
This is Part 2 of 2 of the Ruckus Unleashed home Wi-Fi Best Practices Guide. In Part 1 we configured a number of settings including system time, country code, email alerting, radio configuration, and more. Part 2 will focus on SSID architecture and setting up a number of Wi-Fi networks (WLANs) for various use cases, such as homeowner IoT and guest networks. We will be deploying 3 or 4 WLANs, depending on your requirements. Let’s dig in!
Announcement: In May 2025 Ruckus released Unleashed 200.18. This is a major update to Unleashed with an ENTIRELY new UI/UX. This series from 2024 is based on Unleashed 200.17 and earlier and will not get future updates. See the Related Posts section below for links to the 2025 version that covers Unleashed 200.18.
Related Posts
Part 1: Ruckus Unleashed (200.18+) Best Practices Guide
Part 2: Ruckus Unleashed (200.18+) Best Practices Guide
Part 1: Ruckus Unleashed Best Practices Guide (200.17 and earlier)
Part 1: Ruckus One Home Wi-Fi Best Practices Guide
Part 2: Ruckus One Home Wi-Fi Best Practices Guide
Enterprise Grade Home Wi-Fi: Ruckus Unleashed vs. Ruckus One
Ruckus Unleashed to Ruckus One Migration Guide
Unleashing the Power of 6 GHz Wi-Fi: Re-Think Everything
Ruckus One: Provisioning ICX Switches
What's Covered?
This series of posts will cover the entire setup of Ruckus APs with Ruckus Unleashed for a residential setting. It will also show you how to deploy various networks such as homeowner and guests. Major sections in this series includes:
- Ruckus Access Point Selection (Part 1)
- Cross-Flashing Unleashed (Part1)
- Unleashed Initial Configuration (Part 1)
- Unleashed Firmware Update (Part 1)
- System Time (Part 1)
- Country Code and Channel Mode (Part 1)
- Email Alerts (Part 1)
- Radio Control (Part 1)
- Client Load Balancing (Part 1)
- Radar Avoidance Pre-Scanning (Part 1)
- PoE Troubleshooting (Part 1)
- AP Name and Location (Part 1)
- Management Interface IP (Part 1)
- SSID Architecture (Part 2)
- Guest Traffic Isolation (Part 2)
- Wi-Fi 7 Multi-Link Operations (MLO) (Part 2)
- Dynamic Pre-Shared Keys (DPSK) (Part 2)
- Wi-Fi Band Use Cases (Part 2)
- Wi-Fi Calling (Part 2)
- Firewall IPsec Passthrough (Part 2)
- 2.4 GHz Radio Configuration (Part 2)
- 5 GHz Radio Configuration (Part 2)
- 6 GHz Radio Configuration (Part 2)
- WI-Fi Networks: WLAN Details (Part 2)
- Wi-Fi Networks: WLAN Priority (Part 2)
- Wi-Fi Networks: Access Controls (Part 2)
- Wi-Fi Networks: Radio Control (Part 2)
- Wi-Fi Networks: Others (Part 2)
- Adding more Access Points (Part 2)
- Setting Preferred Master AP (Part 2)
- Troubleshooting (Part 2)
SSID Architecture
Best practices for enterprise APs, like Ruckus, is to broadcast no more than 4 SSIDs. For this residential best practices guide I recommend three or four SSIDs, depending on your requirements. For the homeowner we will have two SSIDs: One for 2.4 GHz IoT devices (smart speakers, doorbells, etc.) and another for the 5/6 GHz bands used for cell phones, laptops, tablets, etc. Some IoT devices don’t like SSIDs that are broadcasting on both 2.4 and 5 GHz, which is why I suggest a dedicated 2.4 GHz IoT SSID to head off potential issues.
For the guest networks I have two different use cases in mind. Pick which one best meets your requirements. The two use cases are:
1. A permanent ‘guest’ such as a cohabitating tenant or roommate: Dedicated 2.4 GHz SSID, and a 5 GHz WPA2 SSID. This separates the tenant’s IoT devices (2.4 GHz) from their primary high bandwidth devices (phone, laptop, tablet, etc), which should use 5 GHz.
2. Friends or family that you have over on occasion for an event: Single guest SSID that combines both the 2.4 GHz and 5 GHz bands and uses WPA2. Ruckus has some fancy guest network captive portal options you can use, but I’m keeping it simple with a single pre-shared passphrase. Since we aren’t concerned about IoT devices in this use case, combing 2.4 GHz and 5 GHz should not be a problem and provides extended Wi-Fi range.
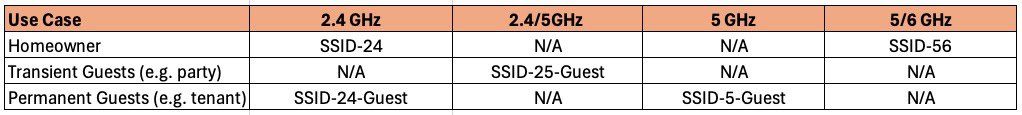
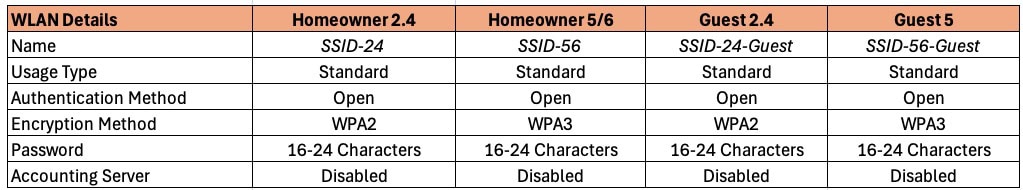
In the table below I you can see the various use cases and suggested SSID naming convention. You can of course use any SSID names you wish, but for the purposes of this article I’ll be using the naming convention below.
