Continuing on from Part 3 of the VMware vCenter Certificate Automation Tool series, we are now ready to replace the Web Client and Log Browser SSL certificates. If you want to start at the beginning, check out Part 1.
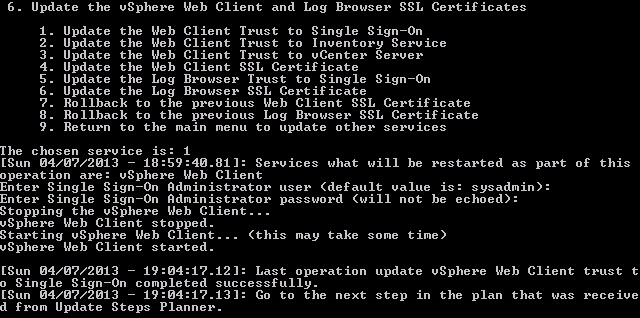
1. Pressing 5 takes us back to the main menu. Now we press 6 to enter the web client and log browser update process. Pre the pre-planning guide we need option 1. I enter the SSO administrator username and password.
Several minutes later the process was a success.
Step 11 of the pre-planning guide is complete. Check!
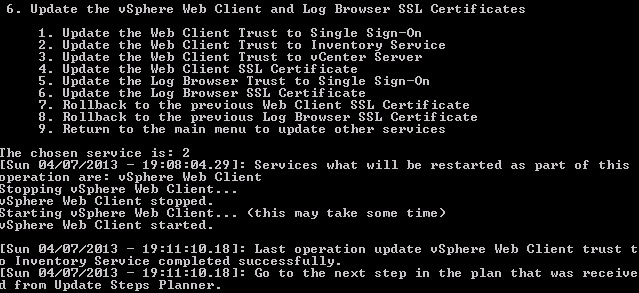
2. Now we need to press 2, to trust the inventory service.
Several minutes later the process was a success.
Step 12 of the pre-planning guide is complete. Check!
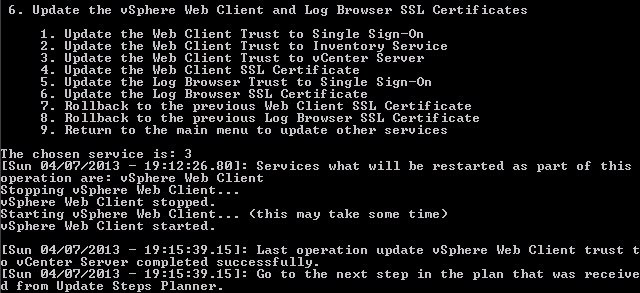
3. Now we need to press 3, to trust the vCenter server.
Step 13 of the pre-planning guide is complete. Check!
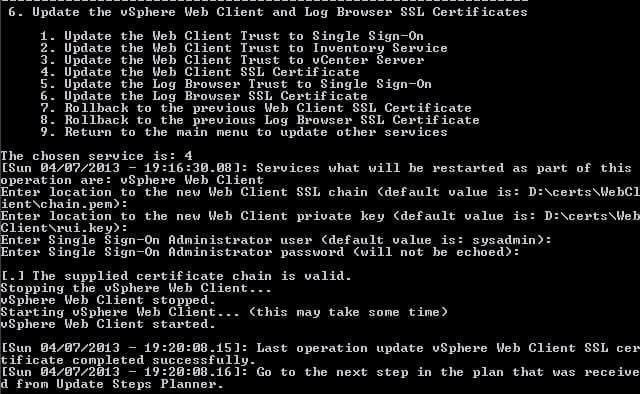
4. Now we need to press 4, to update the web client SSL certificate. Again, the presented paths and files were correct. Enter the SSO administrator username and password.
Step 14 of the pre-planning guide is complete. Check!
5. Next up is pressing 5, to enable the log browser service to trust SSO.
Step 15 of the pre-planning guide is complete. Check!
6. Now press 6, to update the log browser SSL certificate. Again, the certificate and paths looked good. Enter the SSO username and password.
Step 16 of the pre-planning guide is complete. Check!
At this point, since I’m using the vCenter FQDN for the VUM configuration, I am not able to use the v1.0 of this tool to update the VUM certificates. You can check out Part 12 of my vSphere 5.1 Install series for the manual method to update the VUM SSL certificate.
7. To validate some of the certificates I launch the vSphere web client. Using my web browser I view the SSL certificate and validate that my new certificate is being used. I also open the log browser and pull down the logs from an ESXi host to verify that works as well.
Minus the VUM “known issue”, the tool worked flawlessly for me and certainly helped ease the SSL burden. I’m hoping future versions of the tool have the following enhancements:
- Automated execution of the pre-planning steps, so I don’t have to keep referring back the 18 step list and checking off each one (assuming an all-in-one server).
- Ability to create CSRs, submit to a Microsoft online CA, and download the certificates.
- Ability to create CSRs for an offline/commercial CA, and use the resulting certs
- Automatically build and verify the CA chain files, to reduce human error and confusion
- Provide a full GUI with detailed logging, to make the processes even easier
- Perform full certificate validation to ensure unique DNs
- Fix the VUM FQDN “known issue”
- Back-port the tool to work with vSphere 5.0
- Perform SQL database password validation
- Cache in memory all required passwords (flushed upon error or exiting)
- Configure all ODBC/JDBC SQL connection strings to use SSL (if SQL supports SSL)
I think the tool is a decent first stab at helping with the SSL configuration nightmare that 5.1 unleashed on the community. The process could be more fully automated, so I hope future versions can improve on this useful utility.





Over the course of the past year I've installed vCenter for three clients. Including my own lab, that means 5 vCenter installs. This is vCenter install 6 in my lab where I'm using the Certificate Tool (and hopefully this install will be my lab "production" install).
About to jump head first with this new tool. If you don't hear from me for a few days it means something broke and I'm tossing servers into the Gulf of Mexico.
Hi Derek, thank you! It's very helped me!