Some industries, like Government, require the use of certain cryptography algorithms. One of the great features of Windows Server 2008 R2 and Windows 7 is the support for TLS 1.2 ciphers. TLS 1.2 ciphers support AES-256 encryption with SHA-256 hashes. Unfortunately, Microsoft did not enable these protocols out of the box. I wanted IIS 7.5 to negotiate TLS 1.2 connections with my Windows 7 clients. After some registry hacking I was successful, as shown by a Wireshark trace.
I created a simple PowerShell script that enables TLS 1.2 for both client and server communications. It also disables SSL 2.0 server responses, in case you need to be PCI compliant. The lines are pretty long, so pay attention to the wrapping. After you run the PS script (with elevated rights) you must reboot the client and server.
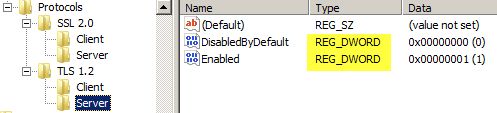
Please note that all values must be DWORD. This is very important, as any other value type will NOT work and you may be pulling your hair out wondering why it’s not working.
# Enables TLS 1.2 on Windows Server 2008 R2 and Windows 7 # These keys do not exist so they need to be created prior to setting values. md "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2" md "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server" md "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client" # Enable TLS 1.2 for client and server SCHANNEL communications new-itemproperty -path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server" -name "Enabled" -value 1 -PropertyType "DWord" new-itemproperty -path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server" -name "DisabledByDefault" -value 0 -PropertyType "DWord" new-itemproperty -path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client" -name "Enabled" -value 1 -PropertyType "DWord" new-itemproperty -path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client" -name "DisabledByDefault" -value 0 -PropertyType "DWord" # Disable SSL 2.0 (PCI Compliance) md "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server" new-itemproperty -path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server" -name Enabled -value 0 -PropertyType "DWord"
After you run the PowerShell script, you should see DWORD entries like those shown below. Also, go into the Advanced properties of IE and check the box next to TLS 1.2.
If you start a WireShark capture on a TLS session you will know it’s v1.2 by two easy methods. First, the Protocol column will show TLSV1.2. Secondly, if you open the ServerHello packet you should see burried in the packet:
Cipher Suite: TLS_RSA_WITH_AES_256_CBC_SHA256 (0x003d)
You can also configure the advanced settings in IE8 on Windows 7 or Server 2008 R2 to only use TLS 1.2 by de-selecting all other SSL/TLS options. If your browser can connect with just TLS 1.2 selected, then you are golden. But for 100% verification, use a packet sniffer.
Another tweak you can do to your system is change the order of the cipher suites that Windows negotiates. This is possible in Windows Vista and higher. I changed the order such that TLS_RSA_WITH_AES_256_CBC_SHA256 is at the top of the list. Next to elliptical curve ciphers, this is the strongest that Windows offers.
To change the cipher suite order, open the GPMC on a Server 2008 or higher DC and navigate to: Computer\ Configuration\Policies\Administrative Templates\Network\SSL Configuration Settings. Enable the policy, then copy the cipher suites to Notepad and change the order as you wish. I just flipped the first two entries. So my first two entries look like:
TLS_RSA_WITH_AES_256_CBC_SHA256,TLS_RSA_WITH_AES_128_CBC_SHA256
I haven’t done extensive testing to know what types of compatibility problems enabling TLS 1.2 may create. So as always, test, test, test! I confirmed with WireShark that the Windows RMS client in Windows 7 will use TLS v1.2 to contact the root Windows Server 2008 R2 RMS server.
During my research I stumbled upon a cool Microsoft web site that lets you test various cipher suites with your browser. If you click on the cipher suites on the server authentication line you can see what your browser will support.
Lastly, Microsoft has a good reference of which cipher suites are associated with which protocols.






to correct the problem you are encountering due to the load-balancer not using TLS1,2 is to change the order back to the orginal: TLS_RSA_WITH_AES_256_CBC_SHA256, TLS_RSA_WITH_AES_128_CBC_SHA256
I think you’re missing some that affect TLS1.0
TLS_RSA_WITH_AES_128_CBC_SHA, TLS_RSA_WITH_AES_256_CBC_SHA
Hi,I am seeing conflicting information on enabling SSL3, TLS 1.0, etc. Some sites (like yours) say creating the Enable key with a value of 0x1. Other sites state the value must be 0xffffffff. Any insight?Thanks.
Use 0xffffffff for ciphers and 0x1 for protocols
I have the same question about the value: Is it 0x1 of 0xffffffff?