If your APs support the 6 GHz band I would keep 6 GHz for the exclusive use of the homeowner, unless there’s a strong case for giving guests access 6 GHz. Guests may also encounter some of the compatibility issues that can come with combining 5 GHz and 6 GHz, such as WPA3.
Guest Traffic Isolation
For your guest traffic consider if you want to isolate their traffic from your primary home network. If your scenario is more the casual party with trusted friends and family, then you might choose to not isolate their traffic to a dedicated (and firewalled) VLAN. This is by far the simplest solution, but is not as secure.
If, on the other hand, you have a tenant situation and have network gear that supports VLANs, you probably want to use a dedicated guest VLAN that is isolated from your primary homeowner network. An isolated guest network will require configuration on your switch/router/firewall.
For the remainder of this post I’ll cover the tenant use case with an isolated VLAN. But, you can easily modify the guest network to use a single SSID across the 2.4 and 5 GHz bands if you want to use the transient guests use case. This SSID would use VLAN 1, co-mingling their traffic with your primary home network.
Wi-Fi 7 Multi-Link Operation (MLO)
Wi-Fi 7 has a new feature called MLO, or Multi-Link Operation. This lets you combine up to two bands (2.4, 5 or 6 GHz) together for higher throughput and lower latency connections to select clients. However, as of February 2025, Unleashed does NOT support MLO. Ruckus does support MLO with their Ruckus One cloud controller (paid subscription). Frankly, I would not worry about MLO as there are interoperability issues at the moment.
For a lot more information on Wi-Fi 7 MLO, check out the Ruckus Wi-Fi 7 Multi-link Operations (MLO) blog post. For even more Wi-Fi 7 information, check out the Ruckus Whitepaper What to Know about Wi-Fi 7. And finally, watch this page for Ruckus blog posts on Wi-Fi 7.
Dynamic Pre-shared Keys (DPSK)
DPSK (Dynamic pre-shared keys), which is a Ruckus feature, is not recommended in a residential environment. DPSK lets you use a single SSID, but individual devices or groups of devices can use unique passphrases. You can then associate certain DPSKs to different VLANs, if you wish. However, due to the way consumer IoT devices sometimes needs your phone’s SSID passphrase to setup, DPSK can cause complications. You might also run into the rare device that is buggy and has issues with a DPSK SSID. Stick with standard pre-shared keys on your SSIDs for maximum compatibility is a residential setting.
Wi-Fi Band Use Cases
2.4 GHz: This band should only be used for IoT type of devices. This can include smart speakers, smart home sensors (e.g. garage door opener, presence sensors, thermostats, etc.) and cameras. Think relatively low bandwidth smart devices. You can also try streaming devices, such as Roku or Apple TV. But personally I put them on my 5/6 GHz network if they aren’t hard wired with Ethernet. The 2.4 GHz network will also be WPA2, so it is a good fallback for devices that don’t yet support WPA3 (which is required on the 5/6 GHz SSID).
5 GHz: This band is pretty widely supported among more advanced modern clients, such as phones, laptops, tablets, watches, and even some cutting edge cameras. This band should be used for your primary high bandwidth devices. 5 GHz supports a variety of security modes, including WPA2 and WPA3. Because guest device compatibility can be a crap shoot, I suggest using WPA2 for all guest networks. For added security if you know all of your 5 GHz devices support WPA3, go ahead and use WPA3 only.
6 GHz: The 6 GHz Wi-Fi band is pretty new, and many client devices do not yet support it. The very latest phones and laptops probably support 6 GHz (via Wi-Fi 6E or Wi-Fi 7). All certified 6 GHz devices require the use of WPA3 on the 6 GHz band. WPA2 and open networks are not allowed. Due to relatively limited client device support, and the great speeds you can get on 5 GHz, I would suggest limiting the 6 GHz band to only homeowner SSIDs. If you combined the 5/6 GHz bands on a single guest SSID, that would require all guest clients using that SSID to support WPA3, which may not always be the case.
Wi-Fi Calling
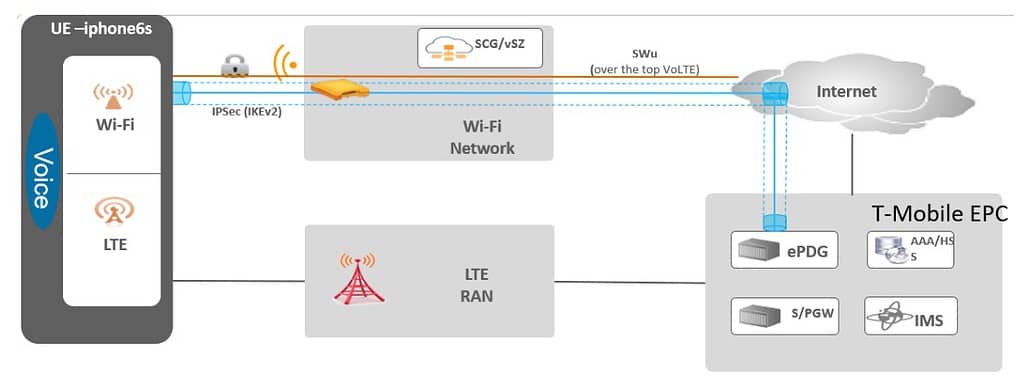
Wi-Fi calling is a service that allows you to make and receive calls over a Wi-Fi network instead of using your phone’s cellular network. This service relies on Voice over Internet Protocol (VoIP) technology to transmit voice calls as data over the internet. Wi-Fi calling uses ePDGs, which are manually defined in Ruckus One.
An Evolved Packet Data Gateway (ePDG) is a critical component in the network function of the 4G (and above) mobile core networks, known as the Evolved Packet Core (EPC). The ePDG helps mobile network operators control their user’s mobile experience, particularly in the context of WiFi calling and similar services. For US carriers setup the applicable ePDGs for ATT, T-Moble, and Verizon. I suggest setting up all three, even if you only subscribe to one carrier. If you reside outside of the US, lookup the ePDG FQDNs for the carriers in your country/region.
