This article discusses my recent migration from NextDNS, a popular ad and malware filtering DNS service, to Control D. Several years ago, I transitioned from Pi-hole, a local network-based ad and malware tracker, to NextDNS due to its enhanced functionality. However, NextDNS failed to keep pace with the industry. Its lack of new features motivated me to look for an alternative DNS filtering service.
Interestingly, I discovered Control D in a conversation thread on the NextDNS forums. Amid the multitude of user complaints regarding NextDNS’s stagnation, Control D was suggested as a potential solution. Upon investigating, I was very pleased with Control D’s features and improvements over NextDNS. Consequently, I installed the Control D server on my Firewalla and transitioned my network usage entirely over to Control D. I’ve been very happy with the migration as it addressed several shortcomings of NextDNS and provided me a significantly better user experience.
In this article, I aim to highlight the distinguishing features of Control D over NextDNS. This will explain my swift decision to terminate my subscription with NextDNS, a company I now firmly believe is complacent and has stopped investing in their platform.
Disclaimer: I have no relationship with Control D. I have no affiliate or referral links. I paid for my subscription just like anyone else. I just happen to be really impressed with the service.
Bottom Line: Except for some nitpicks with their web UI I’m sold on Control D as a full NextDNS replacement. They also have a robust development road map, with feature releases every 2-3 weeks. This is NextDNS on steroids, along with a full public API.
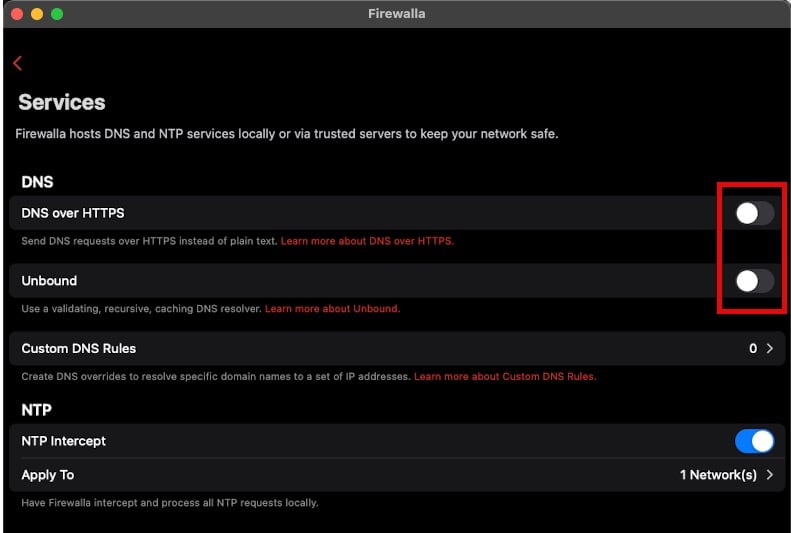
Update April 9, 2024: Added a screenshot in the Firewalla section noting to disable DNS over HTTPS and Unbound.
What is Control D?
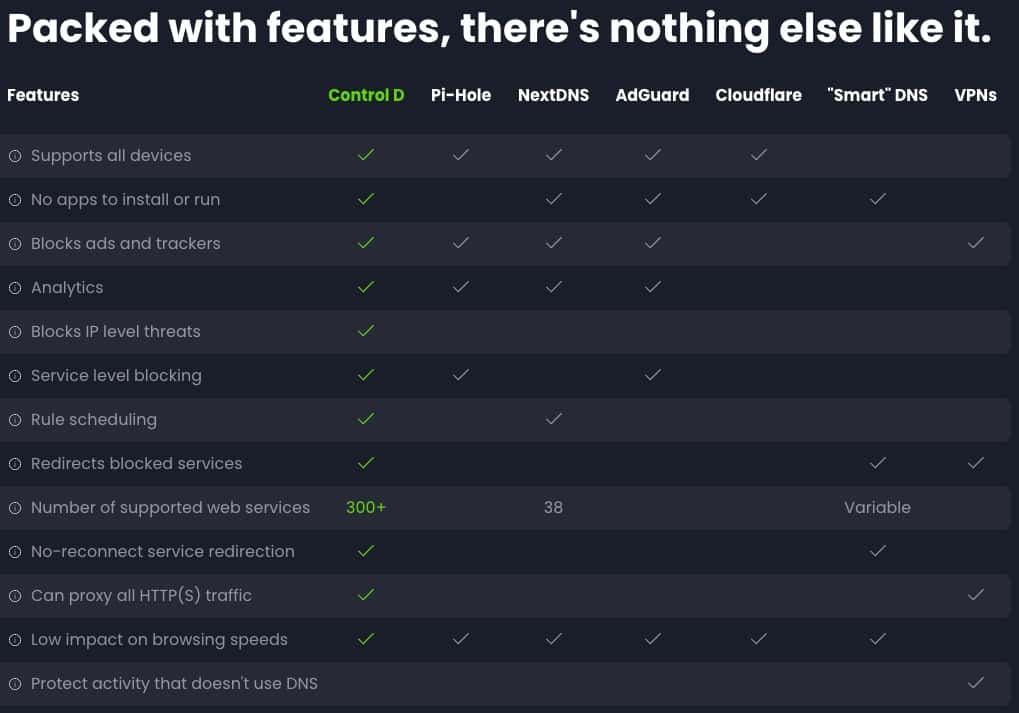
Control D is a cloud-based DNS service that provides robust security and privacy features. It features blocking of cyber threats including malware and harmful content, as well as trackers and ads for enhanced browsing safety. The service can be quickly deployed onto an entire network by installing their Control D server on your router/firewall.
What sets Control D apart from NextDNS is its many customization settings, designed to meet varying security and privacy preferences. Users can fine-tune their control of ad-blocking, content filtering, and even privacy settings on a per-device basis with their web UI. Control D provides a number of automated installers for many common routers, including Firewalla.
Control D fully encrypts all upstream DNS queries, so the prying eyes of your ISP can be avoided. My testing also revealed that the Control D DNS servers have lower latency for me (SoCal), than NextDNS (7ms vs. 9ms).
