In a previous post a while back I wrote how to capture outbound DNS queries with your Ubiquiti EdgeRouter and forward them to Pi-Hole. Now that I’ve transitioned to OPNsense + NextDNS (replacing my EdgeRouter and Pi-Hole), I wanted to post how to do the same thing in OPNsense.
Why is this needed? Well when you use DHCP on your LAN, not all commercial devices may respect the DNS server(s) in the DHCP response. Google devices are famous for hardcoded DNS entries to 8.8.8.8. I want all DNS queries to flow through NextDNS, and bypass hardcoding.
This blog post will show you how to easily configure a NAT port forward rule that will redirect all outbound port 53 queries to the LAN IP of your OPNsense firewall, which can then use NextDNS to filter/resolve. If you want to know how to configure OPNsense to use NextDNS, you can read my post here.
Configuration
- Go to the OPNsense GUI, and navigate to Firewall, NAT, Port Forward.
- Create a new rule with the properties in the screenshots. Note here that my OPNsense LAN IP is 10.13.2.1, so substitute your IP for that address. Otherwise, exactly copy the rule settings as shown.
After you create the rule, it should look exactly like the screenshot below except with the LAN IP address of your OPNsense firewall.
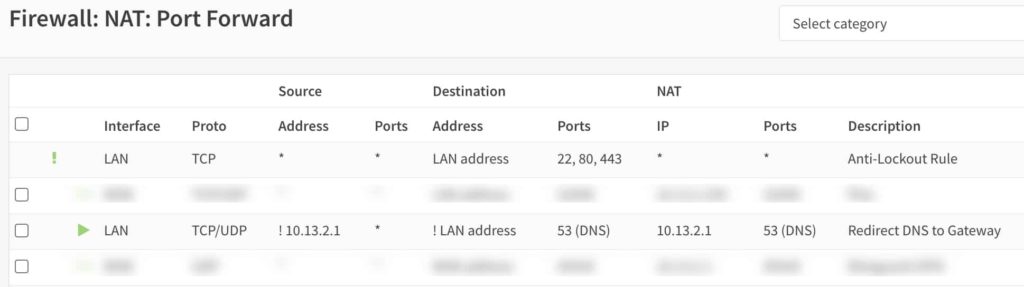
Summary
Setting up a DNS capture rule for OPNsense is not hard. You can do it with a single rule. If you want to make sure it is working, you can tick the Log box, and then review the OPNsense logs for hits on that rule. Google devices are quite chatty with DNS so you likely won’t have to wait long for a rule hit.
Note, that if you are using the totally awesome Sunny Valley Sensei next-generation firewall plugin, the DNS transactions Heatmap will still show queries going to and being answered by the external DNS server, e.g. 8.8.8.8. But, if you review your NextDNS logs, you will see those queries in the logs so the redirection rule is working.
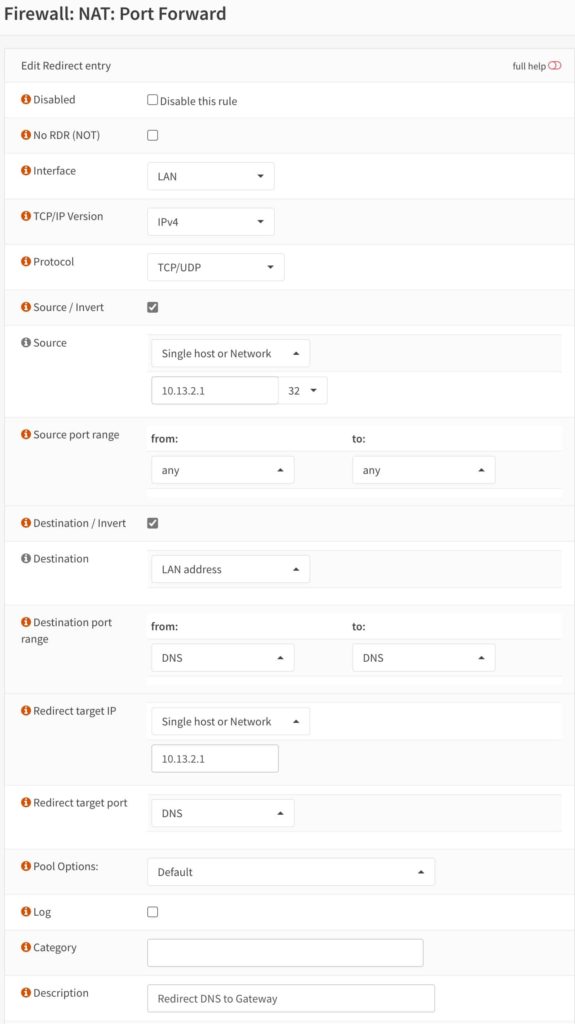





Didn’t you just create an any loop to port 53…?
thanks for this Derek, however, I found that as I’m using unBound for my DNS, the DNSBL’s get bypassed when enabling a NAT rule for DNS.
Have you experienced that too?
Thx for this!
I now have my Chromecast working with its DNS redirected to the PiHole.
Just had to put in the PiHole ip address instead of the OPNsense gateway.
I have external DNS requests blocked in OPNsense, and with this port forward rule, the chromecast is behaving nicely.
Cheers