In today’s interconnected world, safeguarding your personal information is more crucial than ever. With telecommunications companies collecting extensive data about your communication habits, it’s essential to understand how this information is used and how you can protect your privacy. From disabling Customer Proprietary Network Information (CPNI) to securing your Social Security Number and managing your credit, there are numerous strategies to enhance your digital security.
This guide delves into practical steps you can take to control your data, prevent unauthorized access, and maintain your privacy across various platforms. Whether you’re concerned about targeted advertising, data breaches, or identity theft, this guide provides the insights you need to navigate the digital landscape with confidence.
Everyone is Collecting Data on You
The declassified ODNI (Office of the Director of National Intelligence) report on Commercially Available Information (CAI) outlines the increasing availability and use of CAI, which includes data that can be purchased by the Intelligence Community (IC) for intelligence purposes. This data, often gathered from digital sources like smartphones and online activities, can be re-identified to reveal detailed personal information. While the report primarily deals with the IC’s use of such data, it highlights a broader concern about how easily accessible personal data is and the potential implications for individual privacy.
The ODNI report underscores the importance of maintaining a small digital footprint. As data aggregation by brokers can lead to comprehensive profiles, consumers should be vigilant about the information they share online. Reducing unnecessary data sharing and being aware of privacy settings can help protect personal information from being misused. Controlling your digital presence is key for safeguarding your privacy and minimizing exposure to data breaches and targeted advertising.
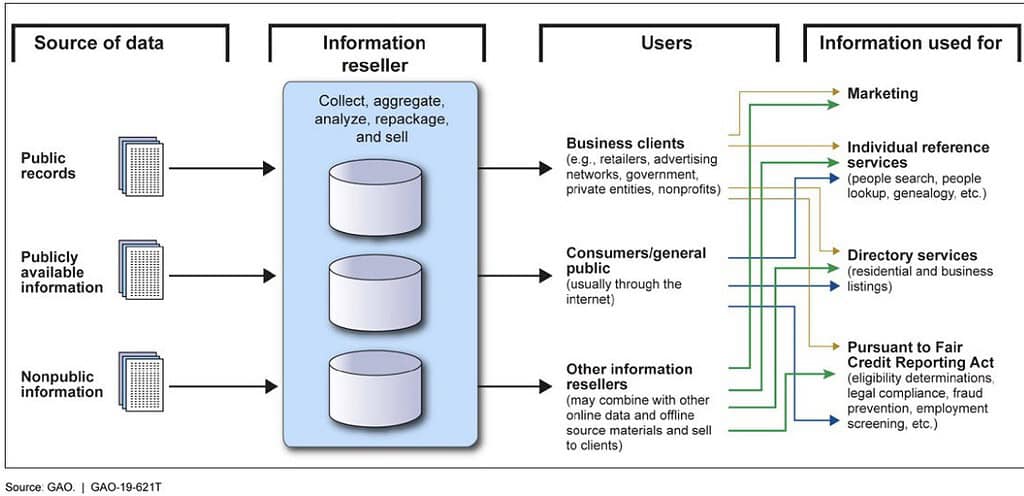
Data brokers collect data from commercial, government, and other publicly available sources. Data collected could include bankruptcy information, voting registration, consumer purchase data, web browsing activities, warranty registrations, and other details of consumers’ everyday interactions. Data brokers do not obtain this data directly from consumers, and consumers are thus largely unaware that data brokers are collecting and using this information. While each data broker source may provide only a few data elements about a consumer’s activities, data brokers can put all of these data elements together to form a more detailed composite of the consumer’s life.
The figure below is from the ODNI report and illustrates how multiple sources of data are combined through data brokers and ultimately used for marketing, directory services, people lookup sites, and more.
Telecomm Privacy Dirty Secrets
Telecommunications privacy is important, as much of your internet traffic will flow through a telecomm provider…be it your home ISP or your cellular provider. However, there’s a dirty secret of the telecomm industry that can deeply invade your privacy. It’s the CPNI.
CPNI stands for Customer Proprietary Network Information. It refers to the data collected by telecommunications companies about a consumer’s telephone calls and internet usage. This information includes details such as the time, date, duration, and destination of each call, as well as the type of network services the customer uses and any billing information. They can also track internet traffic, sites you go to, etc.
Reasons to disable CPNI for privacy:
- Protection of Personal Data: CPNI contains sensitive information about your communication habits and patterns. Disabling it can help protect your personal data from being accessed or misused by unauthorized parties.
- Prevent Targeted Advertising: Telecommunications companies can use CPNI to create detailed profiles of your usage patterns and preferences, which can then be used for targeted advertising. Disabling CPNI can help reduce the amount of targeted marketing you receive. Note that not all telcos use sell CPNI data to marketing firms.
