Welcome to the 15-part VMware vCenter 5.1 U1 installation series! Given all of the new components and architecture of VMware vCenter 5.1, I wanted to walk through the entire installation of vCenter 5.1, assuming a greenfield environment. These instructions are assuming you are using vSphere 5.1 Update 1, which was released in April 2013. You can find more out about that release here.
vSphere 5.1 Update 1 installation is very different from the previous 5.0 and 4.x versions, so don’t think you can just click next and get a working and secure install. The GA 5.1 release of vCenter had a lot of, shall we say, bugs and issues related to the SSO service and SSL problems. 5.1.0b has addressed some of them, and now that we have vSphere 5.1 Update 1, even more issues have been resolved.
This 15-part series covers:
- Non-upgrade vCenter 5.1 Update 1 Installation on Windows Server 2012
- SSO service, Inventory Service, vCenter Server, vSphere client, vSphere Web client, and VUM
- Configure SSL certificates for all vSphere 5.1 services
- SQL SSL encryption for vCenter and VUM databases
SQL SSL encryption for the SSO database(Not working in Update 1)
Recently VMware has released their vCenter Certificate Automation Tool v1.0, which makes replacing the SSL certificates a bit easier. I’ve kept all of the manual instructions in this series, but I’ve updated some text to include references to the tool and will point out which sections you can skip should you want to use the tool.
SSL Certificates
I now recommend you install vCenter using self-signed certificates then use the vCenter Certificate Automation Tool to install your trusted certificates. You should always use trusted SSL certificates in your production environments. While the tool is not fully automated, it is easier than the manual steps or pre-staging. I wrote a complete how-to series on the tool you can find here, which you should follow after you get through the basic vCenter 5.1 installation process.
—
UPDATE 4/27/2013: Updating content to reflect vSphere 5.1 Update 1, and now officially supporting vCenter server on Windows server 2012 and SQL 2012 databases. I’ve also pulled the SQL SSL configuration, since I’m unable to get that working with Update 1 if the SQL server enforces encryption. Added references to the vCenter Certificate Automation tool which makes SSL certificate replacement a bit easier.
UPDATE 3/6/2013: There has been some discussion on what version of OpenSSL to use for vSphere 5.1. VMware states one should use 0.9.8. In OpenSSL 1.0 they changed the hashing algorithm, so you need to use a switch to produce the “legacy” hash of 0.9.8. -subject_hash_old is the switch you must use in OpenSSL 1.x. I get the same hashes with 0.9.8y, 1.0.1c, and 1.0.1e using that switch for the 1.x tree. In Part 3 under Update Trusted Certificate Store I show both command lines so you can produce the correct hashes. I recommend using 0.9.8, for full compatibility with the vCenter Certificate Automation tool.
UPDATE 2/17/2013: Added Part 15, replacing ESXi host SSL certificate. I also updated the Microsoft CA template creation instructions found here.
UPDATE 12/20/2012: VMware has released vCenter 5.1.0b, which addresses yet more installation bugs. I would advise skipping 5.1.0a, and go straight to 5.1.0b. You can find the 5.1.0b release notes here. I currently do not have time to update all the posts with 5.1.0b information.
—
This is the first post in a series of blog articles about configuring vSphere 5.1.0 Update 1. Links to the other parts are below:
Part 2 (Create vCenter SSL Certificate)
Part 3 (Install SSO Service SSL Certificate)
Part 4 (Install Inventory Service)
Part 5 (Install Inventory Service SSL Certificate)
Part 6 (Create vCenter and VUM Databases)
Part 7 (Install vCenter Server)
Part 8 (Install Web Client)
Part 9 (Optional SSO Configuration)
Part 10 (Create VUM DSN)
Part 11 (Install VUM)
Part 12 (VUM SSL Configuration)
Part 13 (VUM Configuration)
Part 14 (Web Client and Log Browser SSL)
Part 15 (ESXi Host SSL Certificate)
Note: You can skip parts 3, 5, 14 if you want to use the vCenter Certificate automation tool as mentioned above.
Related Posts:
VMware vCenter Certificate Automation Tool 1.0
Create VMware Microsoft CA certificate template
VMware vCenter 5.1 Installation: SSL Certificate Pre-Staging Script
SQL Server Pre-Reqs
With prior versions of vCenter one could easily configure their SQL server and ODBC connection to use SSL. This encrypted all communications between vCenter and the SQL server, which is a great best practice. However, in vCenter 5.1 the SSO service uses a JDBC connector, which I have not been able to reliably configure with SSL.
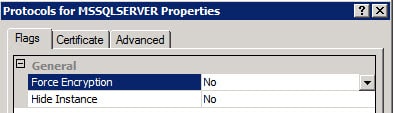
If your SQL server is forcing SQL SSL encryption, then you won’t get past the SSO installer as it will fail. You can validate your SQL server configuration by looking in the SQL Server Configuration Manager on your SQL server and reviewing the properties of the Protocols for MSSQLSERVER. As shown below, if Force Encryption is set to Yes you will need to change it to NO and restart the SQL services.
