Installing Nutanix Community Edition (CE) on vSphere 7
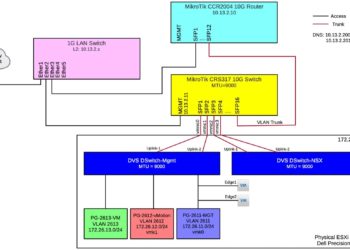
For a number of years now Nutanix has offered a 'community edition' of our AOS and Prism Central software suite. The community edition closely resembles the enterprise versions, but is packaged in a way to allow it to install on commodity hardware, or in a nested virtualization environment. It's also...