Some of the Control D features include:
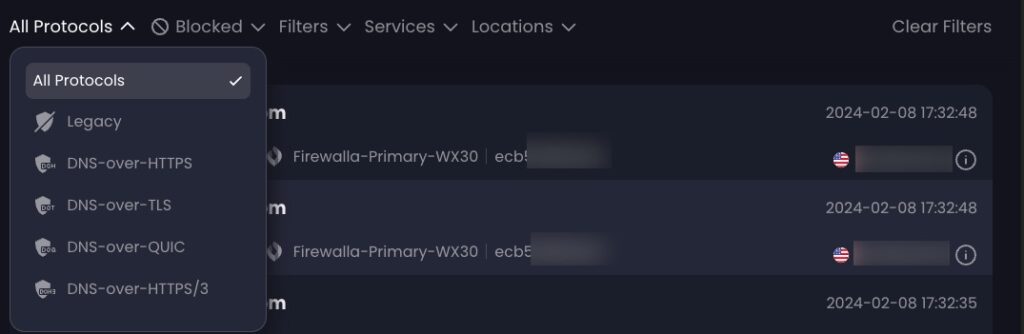
- Supports DNS-over-HTTPS (DoH), DNS-over-TLS (DoT), DNS-over-HTTP/3 (DoH3), DNS-over-QUIC, and plain UDP 53.
- Single command line setup of the Control D server on a variety of routers including Firewalla, DD-WRT, OpenWRT, Fresh Tomato, GL.iNET, Synology, OPNsense/pfSense, Ubiquiti, and more.
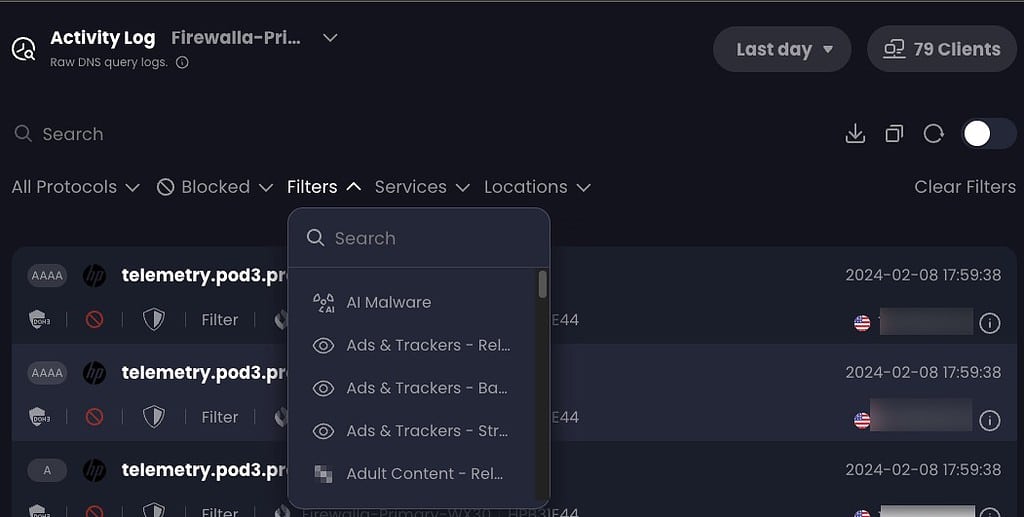
- 18+ filter categories such as crypto, ads & trackers, malware, gambling, adult content, and more.
- Malware filters that are based both on FQDNs and IPs.
- Ability to route specific service traffic (e.g. Netflix) through one of over 100 proxy exit nodes around the world (enhanced subscription level).
- Supports over 400 services which you can block and/or redirect through their proxies. Examples include Google, Notion, Ring, AWS, Zoom, hundreds of streaming services, and more.
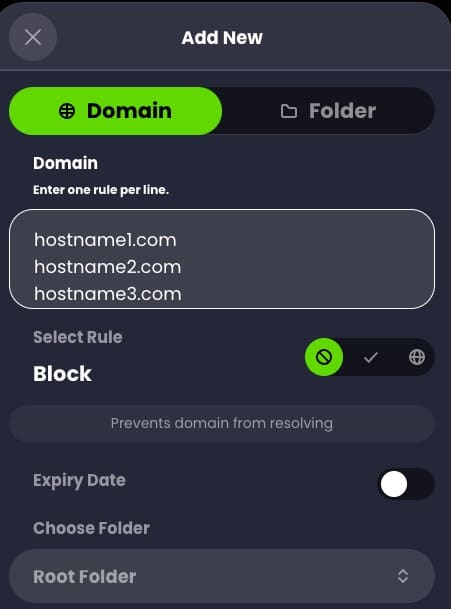
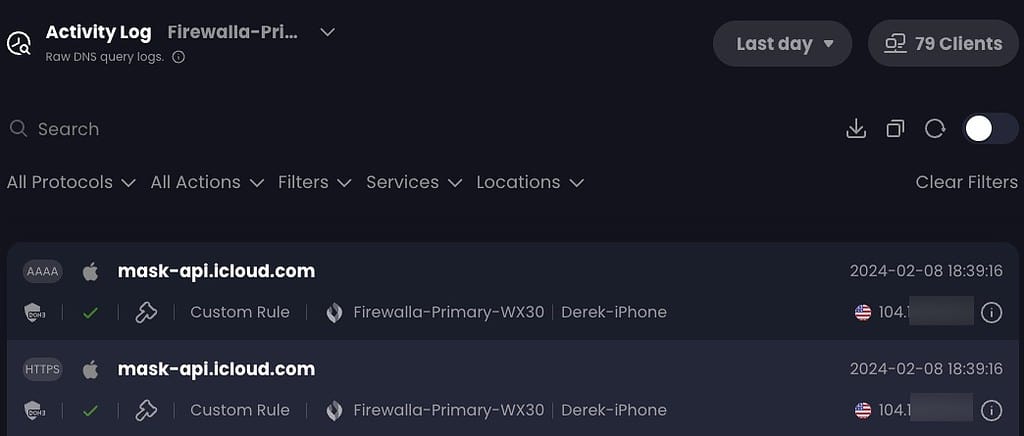
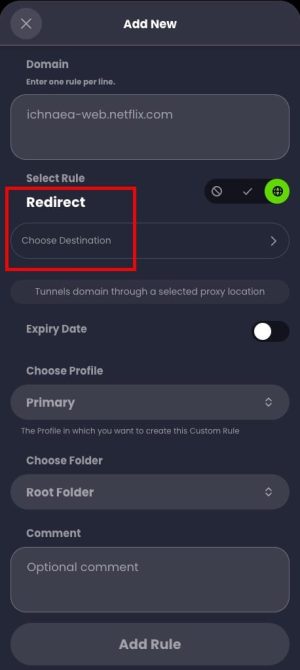
- Extensive custom rules including block, allow and re-writes. You can organize rules into folders, and even configure folder level rules (allow, block, redirect).
- Allows any end point can become a DDNS ‘beacon’ and update a user defined public xyz.controld.live domain in seconds of getting a new ISP address.
- No limits for their consumer home plan in terms of queries or devices. You can even have extended family in a single account.
- OS support includes Windows (x64, Arm), Mac (x64, Apple Silicon), Linux, and FreeBSD.
- Fully documented public API.