Enabling Wi-Fi calling incurs no additional overhead, so there’s no reason to not enable it for all SSIDs. This can help cover a scenario where someone is accidentally on the 2.4 GHz network with their cell phone and makes a call.
For more details on Wi-Fi calling check out the Ruckus Wi-Fi Calling Best Practices Guide. In short, the Wi-Fi calling process is as follows:
- A client associated to the WLAN with the Wi-fi calling profile enabled initiates a Wi-Fi call
- Ruckus One QoS features identify this as a Wi-FI call and can sense the carrier requested.
- An IPSec tunnel to the ePDG is established.
- Carrier grade voice connection is established just as an LTE call would be.
Ruckus Unleashed now includes pre-configured ePDGs for the US market. This means you no longer need to add any ePDGs if you live in the US. If you live outside of the US you will need to find the applicable ePDGs to your country and input them.
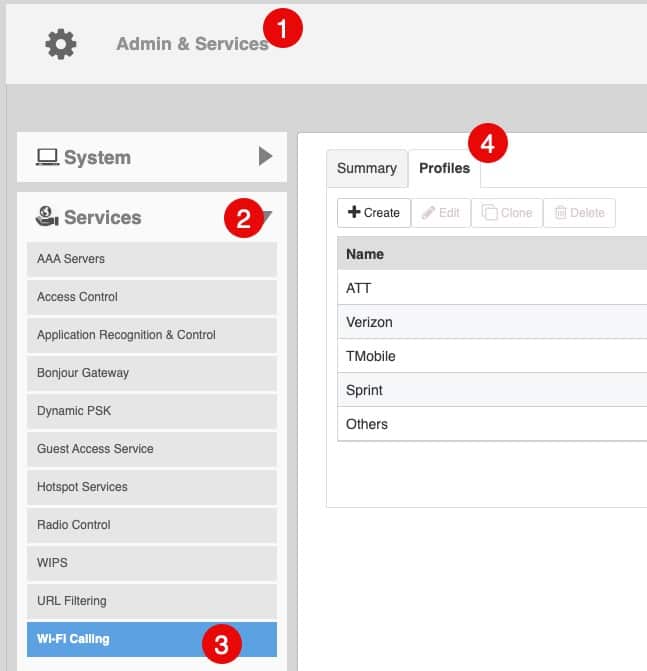
You can find the Wi-Fi Calling profiles at Admin & Services -> Services -> Wi-Fi Calling -> Profiles.
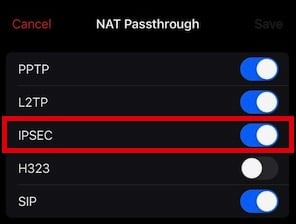
Firewall IPSec Passthrough
If your router/firewall has an IPsec pass-through option, I recommend turning it on for Wi-Fi calling. For Firewalla firewalls, go to Network -> NAT Settings -> NAT Passthrough -> IPSec (turn on).
2.4 GHz Radio Configuration
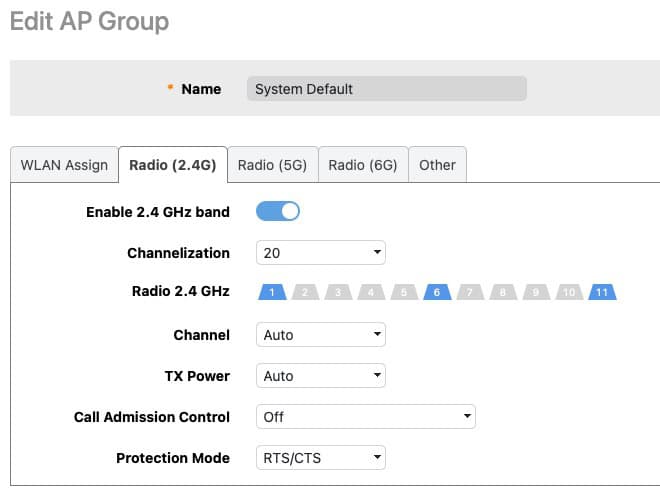
- Go to Access Points -> Summary -> Edit -> Radio (2.4G).
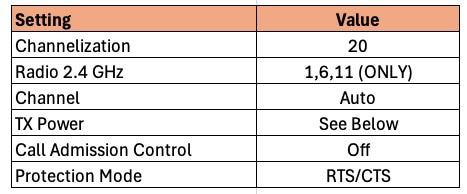
Channelization: For 2.4 GHz you should be using 20 MHz channel width 100% of the time. Due to the very limited number of channels, i.e. radio spectrum, going wider is just asking for trouble. Wider channel width also increases the channel noise, which can reduce performance near the edge of the AP’s coverage. 2.4 GHz devices should not be your high bandwidth devices like laptops or cell phones. 2.4 GHz is for your IoT/smart home devices which are low bandwidth. Think smart light switches, doorbells, presence sensors, smart outlets, smart speaker, etc.
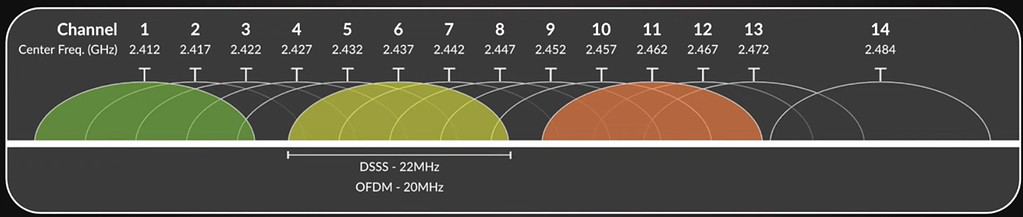
Radio 2.4 GHz: The channels available to you will vary somewhat depending on the region of the world you live in. For example, in the US the graphic below shows what channels are available. Japan, for example, adds channel 14. However, for the vast majority of the world the only non-overlapping channels that you should be using are 1, 6 and 11. Using ONLY these channels, combined with the 20 MHz bandwidth, reduces the chances of interference and will maximize performance. See the graphic below for a visualization of the 2.4 GHz channels.
