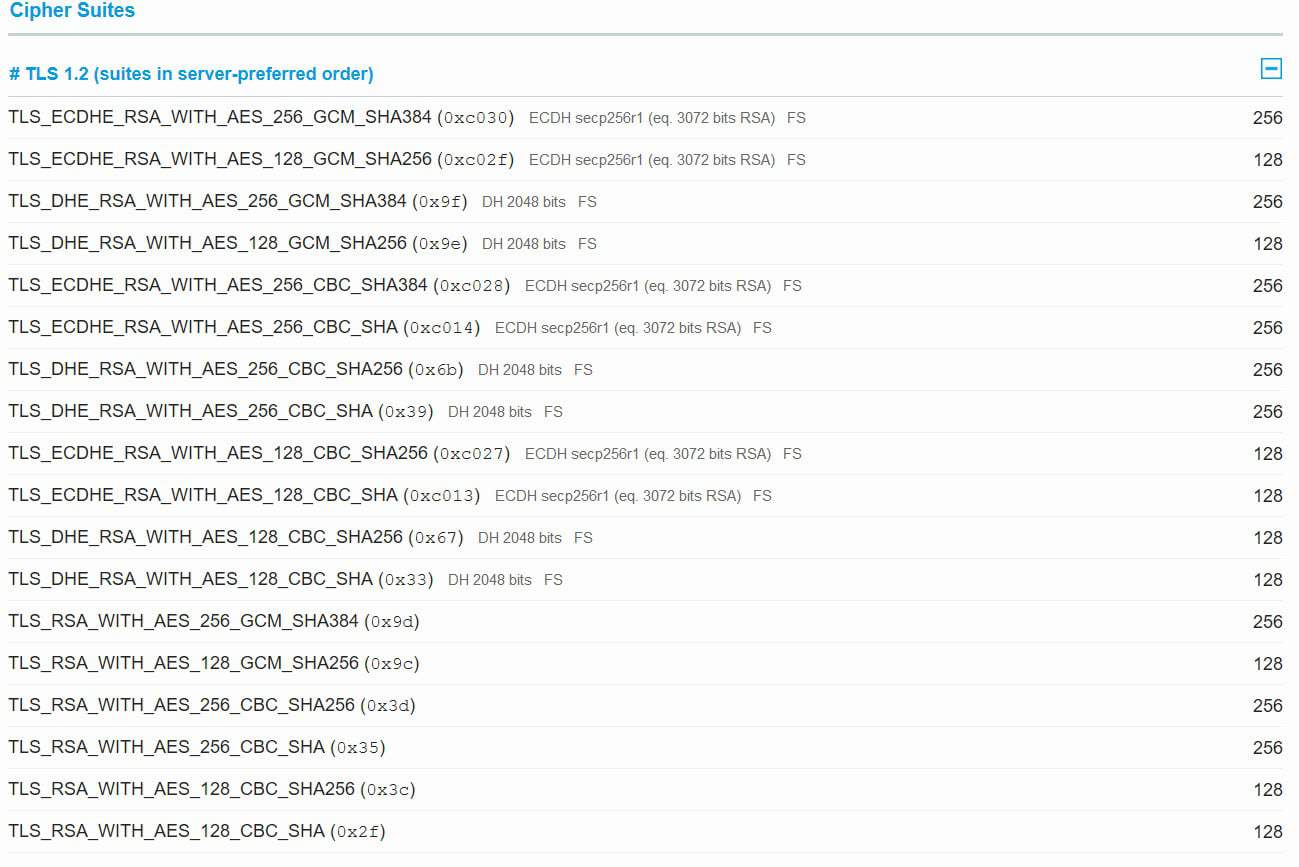
As you scroll down the report you also get a list of protocols and cipher suites that your site supports. Looking at the report below, you see that none of the cipher suites are tagged as insecure or weak. That is good! Looks exactly like what we want it to. Thank you WP Engine!

