Session INF1273
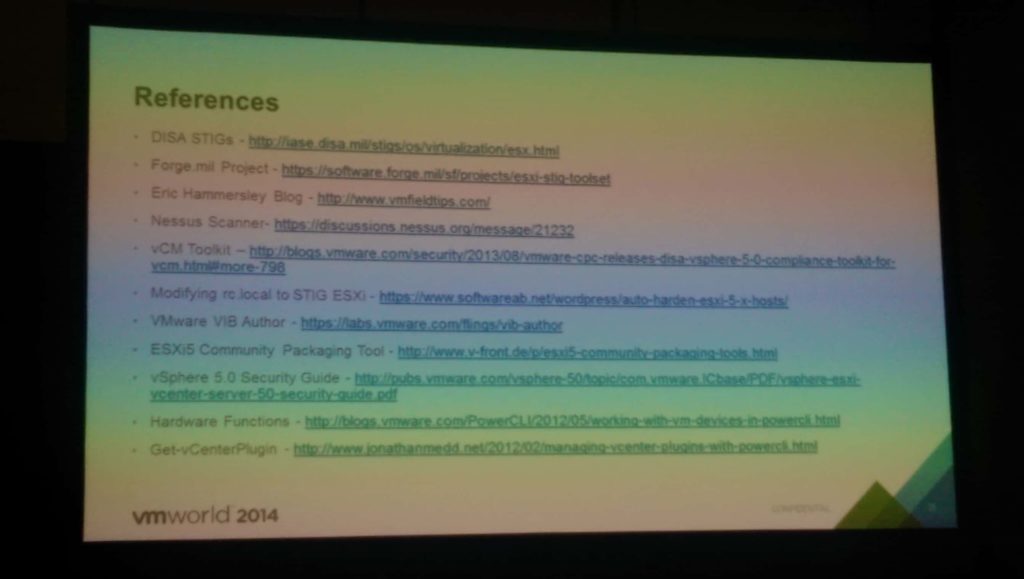
This was a very technical session on how to implement the DISA STIG’s (security lockdowns) for DoD/Government customers. Many of the slides contained script snippets that help automate the process. Thus my session notes are very light. If you are a U.S. Government Federal customer that must comply with the STIG’s, then look at the reference slide I have below. The speaker’s automated scripts and VIBs are located on a CAC-only web site for you to download. If you attended VMworld, then listen to this session and gain some insights on issues the authors found and how to overcome them.
—
STIGS are broken up into three area: hosts, VMs and vCenter
Checking VM settings with PowerCLI: Easiest report to create since it relies most only VMX settings
Checking ESXi settings with Power CLI: Most host STIG controls cannot be queried via exposed APIs. Shows a script that uses Plink and PowerShell to query settings.
Checking vCenter controls with PowerCLI: Very manual process.
ESXi host hardening requires changing of permanent files or adding new files. They will be non-persistent and disappear upon reboot.
ESXi5-CPT: Graphical tool to create VIBs that can replace files on ESXi hosts.
Use ‘ESXcli vib install -d <path> -no-sig-check’ to install the custom VIB or PowerCLI
Additional tools: vCenter Configuration manager (vCM), Nessus scanner, VMware compliance checker, DoD Forge.mil project




Where is the link for the automatic scripts you mentioned? Thanks