Channel: We want the APs to auto-select the channel it uses, so set this to auto.
TX Power: Depending on how many APs you have in your home, you may need to adjust the TX power. For a home with a single AP transmitting at full power is probably just fine, which can help eliminate dead zones. However, if you are deploying multiple APs then transmitting at full power on all APs is probably NOT ideal and choosing AUTO here is a bad idea.
For a better roaming experience in your home it is better to reduce the transmit power for 2.4 GHz. How much you need to reduce transmit power will vary house to house and depends on a number of factors like how many APs you have, square footage you need to cover, building materials, etc. I would try values ranging from -3dB to -8dB, and use the lowest transmit power you can which provides good coverage. Monitor the RSSI values on clients to gauge how much you can reduce power. RSSI values of -67 to -77 is a good signal strength.
Call Admission Control: In a residential environment we don’t need to use the call admission control settings. Turn off.
Protection Mode: Leave the default of RTS/CTS.
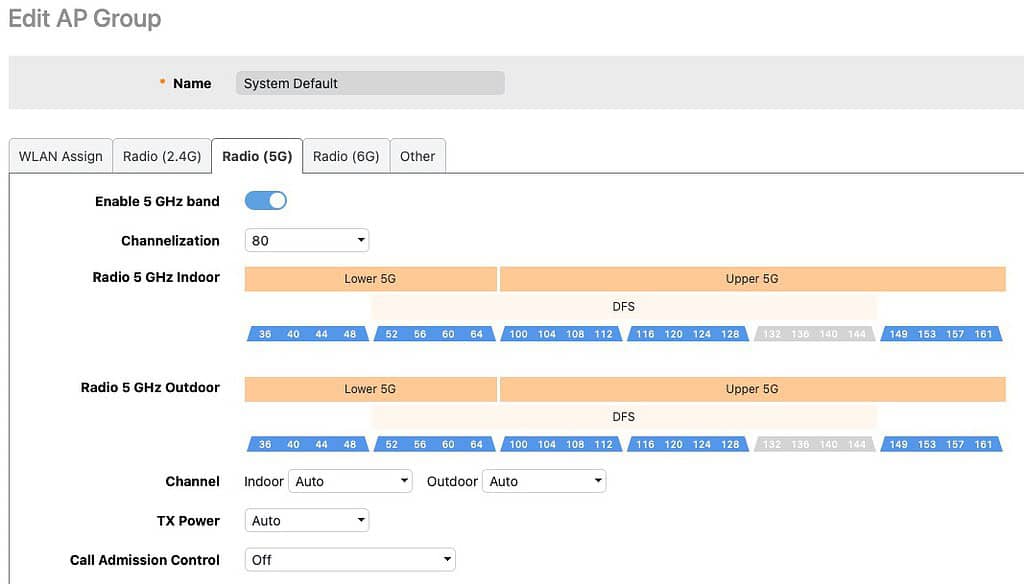
5 GHz Radio Configuration
- Go to Access Points -> Summary -> Edit -> Radio (5G).
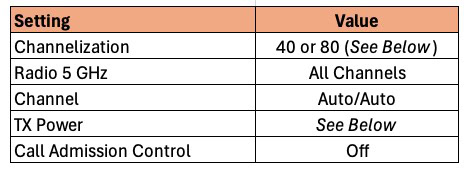
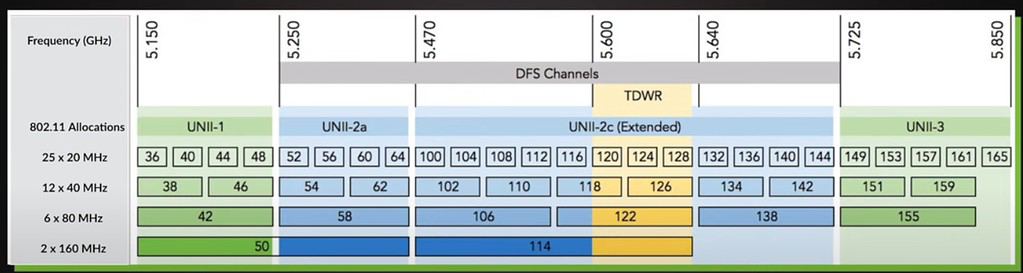
Channelization: This value will depend on your environment and the region of the world you are in. Remember that the wider the channel the higher the noise on the channel, which can reduce performance near the edge of the range of the AP. However, wider bandwidth can improve Wi-Fi speeds. In the US 80 MHz is a good starting point, as many consumer grade Wi-Fi APs don’t even allow you to use DFS (UNII-2) channels (see graphic below). This gives enterprise grade APs, like Ruckus, four more 80 MHz channels to use, which likely have little neighbor interference. 160 MHz on the 5 GHz band is probably overkill, and may not even be supported by some clients. If you live in high density urban areas with limited channels, like much of Europe, 40 MHz is probably a safer choice.
Radio 5 GHz: The channels available to you will vary depending on the region of the world you live in. For example, in the US the graphic below shows what channels are available. Depending on your proximity to radar, the DFS channels may or may not be usable. And some client devices might not like certain DFS channels, like 144. My personal philosophy for 5 GHz (located in the US) is to use all channels. Modify as needed for your environment and clients. As previously mentioned, many consumer/ISP grade Wi-Fi APs in the US can’t use the DFS channels (52-144). So in your environment those channels may have little to no interference from neighbors. See the graphic below for a visualization of the 5 GHz channels.
