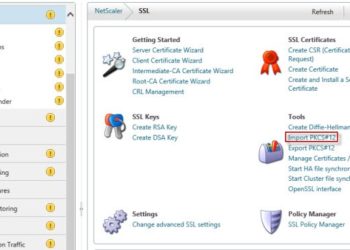
Import IIS SSL Certificate to Citrix NetScaler
For a recent project I've been configuring a Citrix NetScaler (which are wickedly cool) for load balancing of a web service over SSL. The web service is hosted on a Windows server using IIS, so I wanted to re-use the SSL certificate on the NetScaler. The steps to import IIS SSL certificate...