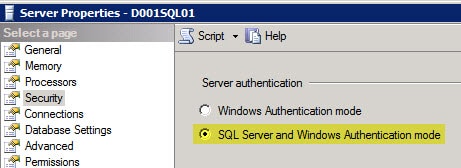
On another security note the SQL server MUST be configured to allow both Windows integrated authentication AND SQL authentication. SQL authentication is very weak, which makes the use of SSL for the database connection that much more imperative. Should the SQL server only allow Windows integrated authentication you will likely get the following error:
Error 29115.Cannot authenticate to DB.
Use SQL studio to login to your SQL server, open the server properties then use the less secure option of SQL Server and Windows Authentication mode. Restart the SQL services.
vCenter 5.1 Installation – VM Provisioning
1. Provision one or more VMs for the vCenter 5.1 install. In this blog series I’m assuming an all-in-one server to make things easier. You can certainly split up the services, which would be recommended in medium to large environments.
I provisioned a Windows Server 2012 VM (2008 R2 will work fine as well), with 2 HDs, and all of the latest Windows updates. 6GB of RAM and even 8GB of RAM for an all-in-one server is recommended, otherwise vCenter and SSO will run verrrrrrrry slowly. The 5.1 release has high memory utilization.
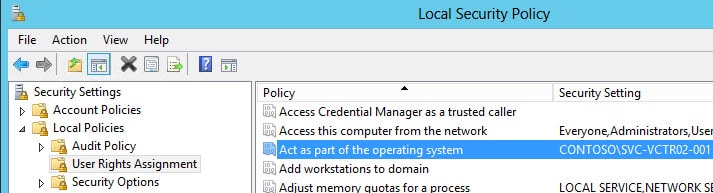
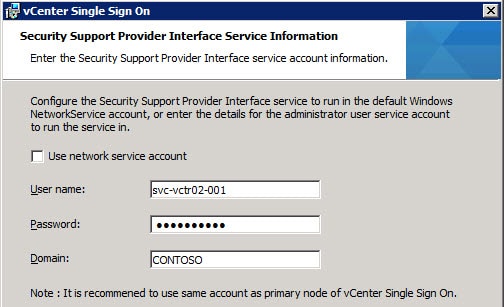
2. Create a domain-based service account (e.g. SVC-VCTR02-001) which the vCenter services will use. Add that account to the local Administrator’s group on what will become the vCenter 5.1 server.
You need to ensure the service account also has the “Act as part of the operating system” user right on the vCenter server. If the Administrators group has the right then you are covered. If not, explicitly add the service account to the user right as shown below.
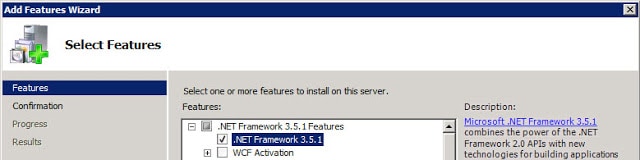
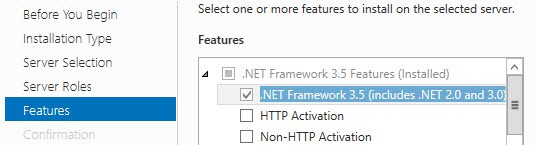
3. Open the Server Manager and add the .NET Framework 3.5 feature and wait for the install to complete.
Windows Server 2008 R2:
Windows Server 2012:
Configure SQL Database
SQL dynamic ports were NOT supported in pre-Update 1 builds (GA, 5.1.0a, 5.1.0b). The release notes for Update 1 state that problem has been fixed. The Update 1 SSO install the wizard has been modified to support dynamic ports for SQL server instances. Remember, VMware still does not officially support clustered SQL servers. They will provide best effort services if you run into issues, but it’s not a validated configuration.
The SSO service requires a database, as do other vCenter services. In this example we are using SQL Server 2012, but 2008 R2 SP2 is perfectly fine as well. Prior to Update 1 SQL Server 2012 was NOT supported, so don’t try it unless you are on vSphere 5.1 Update 1. There are some hard coded restrictions in the SSO service which limit your ability to use customized names for all of the fields. In particular the DB name must only include letters, numbers, underscore (_), the at symbol (@) and the hash (#). No periods and no spaces. As of the 5.1.0b release, hyphens are now allowed though.
As a reader has pointed out, you should be using SQL Server 2008 R2 SP1 and CU6 or later (Build 10.50.2811), which addresses a JDBC issue. You can read the MS KB here. I used SQL Server 2012 in my test environment, since that’s now supported as of vSphere 5.1 Update 1.
Unfortunately, I’m not able to get a SQL SSL configuration that actually works. So I’ve pulled the SSL steps, which were in the last version of this article. Be sure to set passwords on the SQL accounts that meet Windows GPO password complexity and minimum length requirements.