Tip: Some badly designed devices may not deal with DFS channels. For example, old Amazon Fire TV devices did not support channels 52-144. If you have old devices that don’t like DFS channels you can 1) Upgrade the device 2) Disable the DFS channels (52-144). If you need to disable any DFS channels, you can do it here.
Channel: We want the APs to auto-select the channels it uses, so set this to auto for both indoor and outdoor.
TX Power: In a residential environment transmitting at full power on 5 GHz is not always ideal. However, without an accurate predictive Wi-Fi model of your house, it’s anyone’s guess on what transmit power is ideal. If you have a single AP in your home I would not reduce the 5 GHz TX power. You want the best coverage possible. However, if you have multiple APs in your home it might be better to reduce the transmit power for 5 GHz. Why? Reduced power can help nudge your clients to roam better between APs and be less “sticky”.
Remember that 5 GHz has shorter range (more attenuation) than 2.4 GHz. So if you do adjust transmit power, you will not need to dial it down as much as 2.4 GHz for optimal roaming. Also, remember you want a stronger 5 GHz signal than 2.4 GHz, which is another reason why you should be more cautious in reducing 5 GHz transmit power in a residential setting. Remember though, always use the lowest power settings that you can while still maintaining good coverage and strong client performance.
Call Admission Control: In a residential environment we don’t need to use the call admission control settings. Turn off.
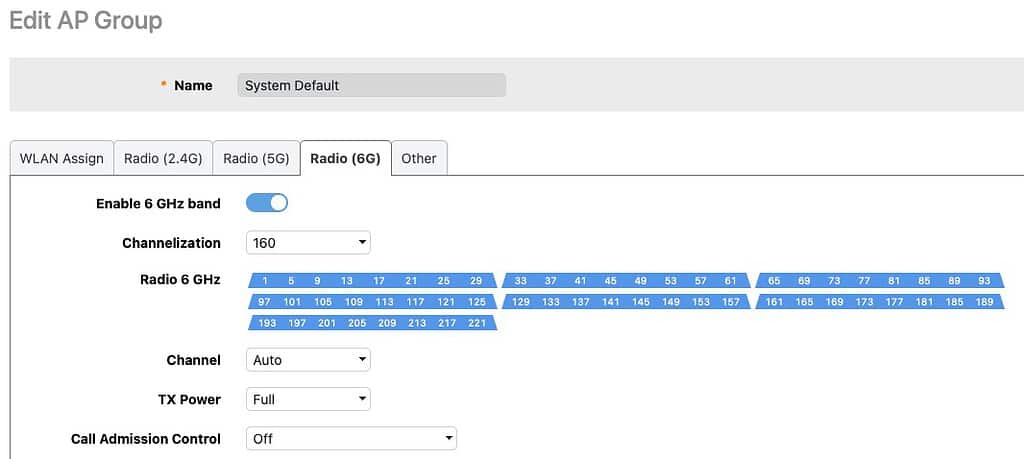
6 GHz Radio Configuration
- Go to Access Points -> Summary -> Edit -> Radio (6G).
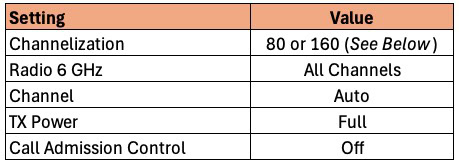
Channelization: This value will depend on your environment and the region of the world you are in. Remember that the wider the channel the higher the noise on the channel, which can reduce performance near the edge of the range of the AP. However, wider bandwidth can improve Wi-Fi speeds. In the US 160 MHz is a good starting point as we have a lot of spectrum and probably little neighbor interference. If you live in high density urban areas with limited channels, like much of Europe, 80 MHz is probably a safer choice.
Radio 6 GHz: The channels available to you will vary depending on the region of the world you live in. Unlike the 5 GHz band, there are no DFS channels. I suggest using all channels available in your region.
Channel: We want the APs to auto-select the channels it uses, so set this to auto for both indoor and outdoor.
TX Power: 6 GHz frequencies attenuate much more than 5 GHz and 2.4 GHz bands. As a starting point I would suggest full power for maximum range.
Call Admission Control: In a residential environment we don’t need to use the call admission control settings. Turn off.
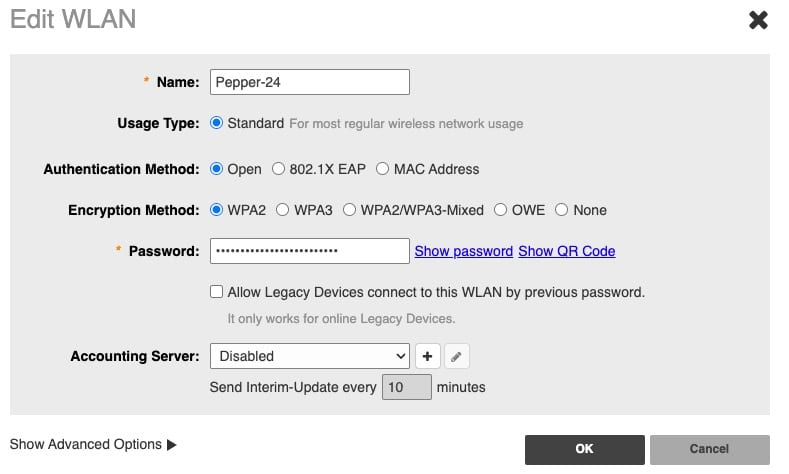
Wi-Fi Networks: WLAN Details
For the remainder of this guide I recommend going through all the settings for a single SSID, then come back and repeat for the remaining SSIDs. If you follow my SSID architecture you will end up with three (or four) SSIDs with different settings.
Note: If there’s any lingering default WLANs, delete them. Simply to go Wi-Fi Networks -> Click SSID -> More -> Delete.
To add a new wireless network in Ruckus Unleashed:
- Go to Wi-Fi Networks -> Create.
