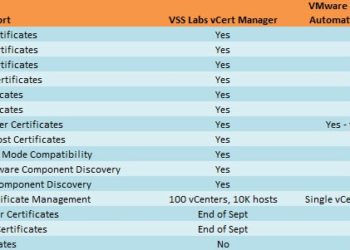
vCenter 5.5 SSL Certificate and SQL Toolkit Updated
Fresh off the press is an updated version of my vCenter 5.5 SSL certificate Toolkit script. Last year when I did my popular vCenter 5.1 install series the posts contain a series of scripts and CLI commands to replace the SSL certificates. While that process worked for many people, it still...