VMworld 2015: vCSA Best Practices
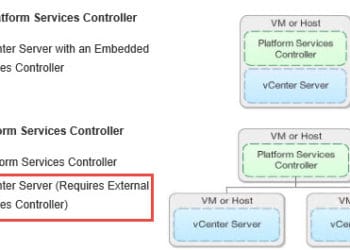
INF4528, William Lam, VMware VCSA is on parity with Windows server in terms of scale and performance VUM still requires a Windows server (future version will not) FULL VUM capabilities in vSphere web client in 6.0 U1 Deployment types: Embedded (PSC and VC), or PSC as external Multiple vCenters can...