2. Walk through each section below to setup the various parameters for each SSID.
Network Name/SSID: Select your SSID name. I like to denote which frequency band and purpose of the SSID (e.g. Pepper-24, Pepper-56, Pepper-24-guest, Pepper-5-guest).
Usage Type: All networks should use standard.
Authentication Method: We are not using any enterprise authentication options, so pick Open.
Encryption Method: Use WPA2 for all 2.4 GHz WLANs. Use WPA3 on 5/6 GHz bands for increased security. Do not use WPA3 on your 2.4 GHz IoT network as most IoT devices will not be able to authenticate. 6 GHz requires WPA3.
Password: I would urge a minimum of 16 characters (Upper case, lower case, number, special character), with longer being more secure. Personally I always use 24 characters or more. I also use a passphrase, which is easier to type (e.g. MaryHadALittle@lamb60602).
Accounting Server: This is not needed in a residential environment.
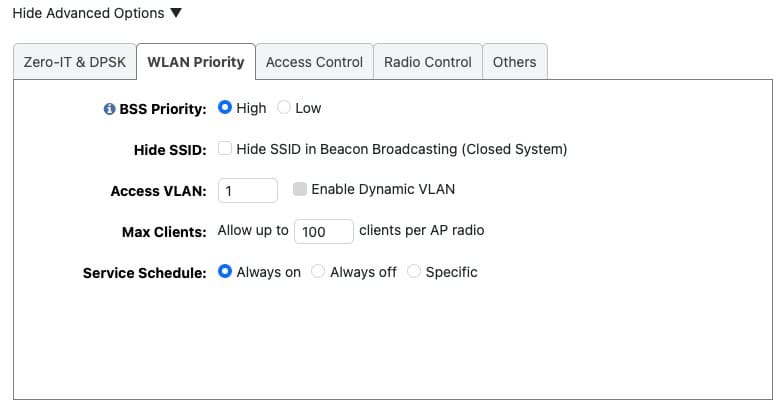
Wi-Fi Networks: WLAN Priority
3. Click on Show advanced settings at the bottom of the above window and go to the WLAN Priority tab.
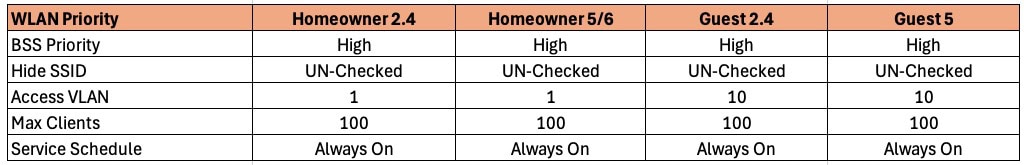
Priority: Leave this set to High for all WLANs.
Hide SSID: Leave your SSID visible. Hiding an SSID is not a security feature and is actually LESS secure. An attacker can still easily find your SSID.
Access VLAN: For the Home owner network use VLAN 1. If you are separating guest traffic to an isolated VLAN, use that VLAN ID for the guest networks. I used 10 in my example.
Max Clients: Leave the default of 100.
Service Schedule: Set to Always on.