Control D Terminology
The Control D terminology is a bit different from NextDNS, and thus I was initially bit confused between devices, profiles and how they related to VLANs. Devices in Control D can both a network-level device (e.g. your router/firewall) or a client (e.g. your PC or phone). Profiles (e.g. DNS policies) are applied to devices.
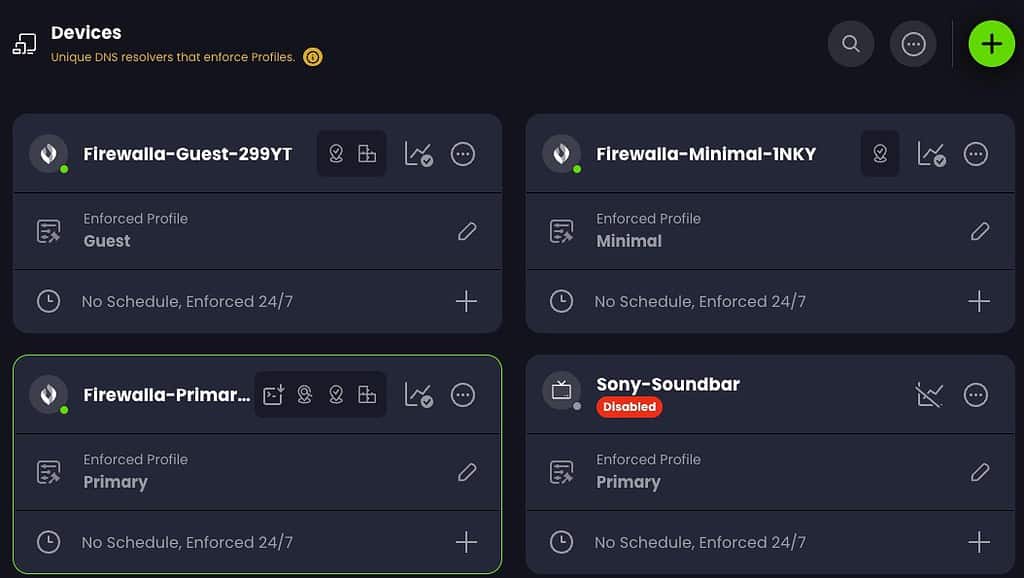
If you are fancy and have multiple VLANs at home, you can map a a VLAN to a ‘device’ via the configuration rules for your router via their TOML configuration file rules. In my case I have a “Firewalla-Primary” device for my main home VLAN and a “Firewalla-Guest” device that is for my guest VLAN. Both of these “devices” are mapped to my physical Firewalla firewall via a simple config file on my Firewalla (shown later).
You can also setup device-specific profiles, in case you have a device that needs custom rules. I have a Sony soundbar that is very chatty to Google DNS, so I totally block that puppy with a “device” that has a disable DNS policy.
Control D Installation
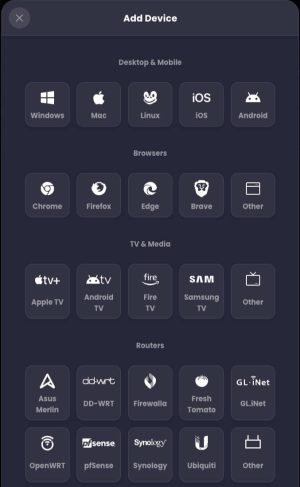
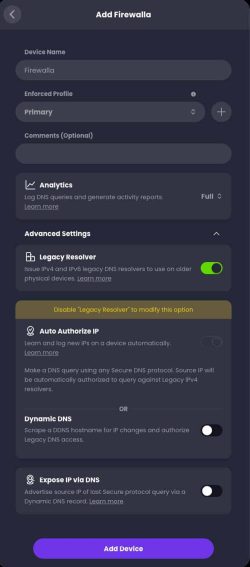
When you want to add a device (such as your router), Control D gives you a ton of options. Click on the type of device you want to use and it walks you through the configuration. (Click to enlarge all screenshots).
When you select a device type, you then get additional choices to customize as you wish. You can entirely disable analytics (logging), use a privacy sensitive mode (minimal high level stats), or opt in to full analytics. I chose full. You can also configure DDNS here as well.
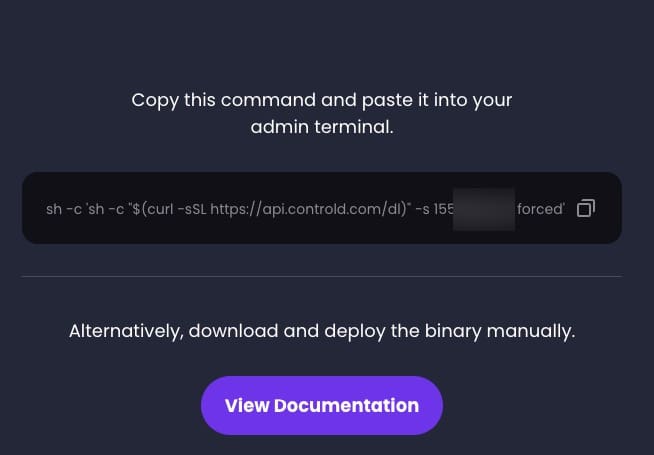
Control D then gives you a command line to run on your router that does all of the configuration, and even sets you up with a default DNS profile.
Note: For Firewalla users, their install script has a bug that results in your Control D configuration being lost upon a Firewalla reboot. I did a simple manual fix, and Control D support says they will fix their script.