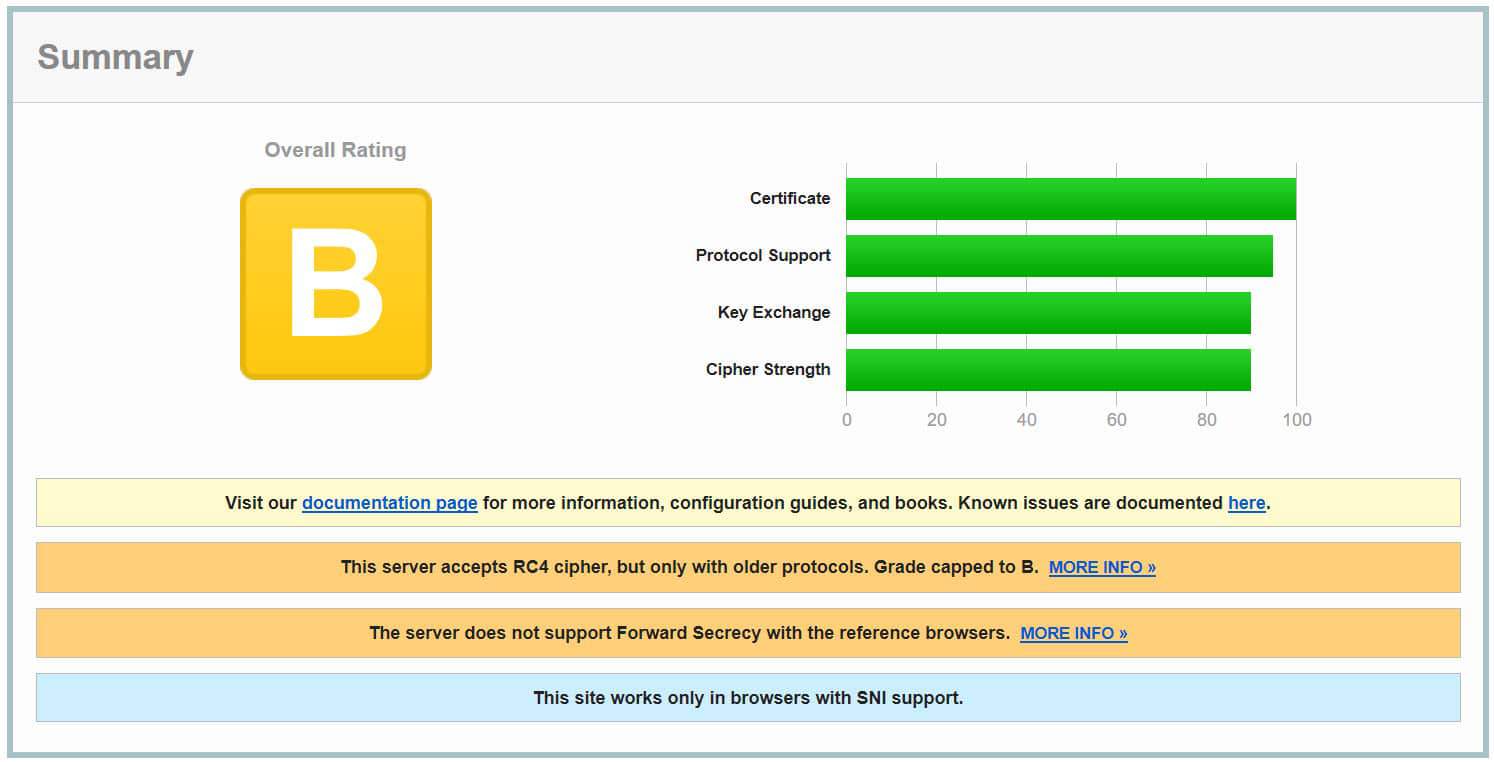
The "B" SSL Lab Report
Recently I got an economical (entry level, shared plan) WordPress hosting account with InMotion hosting, just for experimentation purposes. I could try out new tools, check out another hoster's performance, and see if there was any compelling reason to consider a future move away from WP Engine to something less expensive.
I stood up a new domain, got their free SSL certificate, and then ran a SSL Lab report scan. I was horrified to see the results. Overall it got a "B" which may not sound bad, but digging into the details really made me uneasy. And I had to contact their tech support, but more about that later in this post.

