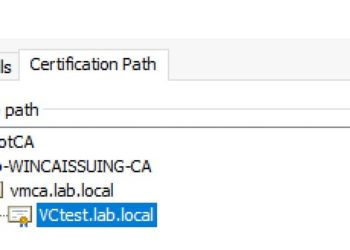
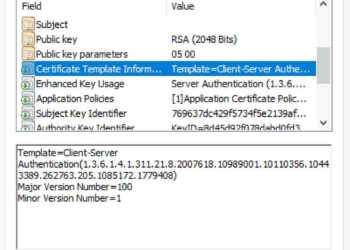
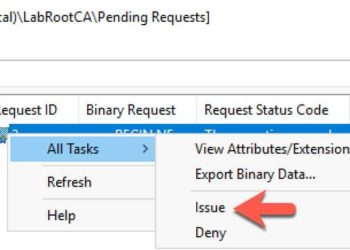
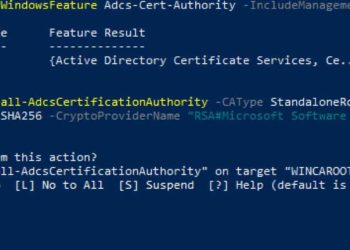
vSphere 7 – Certificates with VMCA as Subordinate
Over the years I've written a number of blog posts about replacing the SSL certificates for vSphere. Back in the day it was exceedingly difficult and was very error prone (think 5.x and 6.x). However, VMware has made great strides with vSphere 7 in how you manage certificates. Yippee!For enterprises...