Control D Profiles
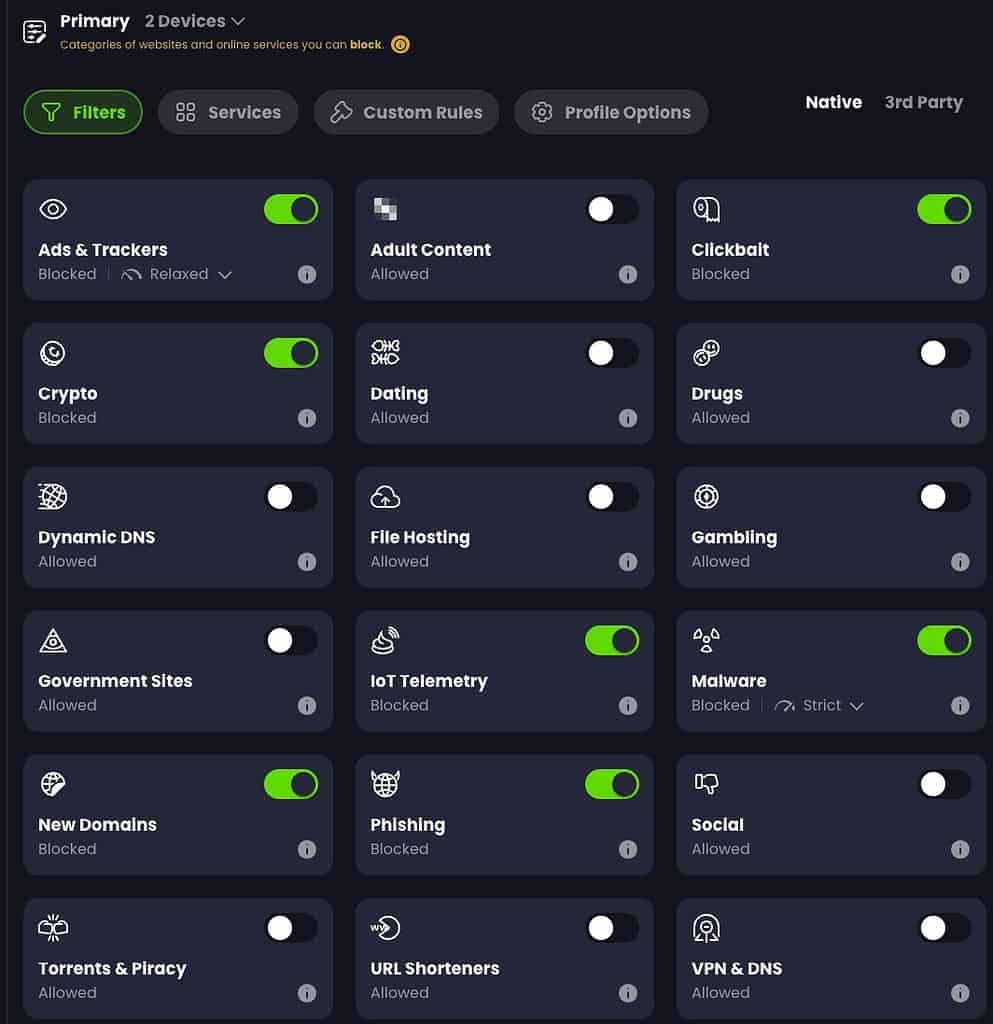
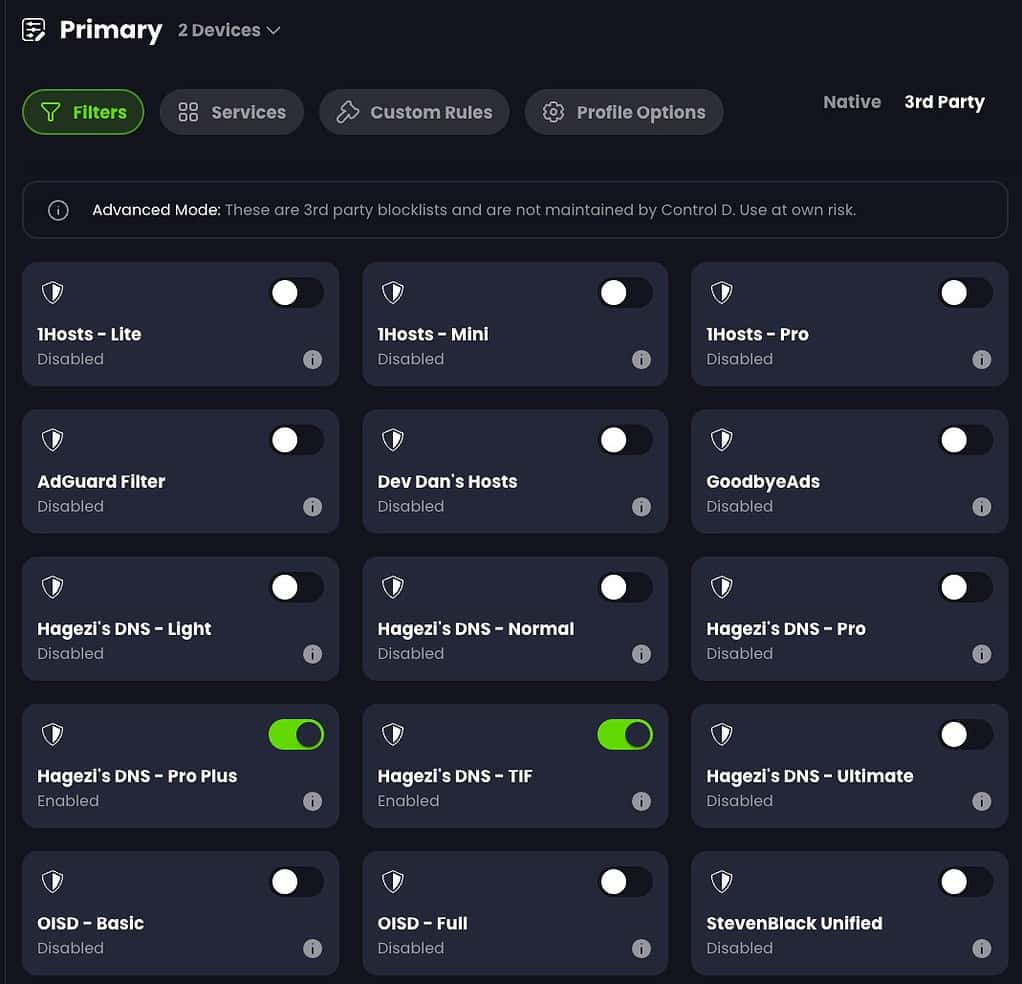
A Control D profile can be assigned to one or more devices. A profile is where you do most of the customization. On the Filters page you can enable/disable various classes of DNS filtering. Ads & Trackers and Malware both have multiple levels of blocking available.
