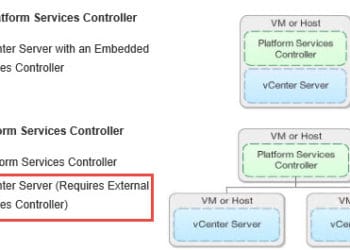
vSphere 6.0 Toolkit Update
In my new role at Nutanix I've had the pleasure of working with end customers, and configuring their vSphere 6.0 environment. During this process, SSL certificates have come up. Surprisingly, thus far my clients have chosen the VMCA method of deploying certificates. This is great, as it automates certificate deployments...