Digital Privacy Decoded: Simple Ways to Secure Your Information
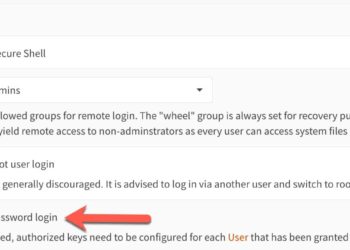
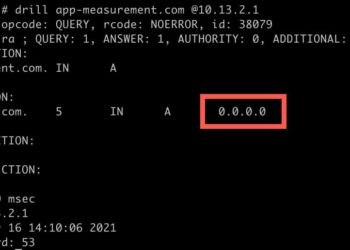
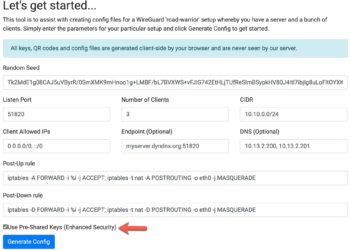
In today's interconnected world, safeguarding your personal information is more crucial than ever. With telecommunications companies collecting extensive data about your communication habits, it's essential to understand how this information is used and how you can protect your privacy. From disabling Customer Proprietary Network Information (CPNI) to securing your Social...