SQL DB Configuration Steps
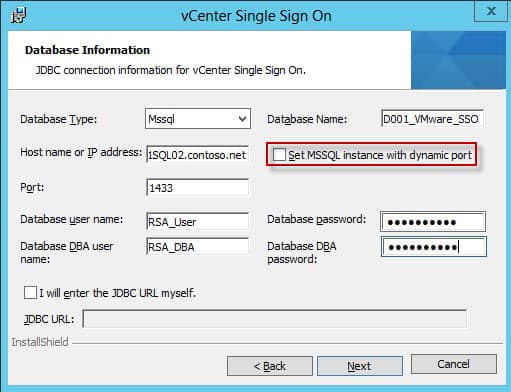
1. I created a custom database creation script below, based on the canned VMware script included in the installation ISO. In my case I called the database “D001_VMware_SSO”. Run this script in SQL Server Management Studio, modified to your liking. Note that you CAN NOT change “RSA_DATA” or “RSA_INDEX” as the SSO service is hard coded to use them and the install WILL fail if they are not present. The VMware script has auto_shrink enabled, which DBAs tell me is a bad idea. So that is not present in my script below.
USE MASTER GO CREATE DATABASE D001_VMware_SSO ON PRIMARY( NAME='RSA_DATA', FILENAME='K:\Microsoft SQL Server\MSSQL\Data\D001_VMware_SSO_Data.mdf', SIZE=10MB, MAXSIZE=UNLIMITED, FILEGROWTH=10%), FILEGROUP RSA_INDEX( NAME='RSA_INDEX', FILENAME='K:\Microsoft SQL Server\MSSQL\Data\D001_VMware_SSO_Index.mdf', SIZE=10MB, MAXSIZE=UNLIMITED, FILEGROWTH=10%) LOG ON( NAME='translog', FILENAME='L:\Microsoft SQL Server\MSSQL\Data\Logs\D001_VMware_SSO_Log.ldf', SIZE=10MB, MAXSIZE=UNLIMITED, FILEGROWTH=10% ) GO ALTER DATABASE [D001_VMware_SSO] SET RECOVERY SIMPLE GO CHECKPOINT GO
USE MASTER GO CREATE LOGIN RSA_DBA WITH PASSWORD = 'Your Password', DEFAULT_DATABASE = D001_VMware_SSO GO CREATE LOGIN RSA_USER WITH PASSWORD = 'Your Password', DEFAULT_DATABASE = D001_VMware_SSO GO USE D001_VMware_SSO GO ALTER AUTHORIZATION ON DATABASE::D001_VMware_SSO TO RSA_DBA GO CREATE USER RSA_USER FOR LOGIN RSA_USER GO CHECKPOINT GO
SSO Installation
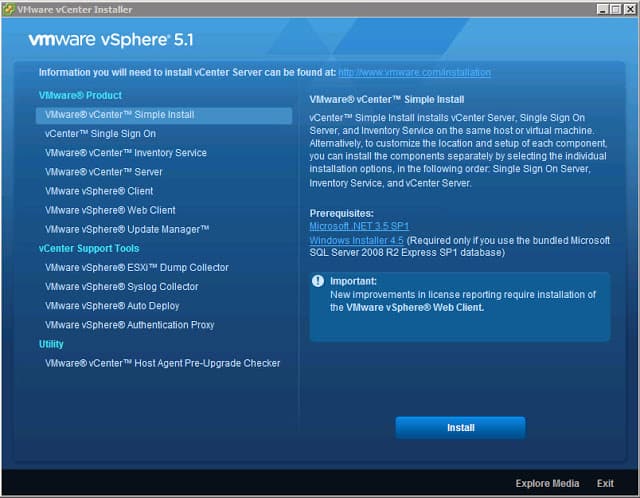
1. Login as the newly created vCenter service account and launch the vSphere installer from the ISO image and you are presented with the following screen.
At this point VMware gives you the option of a “Simple Install” or install each component separately. Since we want to replace SSL certificates in an orderly fashion and in the easiest possible manner, so do NOT select Simple Install. We want to deliberately install each service and perform configuration steps along the way.
2. Click on vCenter Single Sign On, then click on Install. Select the appropriate language and wait for the wizard to open. After clicking through the licensing agreements and carefully reading all of the patents, you are presented with a screen with several options.
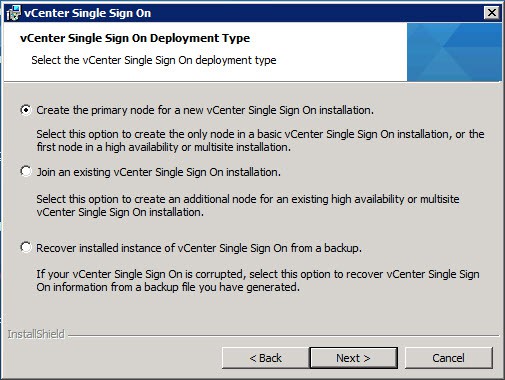
VMware gives you the option to install multiple instances of the SSO service for high availability. So on the screen below you have the option of creating a new primary node instance, or join an existing SSO instance. Since this is a new deployment, we want to create a primary node.