- Reduce Risk of Data Breaches: By limiting the amount of data stored and shared by your telecom provider, you reduce the risk of your information being compromised in the event of a data breach.
- Enhance Control Over Personal Information: Disabling CPNI can give you more control over who has access to your personal information and how it is used.
CPNI Opt-Out
I would strongly suggest opting out of CPNI for both your home ISP and cellular provider. However, locating the opt-out instructions for your provider may be challenging. The fastest way is probably to just use this phrase:
Search term: “<provider name> CPNI opt out”
Example: Verizon CPNI opt out. Follow the instructions that you find. ATT is a bit slimy and doesn’t have CPNI settings in their normal privacy settings panel. You have to use google search to find a dedicated CPNI opt-out page, which I find to be just gross.
Protecting your Social Security Number
Unfortunately, there isn’t a single method to block or freeze access to data linked to your Social Security Number. To comprehensively restrict access to PII associated with your Social Security Number, you should consider freezing or locking “The Work Number,” E-Verify, the Social Security Administration, and the credit bureaus. Each of these protections is detailed below.
'The Work Number' Freeze
The Equifax “The Work Number” portal is an employment and income verification service that automates the verification process for employers, employees, and verifiers. Managed by Equifax Workforce Solutions, it reduces administrative burdens for employers and provides employees with secure access to their data for personal use or applications.
The Work Number may contain salary information from current or previous employers. However, customers of The Work Number will not have access to salary details unless you are notified and follow their PIN authorization procedure. The database is mostly comprised of current or past employers you have worked for and employment dates.
Freezing your Work Number records, IMHO, is not worth it as the sensitivity of the data is low. Plus, a frozen account may hinder future employment background checks, Government services, or other services. If you live in a state with stricter privacy laws you may be able to contact The Work Numbers and ask what data they have on you so you can decide if you want to freeze it or not.
If you are super paranoid and want to freeze access to your Work Number records, you can find the procedure on Equifax’s website. Note that not all companies submit data for their employees, so you might not have a record in their system.
My E-Verify Lock
The E-Verify lock feature is a security measure that allows individuals to protect their Social Security Number (SSN) from being misused in the E-Verify system, which is used by employers to confirm the employment eligibility of new hires. By activating the lock, individuals can prevent unauthorized or fraudulent use of their SSN in E-Verify, ensuring that only legitimate employment verifications are processed. This feature enhances personal data security and helps safeguard against identity theft and employment fraud.
To initiate an E-Verify lock, go to the E-Verify.gov site and discover how to use the self locking feature. It takes just a few minutes to create an account, and online verification was flawless for me.
Social Security Number Locking
Restricting electronic access to your Social Security Number (SSN) ensures that neither you nor anyone else can access or alter your personal information with the Social Security Administration (SSA) online or via their automated phone service. To request this block, you can call the SSA at 1-800-772-1213. If you decide to lift the block in the future, you will need to call again and verify your identity.
This is separate from the credit bureau freeze (covered next) at credit bureaus. Locking your SSN is an action the Social Security Administration takes, not a private company. Freezing the credit bureaus takes additional work on your part.
Credit Bureau Freeze
Freezing your credit is a powerful step to protect yourself from identity theft and unauthorized credit activity. Here’s how you can freeze your credit at each of the three major U.S. credit bureaus:
- Equifax: Visit the Equifax website or call their automated line at 1-800-349-9960. You’ll need to provide personal information, such as your Social Security number, to verify your identity. Once verified, you can request a credit freeze, which Equifax will implement immediately.
- Experian: Go to the Experian Freeze Center online or call 1-888-397-3742. You will need to create an account or log in if you already have one. After verification, you can place a freeze on your credit, which will take effect right away.
- TransUnion: Access the TransUnion website or call their customer service at 1-888-909-8872. You’ll be asked to provide identification details, and once confirmed, you can initiate a credit freeze. TransUnion will process your request promptly.
Freezing your credit at all three bureaus ensures comprehensive protection against unauthorized access to your credit report. Remember, you can lift the freeze temporarily or permanently whenever you need to apply for credit.
Protecting your E-Mail
One common method data brokers use to link pieces of data together is through email addresses. Your email address is likely present in numerous databases, whether from sites where you have accounts or through data brokers. To help prevent data brokers from linking your information and to reduce spam, using email aliases is an effective strategy.
Over two years ago, I started a project to protect a new email address from spam, sharing it only with close friends and family. For all other sites, I utilized site-specific email aliases with a custom domain that I own.
I won’t go into depth here, but check out my article titled Email aliases: How to easily protect your inbox from spam for my methodology. I now have over 900 unique email aliases and my primary email address hasn’t gotten a single piece of spam in years.