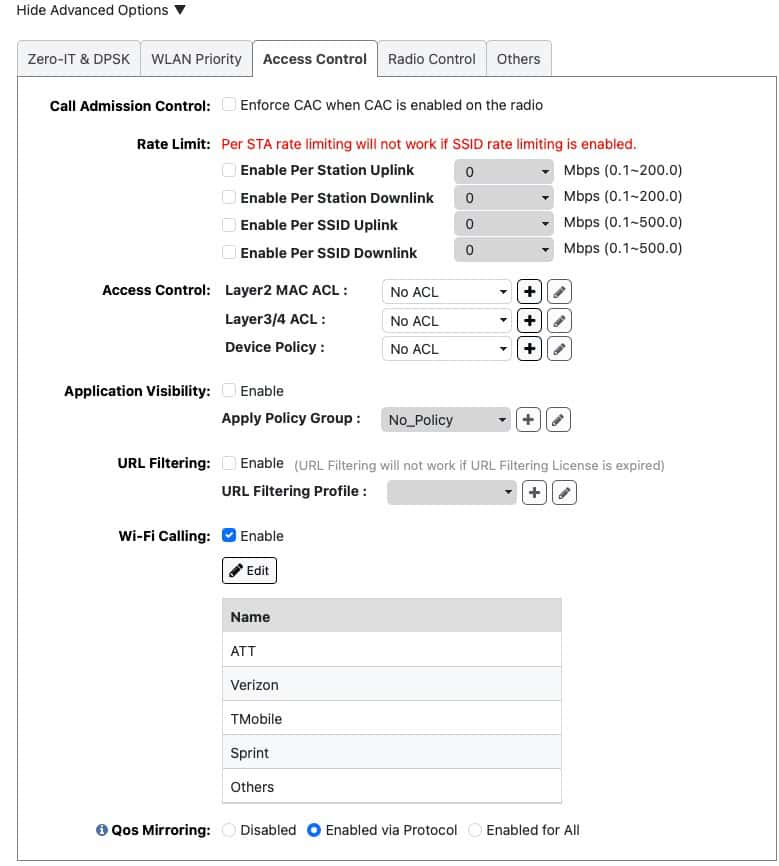
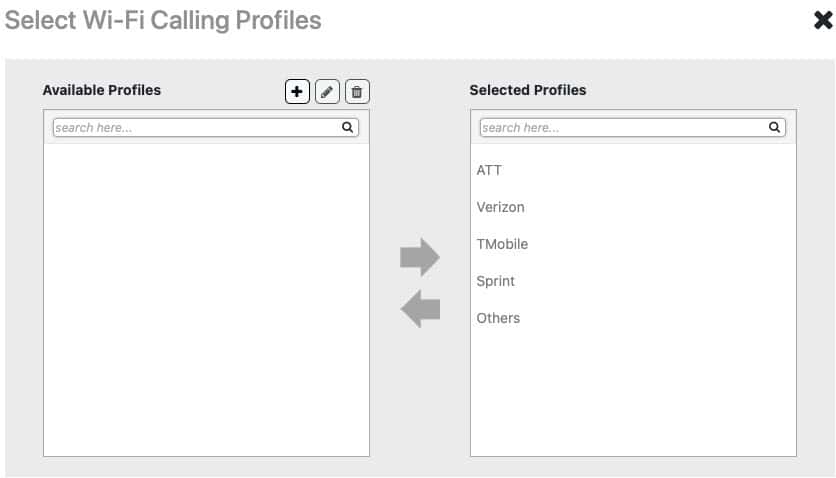
Wi-Fi Networks: Access Control
1. Click on the Access Control tab.
2. Click on the Edit button next to Wi-Fi Calling. If you live in the US, add all the profiles to the right column. If you live in another region click on the plus and add your ePDGs for your cellular carriers.
3. Leave all other settings on this page their default value.
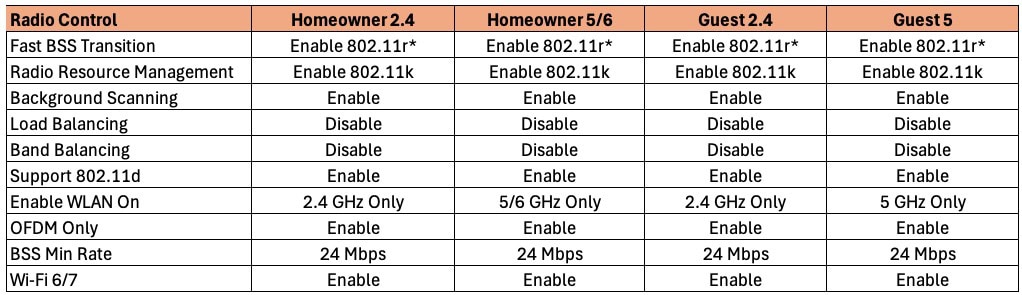
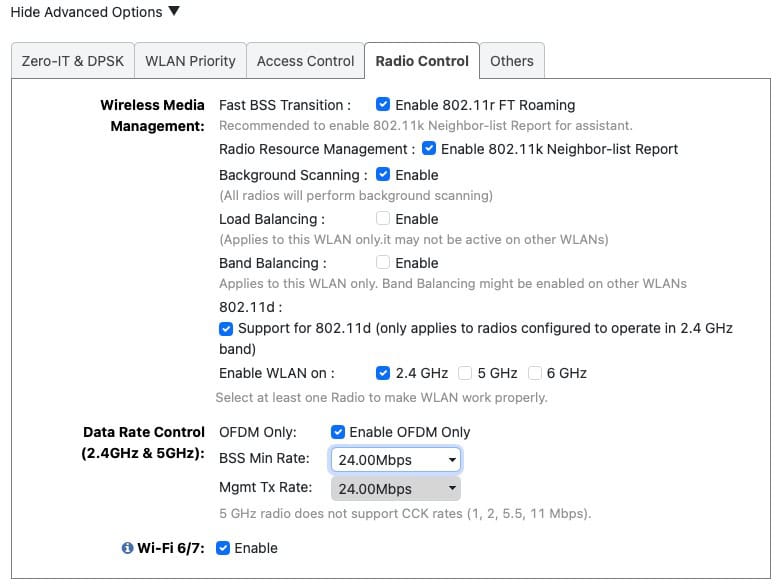
Wi-Fi Networks: Radio Control
1. Click on the Radio Control tab. Depending on the SSID you are configuring, select the appropriate options.
Fast BSS Transition: It is recommended to enable 802.11r. Only if you run into compatibility issues should you disable 802.11r.
Tip: Some HP printers, cameras, Ring doorbells/chimes, and other devices may not like 802.11r turned on. The primary symptom I’ve personally seen is that a device is not able to join the SSID. If you run into these issues and don’t want to replace the broken device, try disabling 802.11r.
Radio Resource Management: Enable 802.11k. Very important to enable so that clients can easily find all bands the AP is broadcasting on. This accelerates some devices discovering which 6 GHz channels are in use. Turn on.
Background Scanning: Set to Enable.
Load Balancing: Can cause issues in a residential setting. Disable.
Band Balancing: Can cause issues in a residential setting. Disable.
802.11d: Adds country information to elements, and allows a device to comply with country regulations. Turn on.
Enable WLAN On: Select the appropriate band for each SSID.
OFDM Only: You can safely enable this unless you know you have a client that only supports 802.11b (extremely ancient Wi-Fi standard). If you have 802.11b only devices, turn this off. OFDM has higher spectral efficiency and is more resistant to noise. Consider replacing any legacy 802.11b only devices so you can enable this setting.
BSS Min Rate: A minimum of 12 is strongly suggested, with 24 Mbps being even better. This encourages clients to roam when the signal is poor.
Wi-Fi 6/7: Enable this as we want the best client experience.