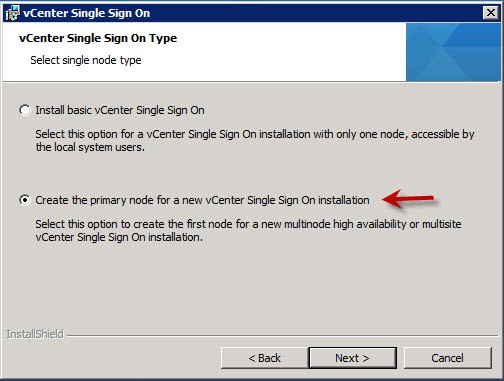
Even if you don’t want multiple SSO instances now, you may want them in the future. You don’t need to configure additional ones from the outset, so there’s no harm in leaving the door open for future expansion. Thus I selected the second option, as shown below. .
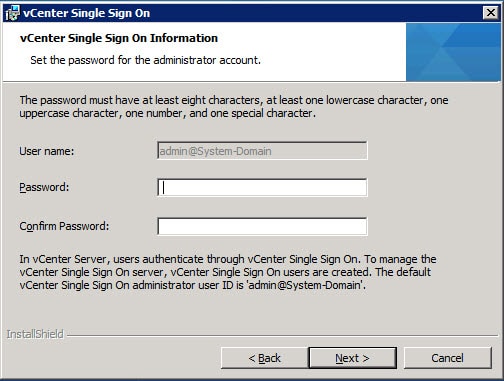
3. Next the installer will prompt you for the password to the default SSO Administrator account. Yes, this is a local account not tied to AD or the Windows host. After SSO is installed, you can configure it for one or more LDAP/AD server and other identity sources, so don’t fret too much about this application password but DO remember it.
The password must have at least eight characters, at least one lowercase character, one uppercase character, one number, and one special character. Maximum password length is 32 characters. Passwords longer than 32 characters will be truncated and cause authentication problems. The password also MUST meet local OS and AD domain length and complexity requirements. Password failures can cause the following SSO installation error:
Error 32010. Failed to create database users. There can be several reasons
for this failure. For more information, see the vmMSSQLCmd.log file in the
system temporary folder.
Note: Do NOT use the following characters, or trailing spaces:
^ (circumflex)
* (asterisk)
$ (dollar)
; (semicolon)
” (double quote)
‘ (single quote)
) (right parenthesis)
< (less than)
> (greater than)
& (ampersand)
| (pipe)
\ (backslash)
These may cause a “Error 29133.Administrator login error.” further on in the installation process. VMware has a KB article regarding these special characters here.
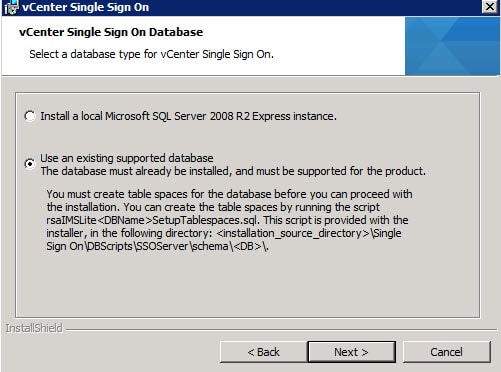
4. At this point you are presented with a dialog asking what kind of database you want to use. I would never use SQL Express in a lab or production environment, so select the second option.
Click on Next, and if everything is validated, no errors will appear.
8. For the installation path I left the default, as the installer has had problems in the path with custom paths or “unusual” characters in the path.
9. On the next screen I left the HTTPS port the default, then sent the installer off on its merry way.
At this point the vCenter Single Sign On service should have successfully installed. Next up is creating all of the SSL certificates that the vCenter services require. You can check out Part 2 here.




In the vmware script for the SQL DB, if you look at it, it has “FILEGROUP RSA_INDEX(
NAME=’RSA_INDEX’,
FILENAME=’blah.ndf'” yet you have changed it to .MDF – Is that a typo on vmwares part?
Anonymous, yes I think that is a typo. The database/log filenames are transparent to the SSO service. The file group names (RSA_) are the hard requirement.
No, ndf file is not a typo. SQL uses 3 types of files
MDF – Primary data file
NDF – Secondary data file
LDF – transaction log file
Do you know if SSO with Vsphere5.1 support SQL 2008 SP1?
It’s not clearly said in the software requierment. I’m looking to upgrade my SQL to 2008 R2 since I readed that Vcenter 5.1 does not support SQL 2008 SP1.
I am running Vsphere 5.1 Host Agent Pre-Upgrade Cheker, and once I click ” RUN PRECHECK ” all of my host (around 20) got the “Connection Error” All hosts (ESX 4.0 U1) are well connected to my VC 4.0
Thanks for the info I have found through repeated installs that the SSO admin password has particular special characters that cause the install to fail after a dozen attempts I found one that works.
Max, Unfortunately the vCenter 5.1 interop matrix hasn’t been populated, so I can’t tell which DBs are formally supported. You can find the tool at:
http://partnerweb.vmware.com/comp_guide2/sim/interop_matrix.php?
Thanks for posting the manual SSO DB creation script – May I link your post it on my blog http://vmadmin.info ?
thanks
vExpert2012: Yes Please feel free to link to my blog post, just make sure to attribute the post to me.
