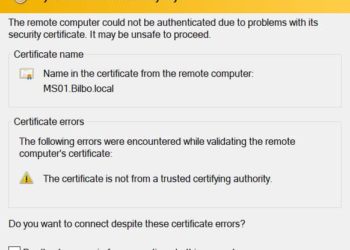
Trusted Remote Desktop Services SSL Certs for Win10/2019
One of the most popular posts of all time on my blog has been Create Trusted Remote Desktop Services (RDP) SSL Certificates for Windows 2008R2/2012/Win7. That article is a few years old, so I thought I would update it for Windows Server 2019 and Windows 10. The fundamentals have not...