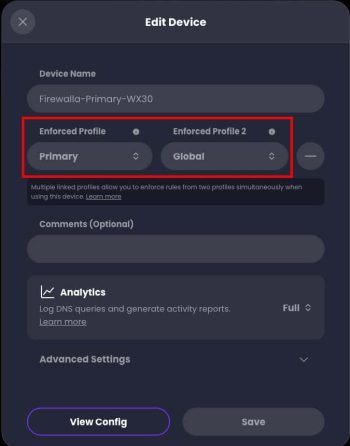
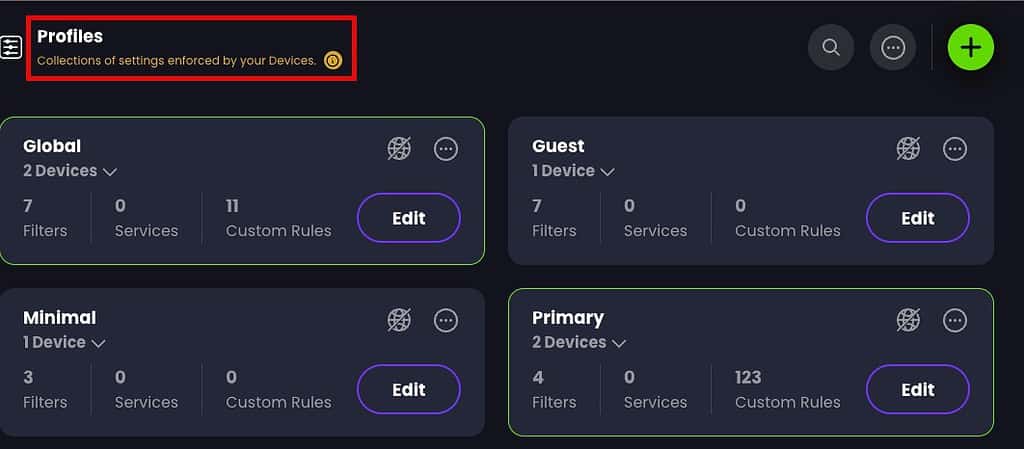
Fun fact: A Control D device can be assigned up to TWO profiles. Why is this awesome? Well, you can have a “Global” (my name, not theirs) policy that includes all the base blocking/allow/redirect that is common to two or more devices. You can then assign a second profile to the SAME (or different) devices which is tailored to that device with even more filters. This is in stark contrast with NextDNS, where a device can only be assigned a single profile.
Real world example: I have a “Global” policy which covers both my primary and guest networks, so there’s a common baseline of DNS filtering for both VLANs. I then have separate “primary” and “guest” policies which tailor DNS blocking for each of their respective VLANs for areas not covered in the global policy. This means I don’t need to try and line up primary and guest policies side by side for common settings…they are in a single shared profile. Pretty neat, and a good quality if life improvement over NextDNS. This also makes it easy to share redirects, as well.
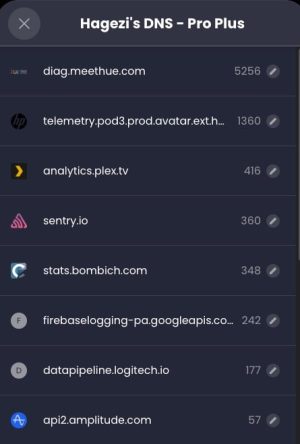
They also have a select number of third party lists, including several from the the highly regarded Hagezi. “Less is more” when it comes to DNS filtering. Don’t go hog wild turning on all the filters or you will be whitelisting domains all the time.
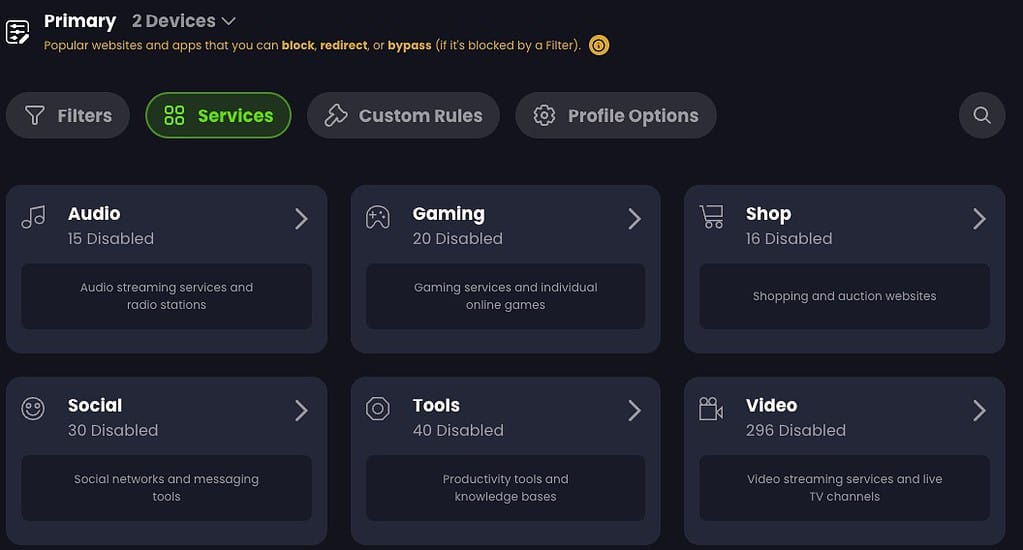
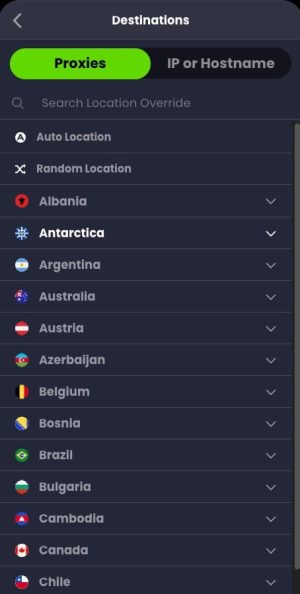
Here you can see the over 400 services that you can block, allow, or redirect through one of their 100+ global proxies. Drilling down into each category shows you the service name you can chose, such as Netflix, Paramount+, YouTube, etc.