Derek,
thanks for your info. I have a quick question, we have two site separate vc/sq server what is the best way to install the new vsphere 5.1?
Anonymous, there are several considerations when looking at a production deployment. Such as high availability, planned usage, DR, etc. So I’d suggest reading VMware best practices and asking more specific questions in the VMware forums.
Hi Derek,
Great guide… but I couldn’t even manage to get past the first step. I can’t even manage to get a certificate into SQL, as Configuration Manager won’t recoqnise any of them as I can’t work out how to get the option “KeySpec” to be “AT_KEYEXCHANGE” out of my Certificate Services CA.
Did you use OpenSSL to request your SQL certificate, or just request it through the MMC?
Hi Derek,
I understand the SQL encryption is optional, but I wanted to set it up “the proper way”, so that when we come to do it in production things are done right.
I got the certificate, but then the installer bombs halfway through with “Error 29114.Cannot connect to DB”.
I’ve tried everything I can think of (mainly following the advice about disabling IPv6) and I’m now pretty much convinced that aside from your experience, getting this to work with SQL over SSL isn’t possible.
It’s a shame, because this would have been really good for us.
We had a similar issue where when we started the SSO install using the newer 5.1A release it gave a network error right away, something regarding ipv4 and ipv6. We also could not connect to the DB. Nothing we did with the adapters or networking revolved this. What I ended up doing was installing SSO using 5.1GA – the original release – and that worked fine, and then upgraded to 5.1A.
on this step do i need to create the cert for SQL server?
Anonymous, creating a certificate for the SQL server is totally optional. Best practices would tell you to encrypt database access across the wire. But everything will work fine in clear text, or using some other encryption method like IPsec.
Anonymous: If you are just doing small test lab then sure you could put them on one box. But for anything in production I would separate them.
having an error wheninstalling vSphere Update Manager on the same server that vCenter is installed: setup failed to connect to the database, please make sure that you entered the correct DSN username and password.
any suggestions.please advise.
Anonymous, did you validate the database connection via the ODBC GUI? If that validation works, then VUM should easily install. If the ODBC verification fails, then you have an authentication problem. Need to check the VUM database permissions and validate the account used to access it has the proper permissions.
Dear Derek,
Thank you this valuable material. Prior to doing a fresh installation I actually tested upgrading to 5.1 in my lab environment which went pretty smooth. On the other hand today I tried installing it from scratch and I keep getting this error every time I try to access my vCenter via vSphere Client 5.1.
—————————
Could Not Connect
—————————
vSphere Client could not connect to “server.domain.tlds”.
An unknown connection error occurred. (The request failed due to an SSL error. (The request was aborted: Could not create SSL/TLS secure channel.))
—————————
OK
I’ve been troubleshooting this since more than 8 hours now :/.
Abdullah and Joe, did you verify the rui.key file has the proper headers in it? Check out step 4 in this post: https://www.derekseaman.com/2012/09/vmware-vcenter-51-installation-part-2.html
I had a couple addition based on going through this.
In step 7 using the “*” character will also result in an error. Using a “.” is a special character that will work however.
In step 12 a few extra steps are needed if the database is configured to use a different SQL instance.
First the database instance needs to be configured to listen on a specific port, such as 1435.
Second the jdbc line needs to be specified in the format.
For example
jdbc:sqlserver://SERVER.DOMAIN.COM:1435;instanceName=INSTANCE;databaseName=SD01_VMware_SSO;integratedSecurity=true;
This page led me to that solution.
http://it.christman.co.uk/vsphere-5-1-single-sign-on-sql-named-instance-error/
Unfortunately it looks like I may have spoke too soon about Step 12, with the database instance. While that does get through the initial configuration, I think there is something missing.
When I got to the third post in this series I ran into problems with the ssolscli.cmd I was receiving 404 errors, in investigating some of the log files I saw several jdbc errors that the database was not specified. Eventually I just abandoned using a SQL instance.
Alan
In step 7, you very helpfully cite some special characters that should not be used for the admin@System-Domain account. I discovered additionally that the ampersand (&) character is invalid for use in the password. If you use it, the installer will hang because at one point a command is passed java.exe containing this password, but the command gets truncated at the ampersand, and java.exe never exits. Additionally, the password cannot be 36 characters in length. Installation will succeed with a long password, but the command line utilities (such as SSOPass and SSOCLI), and the Inventory Service installer will fail when… Read more »
how to configure cert for SQL SSL server? please advice. thanks
Great Post! Part 1, number 17 states “After the SSO service installs, it generates a number of unique passwords …” I didn’t not see any passwords generated. Will that be a problem? Now, how do I find out the passwords? I am using self-sign SSL.
After a disaster upgrade to 5.1 I found your blog, can you elaborate on this statement: “UPDATE 10/7/2012: VMware may be releasing an update to vCenter 5.1 later in October that should address many of the SSL problems”
Where did you find this at? I am delaying my upgrade until this update is available and would like to monitor its release. Thanks!