Tip: To fully protect your primary email address, make sure you are utilizing all available account security controls. This includes using Passkeys if they are available, opting for password-less login options like those offered by Microsoft, and enabling two-factor authentication. Also make sure your password is unique to your email account, super long, and very complex. Use a password manager like 1Password to store the password, not your brain.
Securing your primary email account is crucial because if it gets compromised, it could lead to a cascade of unauthorized password resets across many other sites, potentially giving a bad actor access to your accounts, bank accounts, investment accounts and more.
Protecting your Phone Number
One key piece of PII that is often overlooked is your phone number. Data brokers can use your phone number to link various pieces of data about you, creating a comprehensive profile that can be sold to marketers or other entities. Additionally, spammers are constantly on the hunt for phone numbers to target with endless calls and messages. Changing your primary phone number can be challenging, especially as more websites use it as a means of authentication through verification codes.
The Case for a Secondary Number
To mitigate the risk of spam and maintain your privacy, consider using a secondary phone number for less important interactions online. This approach allows you to keep your primary number private while still engaging with various services. A practical and cost-effective solution is to obtain a Google Voice number, which can handle calls and SMS messages. However, keep in mind that some websites may not accept Voice over IP (VoIP) numbers for authentication purposes.
An Alternative Solution: eSIMs
For those looking for a more robust solution, acquiring a secondary eSIM for your phone can be a worthwhile investment. Services like US Mobile, Telo and Helium offer low-cost, low-data plans for as little as $6 per month. These “light” lines can be used for ALL sites that require a phone number for authentication. This method also simplifies the process of receiving authentication codes directly on your phone without needing to access a separate app like Google Voice.
Best Practices for Phone Number Usage
When it comes to using your phone number online, it’s crucial to be selective. For businesses and institutions you trust, such as your bank or government services, continue using your primary phone number. This minimizes the risk of your main number being exposed online. If your secondary number is compromised, it’s easier and less disruptive to cancel it and obtain a new one.
Do Not Call Registry
Unsolicited phone calls are a constant nuisance, interrupting your day and invading your privacy. Whether from persistent telemarketers or potential scams, these calls can quickly become overwhelming. The Do Not Call Registry in the United States offers an effective solution.
By registering your phone number, you can significantly reduce spam calls and reclaim your peace. This free service empowers you to take control of your phone line and protect your personal space from unwanted intrusions. You can quickly place all of your phone numbers on the Do Not Call Registry with just a few clicks: National Do Not Call Registry.
Tip: If you get a secondary eSIM for your phone, don’t forget to register this number with the DNCR.
SIM Swap and Port Out Protection
Cellular SIM swap protection is crucial for the privacy and security of your phone number because it helps prevent unauthorized access to your mobile account. As of July 2024 the FCC has mandated that all US carriers offer enhanced SIM swap protection and port-out security. The mandate applies to both post-paid and pre-paid accounts.
SIM swapping is a tactic used by cybercriminals to hijack your phone number by transferring it to a new SIM card (or eSIM), allowing them to intercept calls and texts, including two-factor authentication codes. This can lead to unauthorized access to your online accounts, identity theft, and financial fraud.
Port-out fraud is a type of identity theft where a scammer hijacks your mobile phone number by transferring it to a different carrier. This process, known as “porting out,” was originally designed to allow consumers to switch service providers while keeping their existing phone numbers. While convenient for legitimate users, this process can be exploited by fraudsters.
By enabling SIM swap and port-out protection offered by your mobile carrier, such as requiring a PIN or password for SIM changes, you can safeguard your phone number and protect your personal and financial information from potential threats. SIM swap protections vary by cellular provider, so check with your carrier to see what protections they may offer.
The industry has not standardized on what these protections are called, but you can look for the following terms. Note that SIM swap and port-out protection can be decoupled and you may need to request both.
- Never SIM swap
- No Port Out
- Account Lockdown
- Number lock
- SIM protection
- Wireless account lock
- Port out protection
- Number Lock
- Account lock
Account Security
Just like your email account, obsessively protect your cellular provider account credentials. Use a password manager, use a unique and very long/complex password, enable 2FA if available, and enable any available account security alerts.
Protecting Your Finances
Protecting your credit card details is more crucial than ever. With credit card fraud on the rise, the likelihood of becoming a victim is significant, making it essential to take proactive steps to safeguard your financial information. As online transactions increase, cybercriminals find more opportunities to exploit vulnerabilities and access your credit card data. Digital wallets and virtual credit card numbers are effective ways to help mitigate credit card fraud.
Digital Wallets
Digital wallets, such as Apple Pay, offer another layer of privacy protection by masking your real credit card details. When you use a digital wallet, your actual card number is never shared with merchants. Instead, a unique device account number is used to process transactions, ensuring that your sensitive information is not exposed. This tokenization process not only safeguards your financial data from potential breaches but also simplifies the checkout process, making it more secure and convenient. The tokenization process also helps anonymize your transaction, making it much harder for the store and data brokers to link your purchase to a databroker profile.