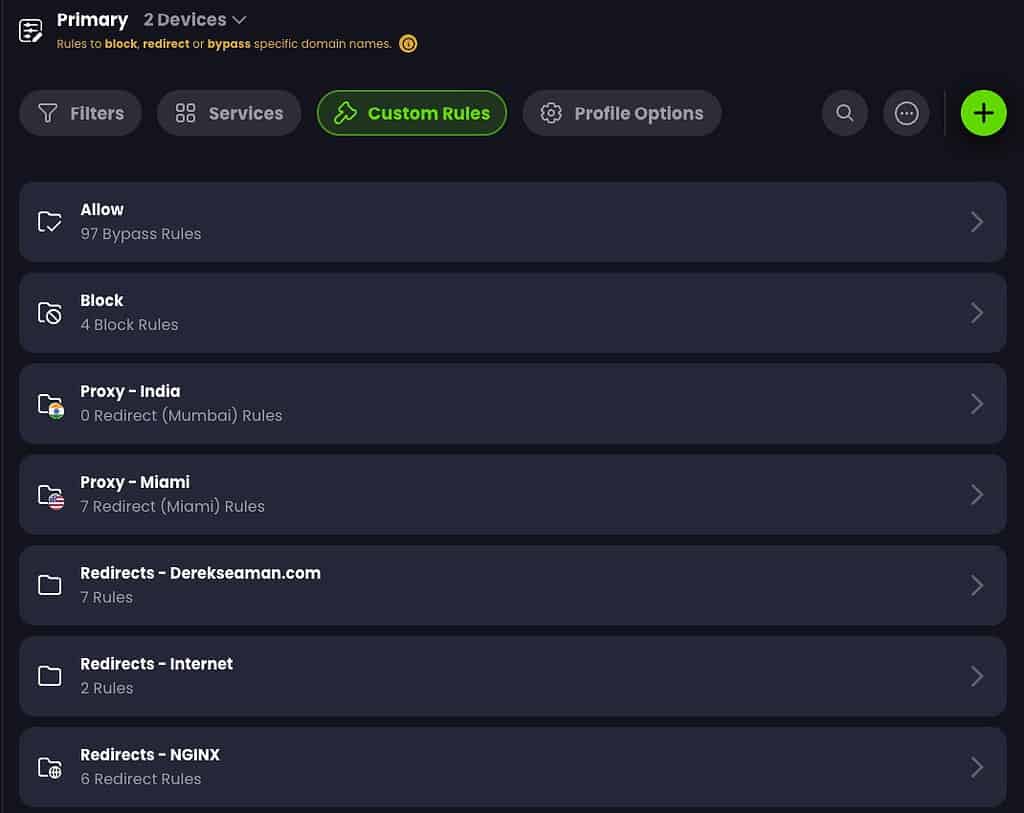
I really like the custom rules, and how you can organize your rules. Unlike NextDNS that only has allow, block and redirect lists (in different areas of the UI), Control D gives you folders. And optionally you can enforce folder-level rules of allow, block or redirect. I use all three. Or you can have a folder which has a combination of rule types..it’s all up to you. I have seven folders in my example below covering allow, block, proxy, and redirect rules.
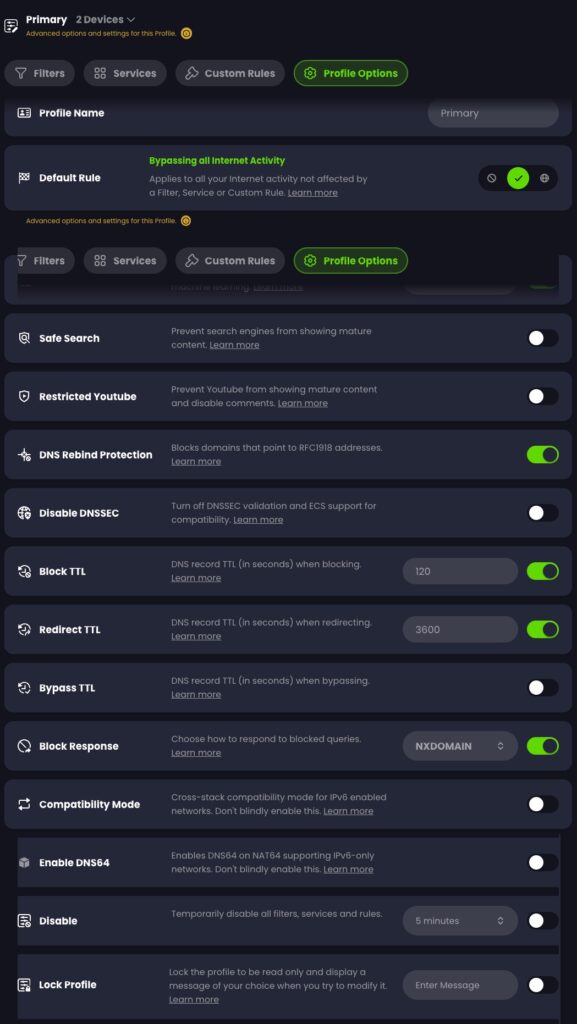
If you want to get very nerdy, then you can customize the DNS responses even more. You can change various record TTLs, block responses, AI malware filter level, and more. Note: If you use Plex, don’t enable DNS rebind protection.
Here you can see that I have four devices defined. In Control D the Devices are assigned a unique Resolver ID. We will use this Resolver ID a bit later when creating our Control D config file. For my purposes I defined three primary device types: Firewalla Primary, Firewalla Guest and Firewalla Minimal. My main home network uses Primary. My guest network, shockingly, uses Guest. And if I have any devices that need very lax DNS, I have Minimal. I also have a Sony soundbar that’s stupid and does endless Google DNS lookups so I entirely block that pooper.
Another cool feature in Control D is on the Profile screen it will highlight which profiles that the device accessing the Control D website is using. In my case you can see both Global and Primary apply to my Mac.
When configuring your allow/block/redirect rules you can also easily paste multiple entries at once. This made it easy to migrate my allow list from NextDNS to Control D, without having to copy and paste each FQDN individually. You can also set expiration dates for rules, which is pretty cool.
Control D Analytics
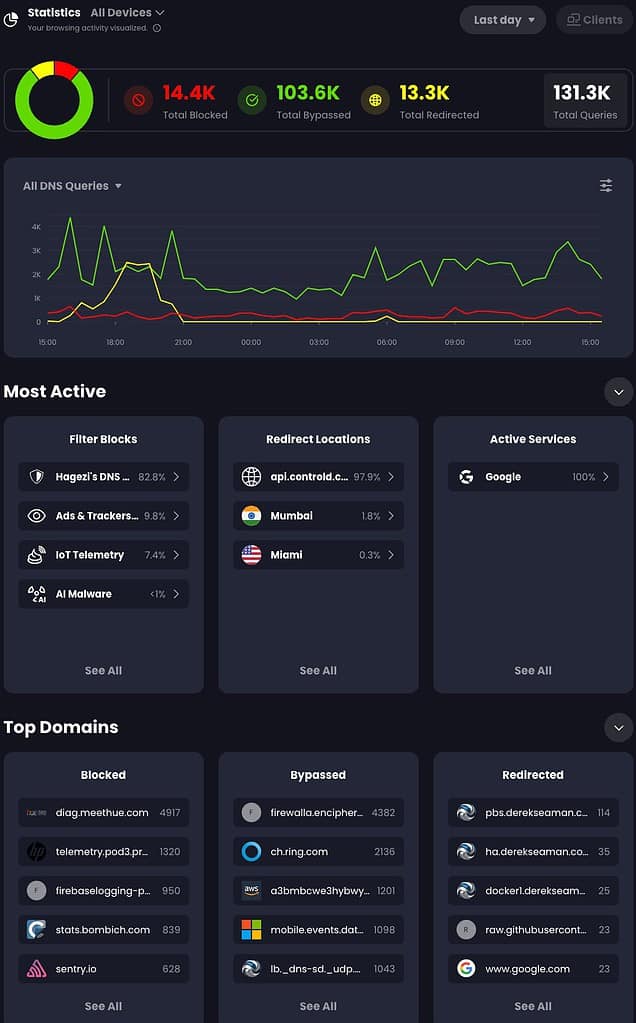
Control D has some great analytics, which mostly surpass of those in NextDNS. This screenshot is from the last 24 hours of using Control D. This is a summary of all devices/networks in my home. In the upper left you can drill down into specific devices/networks to zoom in on the data. You can also see my Netflix redirection to Brazil test.