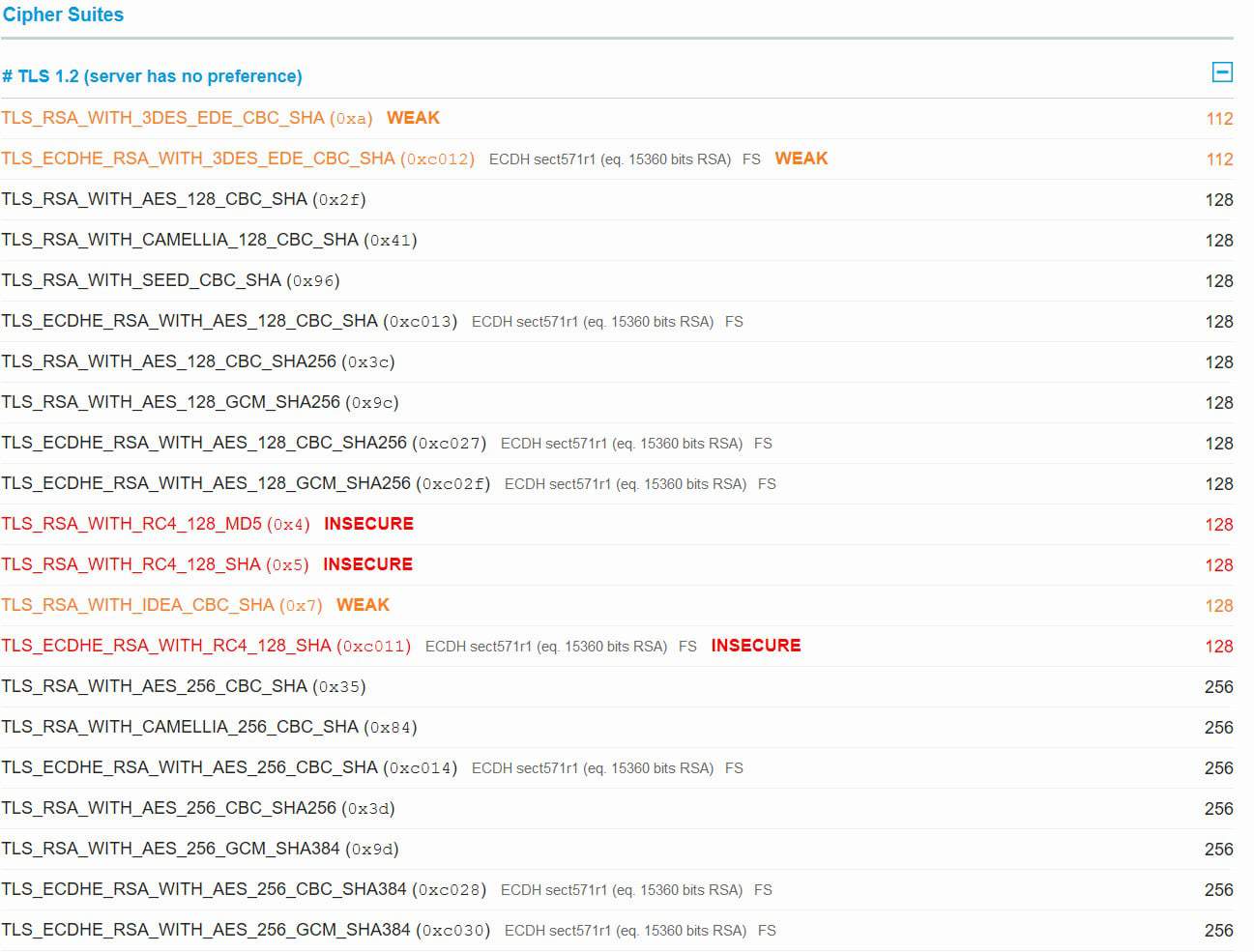
Looking into the details of the "B" grade you can see that RC4 is supported (very, very insecure) and that forward secrecy is not supported. But let's dig deeper into the cipher suites to see what's going on.

Right off the bat you can see three cipher suites are enabled that use RC4. Really bad! And another three cipher suites are labled 'weak'. Also not good, but not as bad as 'insecure'. Clearly, this is significantly worse than the WP Engine scan.
Fixing the Issues
Because the protocols and cipher suites are back-end configuration settings, I contacted InMotion tech support to see what they could do. And there was bad news, and good news. Firstly, for the shared plan I was using NOTHING could be done. As the TLS/SSL configuration is set across numerous customers. However, if one went with their VPS plans, individual sites can be configured per customer requirements. If I was on a VPS plan, then the hoster would take care of all the configuration. You should then re-test, and see if the security holes were plugged. An A+ rating is not to hard and doesn't require techie level skills.
Summary
Even if you have an SSL certificate on your site, that does NOT mean you are optimally configured. Your hoster could be using very insecure settings, but you'd never know without testing it. So if you have never tested your website's SSL, do it immediately. You may be shocked with what is lurking in the results. On the flip side, most of the work is done by your hosting service so you don't need to know what files to configure. I'd just send them a screenshot of the 'bad' results and tell them to fix it.
You also need to be conscious of which plan you are using with a provider, and how that impacts security. For example, my shared plan with InMotion doesn't allow them to tweak the SSL security whereas their VPS plan would. Whether you want to spend the additional money for VPS (or find another provider that's more secure by default), that's your call.
Knowledge is power, and knowing where your site's SSL stands is important. It's up to you whether you want to fix it and get an A+ rating or not. If you are running any type of security sensitive transactions like payments or storing personal information, I'd urge you to configure your site for an A+ SSL labs rating.





Great article – some that are not as familiar with ciphers and packet headers may benefit from knowing some of the basics – this is a good place to start to understand how it works and why you would want to implement it. https://security.stackexchange.com/questions/17264/hsts-extra-security-over-https