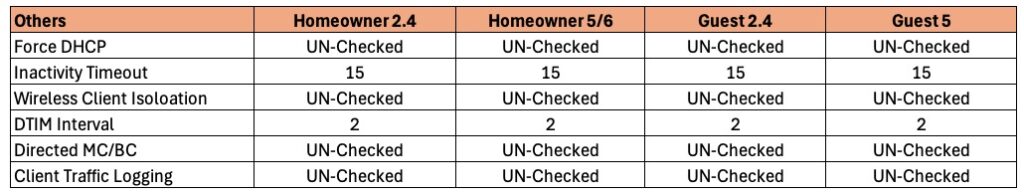
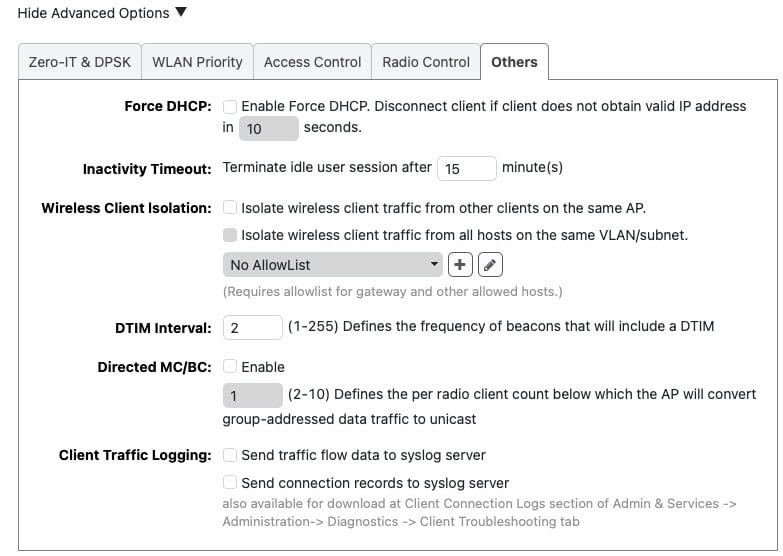
Wi-Fi Networks: Others
1. Click on the Others tab. Note that all SSIDs use the same settings.
Force DHCP: Not recommended in a residential environment.
Inactivity Timeout: I find that 15 minutes is a good compromise for my smart home and detecting when my phone is no longer connected to Wi-Fi.
Wireless Client Isolation: Not recommended in a residential environment.
DTIM Interval: DTIM (Delivery Traffic Indication Message) Interval is a concept in Wi-Fi communication that relates to power saving. If the DTIM interval is 2, the AP will send out broadcast/multicast data every 2 beacon frames. Start with a value of 2, but sometimes 3 can work as well.
Directed MC/BC: This must be UN-checked so that it is disabled. This enables multicast services/devices like Sonos, Airplay, Matter, etc. to work as expected. Enabling this is asking for problems in a residential setting.
Client Traffic Logging: Not recommended in a residential environment unless you have a specific need to log traffic to a syslog server.
Adding more Access Points
Now that you have fully configured Unleashed, it’s time to add more access points. One cool aspect of Unleashed is that access points with the Unleashed Firmware will automatically discover each other and configure themselves.
So now that you have a single AP running with Unleashed, just sequentially power on your other APs. If they have the Unleashed firmware then they will auto-discover your master AP and configure themselves using the configuration you defined. Give the APs quite a few minutes to reconfigure themselves after you power them on. Once your next AP is configured and in production, power on your next AP and repeat until all APs are up.
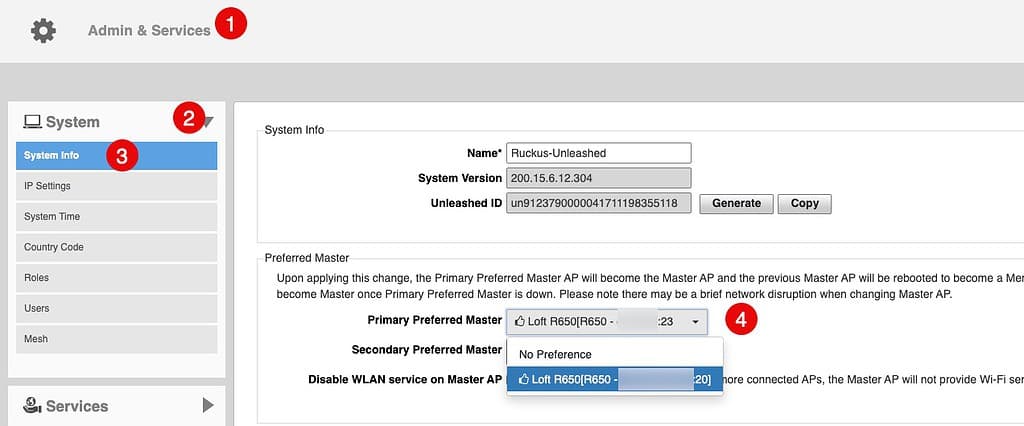
Setting Preferred Master AP
If you have more than one AP in your environment then you can make one AP a preferred Master. This is not required, but in larger environments can be helpful. If you want to make a preferred master I suggest using the AP which has the lightest load. You can also setup a secondary preferred master as well, if you wish.
Troubleshooting
If you followed this guide to the letter, it should set you up for a solid Wi-Fi network. However, not all clients are created equal and some have broken firmware. Generally these symptoms manifest themselves by a client not being able to join the SSID. If you have weird issues try the following:
- If a client has trouble joining a SSID, disable 802.11r then re-attempt the client join.
- If you are trying to join a device to the 5 GHz SSID and it’s not working, disable the DFS channels and try again.
- Some client devices are OK with most DFS channels but break on 144. If you run into client issues, check which 5 GHz channel(s) your APs are using. Try disabling 5 GHz channel 144 if that appears to be causing a problem.
- If a device can’t join the 5 GHz network, try it on the 2.4 GHz network.
- If you have particularly brain dead clients that don’t like channel changes, you may need to hard code the channels the APs use. You can use a program like Wi-Fi explorer to look at the RF neighborhood around you to see what channels are currently in use. But RF environments can be very dynamic, so be careful.
- If you are stumped with issues, check out the Ruckus Unleashed Forums.
Summary
In this two part series I covered the best practices for configuring Ruckus Unleashed in a residential environment. In the first part we covered flashing to Unleashed and a number of system-level settings. In part two we covered a lot of ground including multiple SSIDs, Wi-Fi calling, a bit about 6 GHz, and more.
This guide should give anyone using Ruckus APs a great start in setting up their residential configuration. Ruckus APs are true enterprise class access points which will provide rock solid and performant Wi-Fi in any environment.






Thank you!