Windows Server 2019 Two-Tier PKI CA Pt. 3
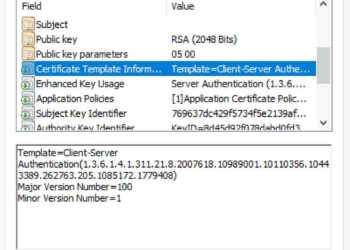
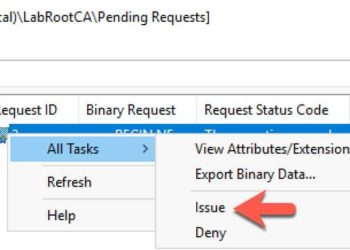
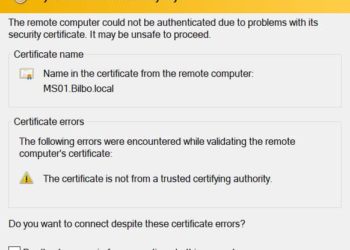
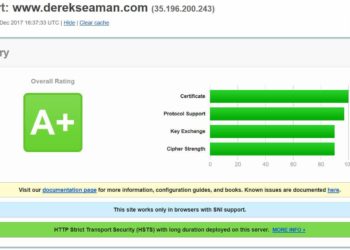
Now that we have our offline Windows Server 2019 certificate authority configured in Part 1, and our online subordinate setup in Part 2, now we should setup auto-enrollment and secure the subordinate’s web certificate services with SSL.Auto-enrollment is where domain joined Windows computers are automatically issued a computer certificate. Services...