InfluxDB + Chronograf: Configuring Let’s Encrypt SSL
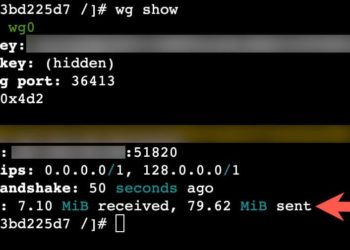
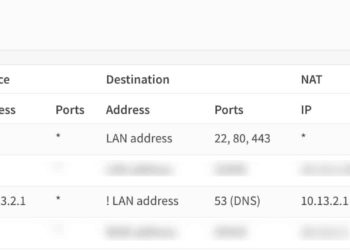
If you value security and want to use InfluxDB 1.x and Chronograf with trusted SSL certificates from LetsEncrypt, this post is for you! This tutorial assumes you are running InfluxDB 1.x and Chronograf either in a LXC container or a traditional VM. If you are using Docker, the procedure would...