@Anonymous: The fix/patch/update has been delayed a few days. No ETA as of yet.
Hi
There is lots of post install DB scripts when you use a remove DB, do we need to use this?? Since I am installing this on SQL that is not the same server for the vCenter. I have run the scripts for the DB install, and all is ok, but having some problem with the post install SQL Scripts.
Thank You
JL
Hi Derek,Read through all your guide and found it excellent! Thanks very much, learnt a lot regarding SSL! =) One question though – What would the process look like if you plan to use the vCenter Server Simple install (which installs everything in one go)? Would you create and pre-stage the SSL certs before starting the install?So basically:1. Ignore the SSO install at the end of part 12. Create the SSL certs in Part 23. Pre-stage the certs according to your pre-stage post4. Create DBs and complete the vCenter Simple install5. Update the SSO certs according to Part 3. Does… Read more »
Any chance of doing a Windows Server 2012 with a local SQL 2012 version of this?
@Derek: Those are not officially supported. I would not use them in any production environment.
True… but I just did it and it’s working like a charm.
Well, with one exception that the Storage service didn’t get installed. This means the storage views are not available.
Will probably go back to Win2008 R2 for the OS and a local SQL 2008 R2 Standard server, but it would be nice to have it on the latest and greatest.
Found this missing from Section 14, part G.
;trustservercertificate=true
SSO installer will create the RSA_USER and RSA_DBA accounts properly now in the installer. If the accounts are created manually, the database table structure SQL scripts need to be run to populate it before letting the SSO installer begin the install process.
Using all the (14?) posts I was able to setup a fully functioning vCenter server. I then started to go through again to install a second server in a multi-site configuration. I selected “Join an existing vCenter Single Sign-On” option. After giving the credentials for my existing vCenter server, the install fails with:
Failed to get type of server, Exception :com.vmware.vim.sso.admin.exception.InternalError: General failure.
Has anybody else been able to get a multi-site install working?
You create the database by script but create the db accounts with studio. In the installation source there is a script called “rsaIMSLiteMSSQLSetupUsers.sql” for that task.
IMHO it would be more consistent to do both via script.
Just an attempt to make a great article a little better.
grubi.
Derek – have you done any testing with multisite config? I seem to be unable to get past the step where it tries to validate against the primary. I have a fully functional vc setup with SSO, but it just hangs on the second SSO server install when I put in the FQDN, port and password. Following your steps, I’ve replaced my certs, and the primary site is working fine, but I’m wondering if maybe the certs are the cause for the secondary site?
I have a ticket open with VMware, but haven’t received a response from them yet.
As others have reported, I can’t get the SSO installation to work with JDBC using SSL. I created a jks.keystore as described above and selected a SSL certificate on the SQL server. I used the JDBC connection string jdbc:sqlserver://;serverName=vCenter.mydomain.com;port=1433;databaseName=RSA;integratedSecurity=true;encrypt=true;truststore=C:\ProgramData\VMware\SingleSignOn\SSL\jks.keystore;truststorepassword=mystorepassword. During the installation I get Error 29115. Cannot authenticate to DB. This happens with Force Encryption either Yes or No on the SQL server. Looking at the SQL Management Studio, I see that the installer has deleted the SQL logins for RSA_USER and RSA_DBA, so no wonder it can’t authenticate. It’s not clear if or how others have gotten past this… Read more »
Hi – Really great work! One question, I have created a vcenter service account (vmlab\vcenter-service). Account is added to local admin group on vcenter server. But when I use it in the install wizard (deselect use network service account”) it always says “Could not find the specified user on provided domain” when clicking next. Im am sure password is correct. If I use the domain administrator it passes to next screen. Any idea what Im missing? Kind regards, Bjørn.
.Hi Derek. I came across your site via Google. I had install SSO5.1 the simple way and decided to build a Windows 2012 domain and do an enterprise install, DC, CA, SQL2012, and vCenter/SSO on their own vm’s. A few hiccups on SQL now resolved (I know it’s not supported yet, but…) anyway I found your work on certificates so I am following it and building as I go along. Everything was great until I tried to create the keystore. No amount of changes would get it to work until I had a brainwave, type cmd in powershell and it… Read more »
Thank you very much for your very useful guides Derek.