Tip: When purchasing goods at a physical location always, always use your digital wallet (Apple Pay/Google Pay/Samsung Pay) for the highest level of transaction security and the most transaction privacy.
Virtual Credit Card Numbers
Using a virtual credit card service is an excellent way to enhance your privacy and security when making online purchases. Virtual credit cards generate temporary card numbers that you can use in place of your actual credit card number. This means that even if the virtual card details are compromised during a data breach, your real credit card information remains safe. Additionally, you can set spending limits and expiration dates for virtual cards, providing further control over your online transactions. This reduces the risk of unauthorized charges and makes it easier to manage your financial privacy.
Virtual Credit Card Services
Privacy.com offers virtual credit cards, with various plan options that range from free to paid. Some credit card issuers, like Capital One, also let you generate free on-demand virtual credit card numbers with various limits and expiration options. Privacy.com credit cards may also ignore physical billing details (like your home address), enabling you to use a fake address for situations where physical goods are not being shipped to your home. Perfect for any digital delivery service like streaming media.
Enabling Alerts
For each credit card you own, I highly recommend visiting your financial institution’s website to set up low-value threshold alerts for all new charges. For instance, configure alerts to notify you via text and email for any charge over $0.01. Criminals often perform small test transactions to verify if a card number is active before making a large purchase. By receiving alerts for these small transactions, you can potentially prevent larger fraudulent charges. This is also a great way to catch recurring transactions that should no longer be charged.
Privacy Opt-Out
Since you have ongoing relationships with your financial institutions, they potentially have a lot of data on you including credit card transactions and possibly even down to exactly what you purchased in a store (look up ‘level 3 credit card transaction data’). Even if you opted out years ago, there may be new opt-out options. I’d encourage you re-exercise all of your opt-out options.
Search term 1: “What does <company> do with your personal information.”
Search term 2: <company> “what does * do with your personal information”
Search term 3: <company> “to limit our sharing”
Search term 4: <company> “to limit direct marketing:
Tip: Some banks allow blanket opt-outs for all accounts in one go, while others require an account-by-account opt-out process. Pay attention to what your bank requires for full opt-out on all accounts.
General Data Collection Opt-Out Tips
For any company that you have an ongoing relationship with and you want to see what data privacy options they have you can use the following search terms to hopefully find their privacy policy and how to opt-out of data collection.
Search term 1 (US): <company> “your privacy choices”
Search term 2 (US): <company> “do not sell or share my personal information”
Search term 3 (US): <company> “limit the use of my sensitive personal information”
Search term 4 (US): <company> “right to opt-out”
Search term 5 (EU): <company> “object to processing”
Search term 6 (EU): <company> “right to object”
Search term 7: <company> “your choices and controls”
search term 8: <company> “opt out of the processing of”
Tip: Unless a company actually needs to know your physical address, consider using fake information. Obviously use common sense and use your real address with banks, Government, etc.
Google and Apple Maps Privacy
Both Google and Apple maps have the street level look around feature on their maps. Both Google and Apple try and blur some PII like faces and license plates automatically. However, there may be times where some PII has not be blurred by accident. I would suggest looking up your home address in both Google maps and Apple maps and check for any visible PII. If you find PII you can submit requests to both companies to have the offending data blurred. Regardless of which mobile platform you use, I would check both services for any offending PII.
Google Maps Blur Request Process
How to Blur Your House on Apple Maps (external blog post)
Real Estate Photos
Real estate websites have become a vital tool for buying and selling properties, often showcasing detailed interior photos to attract potential buyers. However, for some homeowners, these images can pose significant privacy and security concerns. Detailed interior photos can inadvertently reveal sensitive information about a home’s layout, security systems, or valuable possessions, making it easier for potential intruders to plan unlawful activities.
Additionally, these images can be used by strangers to gain insights into personal lifestyle and habits, which can lead to privacy invasions. As a result, some homeowners may choose to have these images removed from real estate sites to protect their privacy and maintain a sense of security.
To find sites which may have photos of your house I would first Google your address and see if sites like Zillow, Redfin, etc. have your house listed with any photos (even from previous owners). Some sites may require a single photo, so just leave an innocuous exterior photo.
Summary
In this blog post, I tackle a few important areas of privacy. One of these areas is opting out of Customer Proprietary Network Information (CPNI). I explain how telecom companies collect data on our communications, which can be used for targeted advertising and is vulnerable to breaches. Beyond CPNI, I explore broader privacy strategies, such as freezing credit to prevent identity theft, using email aliases to avoid spam, and securing your phone number against data brokers. My goal is to provide practical steps to help you take control of your digital privacy in our increasingly data-driven world.