What I really like, which was lacking NextDNS, is the ability to drill down into the blocks and redirections to see what was caught by that rule, down to the number of hits per FQDN. And right from this page you can click on the pencil icon and create a rule to allow/block/redirect as you wish. No more copying/pasting in the NextDNS console, which has been a multi-year complaint of users.
And for each “Device” (aka network in my case), you can list all of the clients and real time status of the last DNS query. You can then click on any client device, and see the same filter summary and top domains page as previously shown.
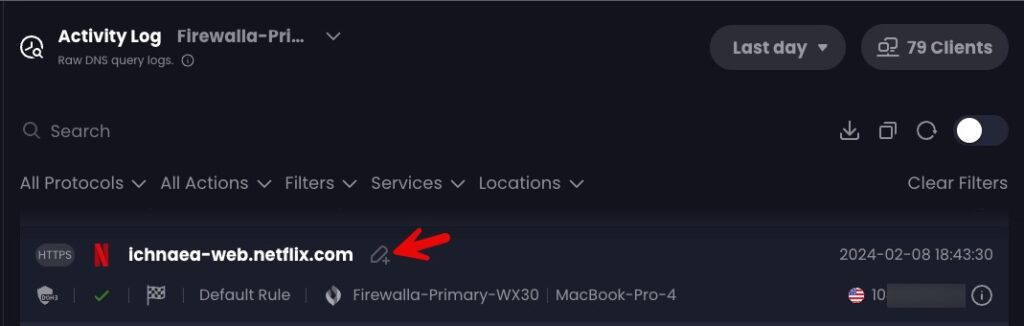
Control D also has rich filtering, in addition to real time streaming DNS logs. You can filter logs on many criteria.
DNS logs entries are also very detailed with record type (A, AAAA), any rule hits, device name, client device, time stamp, and public IP address the DNS request came from. You can also export logs to CSV, which has an astonishing amount of details. In fact, the CSV export has over 24 columns of details about EACH DNS query. It lists data such as:
- Time stamp
- Device ID
- Client ID
- DNS query (question)
- Query category
- Protocol
- Record Type
- Source ASN
- Source IP
- Source City
- DNS Query response
- Answering ASN
- Answering ISP
- Answering City
- Answering Country
Control D Proxy
A feature that NextDNS is entirely lacking is a native proxy (not VPN) service. Control D has over 100 global exit nodes in a wide range of countries. With just a few clicks you can redirect, for example, All Netflix traffic to the UK or Singapore. You can have multiple proxy rules in use a the same time. I did a couple of tests, and it seemed to work well.
I redirected YouTube to India, and sure enough when I went to youtube.com my landing page was full of Indian content. Google Search also had an Indian landing page. I also redirected Netflix to Brazil, which also worked. The proxy/redirection feature is a $20/yr premium add-on to their base plan, which is also $20/yr.
Control D Router Configuration
The real power of Control D comes when you install it on your router/firewall (many brands are supported). This is my actual running config at home. You can make more complex configurations, based on MAC addresses, domain names, and more. Control D has great documentation on all the options. I’m not even using a fraction on all their options.
I won’t go into great detail here, but I’m just briefly cover what my config does. I have three logical networks on my Firewalla. A primary network, guest network, and one for inbound Wireguard VPN connections. The config file below associates the relevant Control D Profile to the VLAN’s CIDR. I’m also using DoH/3 (DNS over HTTP3) to the upstream Control D DNS servers. This fully encrypts all DNS queries so my ISP can’t snoop on me (as easily).
[service]
metrics_query_stats = 'true'
cache_enable = 'true'
[listener]
[listener.0]
ip = '0.0.0.0'
port = 5354
[listener.0.policy]
name = 'Home Policy'
networks = [
{ 'network.0' = ['upstream.0']},
{ 'network.1' = ['upstream.1']},
{ 'network.2' = ['upstream.2']}
]
[network]
[network.0]
name = 'Primary'
cidrs = ['10.13.2.0/24']
[network.1]
name = 'Guest'
cidrs = ['192.168.193.0/24']
[network.2]
name = 'Wireguard'
cidrs = ['10.189.177.0/24']
[upstream]
[upstream.0]
name = 'Primary'
type = 'doh3'
endpoint = 'https://dns.controld.com/abc123456768'
timeout = 5000
ip_stack = 'both'
[upstream.1]
name = 'Guest'
type = 'doh3'
endpoint = 'https://dns.controld.com/xyz12345678'
timeout = 5000
ip_stack = 'both'
[upstream.2]
name = 'Minimal'
type = 'doh3'
endpoint = 'https://dns.controld.com/mno123456789'
timeout = 5000
ip_stack = 'both'
Control D CLI
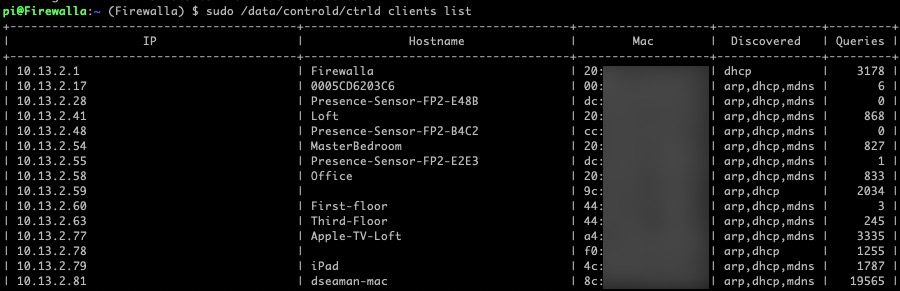
Installing the Control D server on your router gives it deep insight to all of the clients on your network. In fact, it uses DHCP snooping, ARP, mDNS and NDP protocols to find out all of the clients on your network, their IP address, and “name”. In fact, it discovered all 20 of my Matter/Thread devices with their IPv6 addresses. The veerrryyyyyy long list of clients it found on my network was astonishing, as it also listed each IPv6 address for every device I have.
sudo /data/controld/ctrld clients list
Missing NextDNS Features
Control D has a robust set of features, and I’m very happy with what they offer. However, NextDNS does have a few niche features that are currently lacking in Control D. Some of the missing features are:
- CNAME Flattening
- Web3 domains
- Block Parked Domains
- Block Domain Generation Algorithms
- Enable Anonymized EDNS Client Subnet
- Metrics: DNSSEC Query Percentage
- Metrics: Traffic Destination World Map
I personally don’t think any of these are deal breakers, so I wasn’t missing them with Control D.