I would like to install a complete fresh installation of vCenter 5.1.0a with your guides and public SSL-certs. VMware has released today version 5.1.0b, does your guides fit to the new release? I’m asking because didn’t like to install outdated versions 🙂
I hit a brick wall … in the installation window that said Single Sign On information admin@System-Domain / Password next line Lookup services URL filled the line with the following url https://vcenter.labo.local:7444/lookupservice/sdk , hit next and I got the following error message Could not contact lookup service. Check vm_ssoreg.log in system temporary folder for detail … see below can someone please help me figure why it wont let me install ? Thank you. [2012-12-24 16:52:18,286 main ERROR com.vmware.vim.install.cli.commands.CommandArgumentsParser] Unable to connect to server[2012-12-24 16:52:18,286 main INFO com.vmware.vim.install.cli.RegTool] Return code is: ServiceNotResponding[2012-12-24 16:52:27,319 main DEBUG com.vmware.vim.install.cli.RegTool] $Id: //depot/vicore/vicore-vsphere51p01/regtool/viregtool/src/main/java/com/vmware/vim/install/cli/RegTool.java#1 $[2012-12-24 16:52:27,335 main… Read more »
Installing the 5.1.0b version of vCenter.During the SSO installation I came across two SQL issues:1. Error 29114. Cannot connect to DBThis issue is occurs when the SSO database RSA (default SSO DB name) does not meet the prerequisites for the SSO installation and the RSA DB table space RSA_INDEX has a filegroup type of PRIMARY, instead of RSA_INDEX. I had to change this manually in SQL Server Managerhttp://kb.vmware.com/selfservice/microsites/search.do?cmd=displayKC&docType=kc&docTypeID=DT_KB_1_1&externalId=2036318 2. And again, Error 29114. Cannot connect to DBThis one is an unexplained error. I used the VMware outlined account of “RSA_USER” The account was added as a local security login for… Read more »
Wanted to say thank you for the post. The script also worked perfectly. This helped me implement the upgrade from 4.x to 5.x vCenter today. /SALUTE
Great guide! This helped me alot when upgrading to 5.x!
Hi Derek
Great blog, but question why using OpenSSL 1.x when Vmware requires the use of openssl 0.9.8 (MUST). I am in trouble installing inventory service (install hangs) and opened an SR with Vmware. They asked me to redo the whole procedure using their KB 🙁
kind regards, yvan
@Anonymous: OpenSSL 0.9.8 and earlier use a different hashing algorithm when you are creating the trust store with the filnames ending in .0. However, the newer versions of OpenSSL have a flag to use the old hashing algorithm. So I haven’t seen any problems, as long as you use the right flags (which are in my steps).
Hi Derek, Your articles were really helpful. Thanks for putting it together. I am trying to figure out how to configure HA (19 Attempts till now)I am using Stingray Traffic manager.Also referring KB2033588. In Lab 1st I Installed Node1(SSO-A), replaced ssolscli.jar, installed Node2(SSO-B) as secondary node. made changes to server.xml on both Nodes. I did configure StingrayTM (virtual appliance) Virtual Server with a SSL.Set VirtualServer to decrypt the traffic, then apply rules to Map traffic appropriately according to KB2033588. The services got updated. Issue: After updating services on SSO-B SSOlscli listServices in giving error when trying to communicate on https://ssoha.vhomelab.com:7444/sso-adminserverfrom… Read more »
Hi Derek, Your articles were really helpful. Thanks for putting it together. I am trying to figure out how to configure HA (19 Attempts till now)I am using Stingray Traffic manager.Also referring KB2033588. In Lab 1st I Installed Node1(SSO-A), replaced ssolscli.jar, installed Node2(SSO-B) as secondary node. made changes to server.xml on both Nodes. I did configure StingrayTM (virtual appliance) Virtual Server with a SSL.Set VirtualServer to decrypt the traffic, then apply rules to Map traffic appropriately according to KB2033588. The services got updated. Issue: After updating services on SSO-B SSOlscli listServices in giving error when trying to communicate on https://ssoha.vhomelab.com:7444/sso-adminserverfrom… Read more »
Nice post, Derek! I was writing a post / video combo on the SSO database and found your article, you’re added as a resource to visit!
http://wahlnetwork.com/2013/02/04/successfully-installing-vcenter-sso-part-1-sql-database/
Hi, all! i have some error in step6 – database connection has failed. Logfile sayd: [2013-02-07 11:42:56,379] INFO 0[main] – com.vmware.vim.installer.core.logging.CoreLoggerImpl.info(?:?) – Validate database connection[2013-02-07 11:42:56,379] INFO 0[main] – com.vmware.vim.installer.core.logging.CoreLoggerImpl.info(?:?) – DB information jdbcUrl:jdbc:sqlserver://;serverName=192.168.100.15;port=1433;databaseName=D001_VMware_SSO type: Mssql[2013-02-07 11:42:56,379] INFO 0[main] – com.vmware.vim.installer.core.logging.CoreLoggerImpl.info(?:?) – Initialize values of user DBA user SSO_DBA , other user SSO_User[2013-02-07 11:42:56,379] INFO 0[main] – com.vmware.vim.installer.core.logging.CoreLoggerImpl.info(?:?) – DB information jdbcUrl:jdbc:sqlserver://;serverName=192.168.100.15;port=1433;databaseName=D001_VMware_SSO type: Mssql userName:SSO_DBA[2013-02-07 11:43:26,565]ERROR 30186[main] – com.vmware.vim.installer.core.logging.CoreLoggerImpl.error(?:?) – Failed to established connection :com.microsoft.sqlserver.jdbc.SQLServerException: The TCP/IP connection to the host 192.168.100.15, port 1433 has failed. Error: “connect timed out. Verify the connection properties, check that an instance of SQL… Read more »
