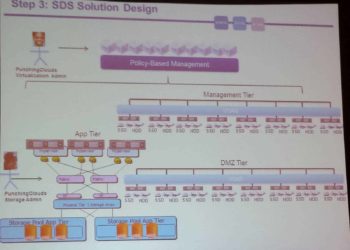
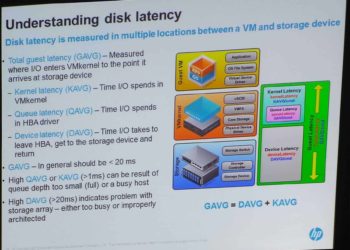
Building a Haswell ESXi Server for VSAN
For a few years I've been occasionally posting home ESXi "server " builds. The last one I did was for SandyBridge. I have two such hosts, and they've been working really well. But after attending VMworld this year in San Francisco and hearing about all the VSAN goodness, I'm going...