Firewalla Integration
I’ve had my Firewalla firewall for quite a while, and I really love that device. The great thing about Control D is that they have an installer built specifically for the Firewalla. And unlike the community NextDNS package for Firewalla which is pretty ‘hacky’ (IMHO), the Control D client appears much cleaner and easier to configure. Modifying the Control D config file for complex rules and multiple VLANs is vastly easier than the community NextDNS CLI for Firewalla.
If you have a Firewalla, I would suggest turning off all ad-blocking and any other DNS filtering features. You don’t want to be troubleshooting DNS filtering at two points. Also, if you previously installed the community NextDNS CLI on your Firewalla, I would suggest doing a complete firmware reload. The NextDNS CLI uninstaller left Control D in a broken state, whereas after a firmware reload it worked flawlessly the first time. Firewalla restored ALL my settings, and the whole process took less than 20 minutes.
After you follow the Control D Firewalla installation instructions, you can edit the configuration file by running:
sudo vi /data/controld/ctrld.toml
You can reload the Control D configuration via:
sudo /data/controld/ctrld restart
Also, to ensure that DNS queries are directed to the Control D client and not bypassed, ensure in Firewalla that DNS over HTTPS and Unbound are OFF.
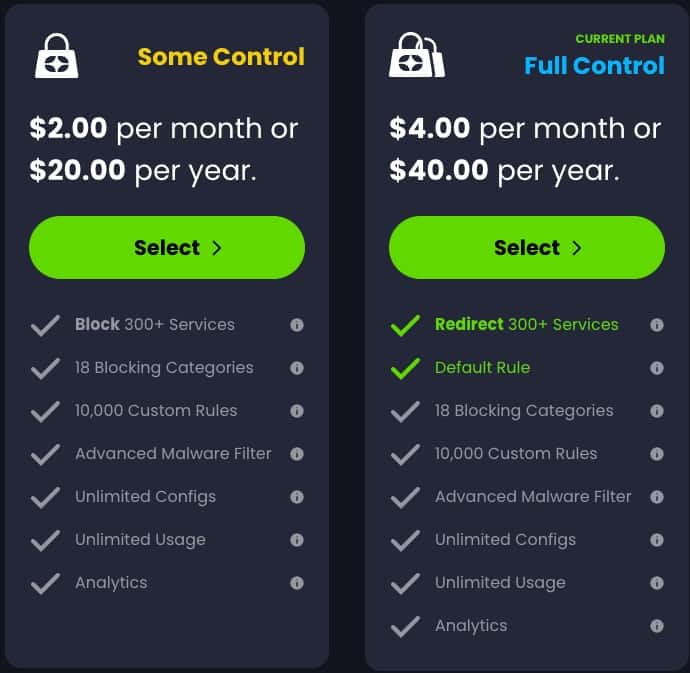
Subscription Plans
Since this is a cloud based service, there is a cost…just like NextDNS. However, their base plan (“Some Control”) is priced the same as NextDNS at $20/yr for unlimited queries AND they encourage one account for extended family members.
Their “Full Control” is a superset of features, adding proxy redirects to 300+ services. This tier also has a “Default Rule”, which makes you always appear from a different location (but you can add exceptions). That plan costs $40/yr, and can also cover extended family.
What don't I like?
No service is perfect, and Control D does have some shortcomings. However, none are show stoppers for me. Areas I’d like to see improved:
- Revamp UI/UX to be MUCH more compact. The whole UI wastes a huge amount of space on the screen. It’s like the UI was designed by gamers, not DNS professionals.
- Some settings a bit buried and hard to find. I think the whole UI needs a re-think. It’s not terrible, but doesn’t do the underlying platform justice. A hybrid NextDNS/Control D UI would be perfect.
- Ability to rename clients (coming soon, I heard) to meaningful names
- Better Control D server testing on various platforms (e.g. Firewalla bugs)
Summary
Control D is cloud based DNS service, much like NextDNS. However, the company behind Control D is rapidly innovating with new features every 2-3 weeks. Think agile development. You can check out their Change log here. I can’t recall a single NextDNS enhancement in years, so the new feature drops in Control D every few weeks is very refreshing.
Control D also has a number of quality of life features that are entirely lacking in NextDNS. Their base plan for unlimited DNS queries is the same cost at NextDNS at just $20/yr for the base (non-proxy) plan and $40/yr for the full plan with proxy support.





Really enjoyed this post (as well as your others here. I’m most interested in the Firewalla integration side. You mentioned: If you have a Firewalla, I would suggest turning off all ad-blocking and any other DNS filtering features. Are you suggesting that the Firewalla security rules should (need?) to be disabled? Using some of the Active Protect features, as well as Family configs, which are nice, because alerts happen in addition to just blocking the requests. I had also been using Unbound on it for a while, so I assume that also needs to be disabled prior to running their… Read more »
I just suggested turning off the Firewalla side of DNS blocking so that you don’t have two places to troubleshoot issues. But if you like the alerts and control of Firewalla, then just leave their blocking turned on. Yes disable unbound.
Thanks. Another question – it’s clear that rules can be made for the “device” level, in this case the Firewalla. I’m not using multiple networks/VLANs, so devices behind it will all show up as separate clients under that device. Are there ways to then apply specific policies at the client level (or ideally, groups of clients)?
It appears you can do that. I went into my client list on my primary Firewalla device. I then assigned (or in their terms, Linked) one of those clients to my Guest firewalla device. The client is now using the Guest Firewalla device and associated profiles. I think their UI for this, and trying to unlink, is a bit buried. But it does seem possible. I don’t see a way to group clients, just link individual ones. The Firewalla guest device I’m using in this case need not be a separate VLAN on your network…you can create devices without a… Read more »
Great post, thanks! I switched from nextdns to controlD too. I’ve read on Twitter that they’re working on a revamped UI as well, so there’s more to come. Such a nice service!
I like the GUI of ControlD. I switched from NextDNS to ControlD, for ONE WEEK. Like so many others, on several other platforms, ControlD servers were so slow, that it made the user experience unusable. This occurred on all network devices, including profiles loaded into iPhones and iPads. I had even installed the CLI on my router.
NextDNS may not have the GUI of ControlD, but has all of the same functionality, and it just works, FAST.
I also like the features of ControlD but find, that AdGuard DNS Service and NextDNS are really fast and actually more reliable than ControlD.
Habe ControlD will ramp up reliability and speed.
Thanks for the nice write up on control d.
I installed control d on my firewalla but notice three issues with the install.
Other than these it works great. Have you experienced any of these issues with your control d on your firewalla?