Hi, Has anyone been able to get the instructions for using this with an SSL secured SQL server to work? I followed the instructions above about using encrypt=true and have not been able to get either the install to work or the service to connect (once installed). I found VMware KB 2035831 which states: This issue can occur if the Force Encryption option in the SQL Server Configuration Manager is set to YES. To avoid this installation error, change the setting to NO Which seems to imply that you cannot install the SSO Server with the SSL encryption set to… Read more »
Great post! thanks for all the effort you have put into this. I do have a question though, I cannot get the SSL SQL connection part of the SSO install to work at all. I have followed your instructions to the letter as well as other suggestions on the VMware forums with no luck, I always get Error 29114 Cannot Connect to DB when it reaches the configure Single Sign stage during the install. (password complexity is fine, no illegal characters) VMware’s recommendation is to turn off Force Encryption on the SQL server which is a pretty poor workaround to… Read more »
Good stuff… thank you for insight on this mess of a product (SSO anyway). We’re just testing having built a lab for the 4.x to 5.1 planning and SSO install fails at very end with “error 29148.STS configuration error” and rolls back after clicking OK. We’ve used VMware’s own scripts for db/tables and user creation which run fine. All prompts in installer accepted, no fancy SQL SSL config attempted initially just keeping it all very simple. Still fails. Same 29148 error and nothing found online for it so opened a ticket. Will advise… but meanwhile, anyone seen that particular error?… Read more »
Figured out the issue prior to VMware calling me back (and their support responsiveness has been increasingly drawn-out in the last year or so I must say versus the good ol days of circa ESX 2.5/3.x but I digress). The installer failed with that cryptic error because it didn’t like a circumflex ^ character in the password of the domain account I was using for the SSPI service. While that character restriction is duly noted in the release notes for 5.0.1b where the SQL users and admin@system-domain account is concerned, there is nothing noted where the SSPI service/configuration dialog of… Read more »
For those of you having an issue getting these instructions working and are getting the generic error “Database Connection has failed. refer to vm-sso-javalib.log for more information” and in the vm-sso-javalib.log you see something like this at the end of the attempted handshake: “[2013-02-15 13:33:33,519]ERROR 0[main] – com.vmware.vim.installer.core.logging.CoreLoggerImpl.error(?:?) – No Database Name is provided[2013-02-15 13:33:33,535]ERROR 16[main] – com.vmware.vim.installer.core.logging.CoreLoggerImpl.error(?:?) – DatabaseName is either not supported or wrong :com.vmware.vim.installer.core.common.InstallException[2013-02-15 13:33:33,535] INFO 16[main] – com.vmware.vim.installer.core.logging.CoreLoggerImpl.info(?:?) – could not close JDBC connection”Make sure you have SQL Server 2008 R2 SP2 installed or at least the hotfix that pertains to this KB article: http://support.microsoft.com/kb/2653857After I… Read more »
Disregard my post about SP2 on SQL 2008 R2, it isn’t in the support matrix for vcenter 5.1…….
the hotfix does seem to resolve the issue though.
Hadn’t really considered the certificate security until I happened upon your posts Derek. Appreciate you taking the time to share. I’ve been struggling like others with the forced encryption errors and have seen most of the errors listed above – spent hours so far trying to get it to work but… importantly.. I like to remind myself that I’ll now remember this stuff all the more because it didn’t fly straight through without a glitch ;-). Will try the SQL 2008 R2 SP2 install as I came back today to confirm what exact version of SQL you were using and… Read more »
I had success up until where it said,”Configuring LookupService. It will take few minutes…” (I didn’t notice the grammatical error until typing this up just now. I’m sensing a theme. Anyone else feel like a beta tester right now?)
It fails with “Error 20010. Failed to configure LookupService.”
Which I will google and get back to this.
And to add to the Force Encryption setting on the SQL Server question everyone has been asking, I can’t get this to work with Forced Encryption enabled either.
The SQL patch only resolved my inability to connect using encryption with the jdbc driver.
If you have OPENSSL installed when you are installing HA or Multisite. The installer might hang at on the “vCetner Single Sign On Type” screen. if it does open task manger and kill the openssl proccess ( maybe 2 or 3 times) and it will continue with no errors. This is a known issue but has not been publish in a kb yet.
Ok, performed more testing on my environment. I can install error free on any variation of settings except when I use the JDBC string. (passes with SSPI account set to domain account and non-default installation folder)Seeing as I get past the SQL connection page with the string and fails later on, that it’s probably the key store. (It appears the SQL patch takes care of the initial jdbc connection)My question is, working with a snapshot on the vcenter server connecting to an external database server, do I need to regenerate the keystore every time I roll the vcenter server back… Read more »
I’ve rolled the databases back, same result. “Error 29115.Cannot authenticate to DB.” Where the status shows “Configuring Single Sign On”.Forgot to give the account that I was running the service under access to the database. Gave it dbo access to the “RSA” database, re-ran the install after rolling everything back again. I’m back at “Error 20010.Failed to configure LookupService.”Changed the user for service authentication I was using from one that had an underscore in the name to one without, and I get “Error 29148.STS configuration error.”Going to try the default account.I don’t know how comfortable I am putting something that… Read more »