
So for vCenter 5.5 I wrote a PowerShell script that did all the SSL certificate creation ‘magic’ in one place. In the intervening weeks since the first version went up, I’ve made a number of changes based on user feedback (and code submission) and my own development effort. I want to develop it further, but that will have to wait for a number of weeks while I complete a big project I’m working on. But for those that did download the first version and haven’t seen my Tweets about updates, I wanted a dedicated post to highlight the full feature set of v1.41 (November 10th).
The script is designed to be used in conjunction with the VMware vCenter certificate automation tool, NOT replace it. While that tool will create CSRs, I find it a bit cumbersome and does not help you in minting the certs. Regardless of what kind of CA you have, the script will help. The degree of automation varies, as the script is targeted for an online Microsoft CA. Once you use my tool to mint all of your certificates, then it’s a straight forward matter of using the VMware certificate tool to replace the self-signed certificates with your freshly minted ones.
As you will see in the feature list, the script goes beyond just SSL assistance and can also aid in your SQL database and DSN creation.
The script has the following features:
- Downloads and installs the proper version of OpenSSL (0.9.8.Y) if it’s not already installed
- Creates 2048 bit RSA private keys in the proper format
- Creates a directory for each service bundle of SSL certificates
- Generates ten OpenSSL configuration files, one for each certificate, in the appropriate directory
- Creates certificates for AutoDeploy, Dump Collector and Syslog collector
- Downloads both root and subordinate root public certificates
- Submits the CSRs to the online CA and downloads the certificates
- Creates the needed service PEM files for the vCenter certificate automation tool
- Creates the required root/subordinate PEM files
- Handles the special SSO 5.5 certificate requirements
- Assumes all vCenter components are on one server
- Automatically uses the hostname of the server you run the script on for all certificates
- Creates a pre-filled vCenter Certificate Automation environment script – Just run!
- Works with offline CAs
- Creates SSO 5.5 certificate replacement files – Only used if manual replacing certs
- Creates customized SQL vCenter and VUM database creation script
- Creates SQL ODBC DSNs for vCenter and VUM
- Automatically downloads and installs SQL 2008 R2 or SQL 2012 client package
- Linux vCenter Server Appliance support for online minting and offline CSR creation
- Creates certificates for Auto Deploy, Dump Collector and Syslog collector
- Support Microsoft CAs that require manual certificate approval
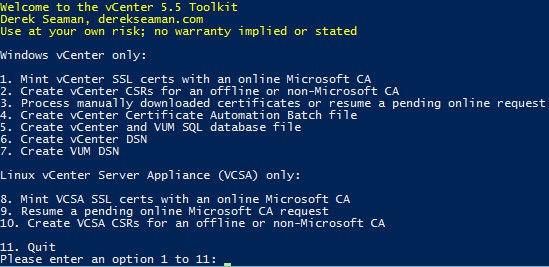
On the potential roadmap is replacing the ESXi 5.x host certificates, and a bit more robust Linux VCSA support. A screenshot of the main menu is shown below.
As always you can download the latest version from: vExpert.me/toolkit55 It’s gotten over 1,500 downloads in the few weeks that its been available, which is great. Hopefully it is helping people install vCenter 5.5 and more easily configure trusted certificates. For instructions on how to use the tool and a change log, start in Part 8 of my vCenter 5.5 install series.






I have a problem that I only get SHA1 signature hash algorithm on the certificates.
For example even though the file C:certsAutoDeployAutoDeploy.cfg created by the script contains default_md = sha512 under [ req ] the certificate file c:certsautodeployrui,crt created only has SHA1 which is not recommended.
I can't find any setting on the root CA that would force it to give out SHA1 instead of the requested SHA512 so I'm not sure why this would happen?
OpenSSL was downloaded and installed by the toolkit script so it should be the correct version also.
ah I solved it by doing this command on the root ca:
certutil -setreg cacspCNGHashAlgorithm SHA512
restarting the certificate services, and issuing a new SHA512 root CA certificate.
then recreating certificates on on vcenter server with your script and then restarting the vcenter server to make sure new root CA certificate got installed on server.
Not sure if that is the best way to do it but it seems to work well.