I’m actually trying to enable a specifc weak cipher on my web server because of a specific client requirement. No matter what I do, SSLScan always shows a pretty short list of Accepted cipher suites. Anybody have ideas? I’ve tried using IISCrypto utility to enable the settings I want. I’m specifcally trying to enable TLS_RSA_WITH_NULL_SHA. I know, why would I want that? I’m setting up a server to deploy firmware and settings to Avaya phones. The older models only support TLS_RSA_WITH_NULL_SHA. It’ll be awhile before those phones go away so I need the server with support NULL_SHA for now.
Supported Server Cipher(s):
Failed SSLv2 168 bits DES-CBC3-MD5
Failed SSLv2 56 bits DES-CBC-MD5
Failed SSLv2 128 bits IDEA-CBC-MD5
Failed SSLv2 40 bits EXP-RC2-CBC-MD5
Failed SSLv2 128 bits RC2-CBC-MD5
Failed SSLv2 40 bits EXP-RC4-MD5
Failed SSLv2 128 bits RC4-MD5
Failed SSLv3 256 bits ADH-AES256-SHA
Failed SSLv3 256 bits DHE-RSA-AES256-SHA
Failed SSLv3 256 bits DHE-DSS-AES256-SHA
Failed SSLv3 256 bits AES256-SHA
Failed SSLv3 128 bits ADH-AES128-SHA
Failed SSLv3 128 bits DHE-RSA-AES128-SHA
Failed SSLv3 128 bits DHE-DSS-AES128-SHA
Failed SSLv3 128 bits AES128-SHA
Failed SSLv3 168 bits ADH-DES-CBC3-SHA
Failed SSLv3 56 bits ADH-DES-CBC-SHA
Failed SSLv3 40 bits EXP-ADH-DES-CBC-SHA
Failed SSLv3 128 bits ADH-RC4-MD5
Failed SSLv3 40 bits EXP-ADH-RC4-MD5
Failed SSLv3 168 bits EDH-RSA-DES-CBC3-SHA
Failed SSLv3 56 bits EDH-RSA-DES-CBC-SHA
Failed SSLv3 40 bits EXP-EDH-RSA-DES-CBC-SHA
Failed SSLv3 168 bits EDH-DSS-DES-CBC3-SHA
Failed SSLv3 56 bits EDH-DSS-DES-CBC-SHA
Failed SSLv3 40 bits EXP-EDH-DSS-DES-CBC-SHA
Accepted SSLv3 168 bits DES-CBC3-SHA
Failed SSLv3 56 bits DES-CBC-SHA
Failed SSLv3 40 bits EXP-DES-CBC-SHA
Failed SSLv3 128 bits IDEA-CBC-SHA
Failed SSLv3 40 bits EXP-RC2-CBC-MD5
Accepted SSLv3 128 bits RC4-SHA
Accepted SSLv3 128 bits RC4-MD5
Failed SSLv3 40 bits EXP-RC4-MD5
Failed SSLv3 0 bits NULL-SHA
Failed SSLv3 0 bits NULL-MD5
Failed TLSv1 256 bits ADH-AES256-SHA
Failed TLSv1 256 bits DHE-RSA-AES256-SHA
Failed TLSv1 256 bits DHE-DSS-AES256-SHA
Accepted TLSv1 256 bits AES256-SHA
Failed TLSv1 128 bits ADH-AES128-SHA
Failed TLSv1 128 bits DHE-RSA-AES128-SHA
Failed TLSv1 128 bits DHE-DSS-AES128-SHA
Accepted TLSv1 128 bits AES128-SHA
Failed TLSv1 168 bits ADH-DES-CBC3-SHA
Failed TLSv1 56 bits ADH-DES-CBC-SHA
Failed TLSv1 40 bits EXP-ADH-DES-CBC-SHA
Failed TLSv1 128 bits ADH-RC4-MD5
Failed TLSv1 40 bits EXP-ADH-RC4-MD5
Failed TLSv1 168 bits EDH-RSA-DES-CBC3-SHA
Failed TLSv1 56 bits EDH-RSA-DES-CBC-SHA
Failed TLSv1 40 bits EXP-EDH-RSA-DES-CBC-SHA
Failed TLSv1 168 bits EDH-DSS-DES-CBC3-SHA
Failed TLSv1 56 bits EDH-DSS-DES-CBC-SHA
Failed TLSv1 40 bits EXP-EDH-DSS-DES-CBC-SHA
Accepted TLSv1 168 bits DES-CBC3-SHA
Failed TLSv1 56 bits DES-CBC-SHA
Failed TLSv1 40 bits EXP-DES-CBC-SHA
Failed TLSv1 128 bits IDEA-CBC-SHA
Failed TLSv1 40 bits EXP-RC2-CBC-MD5
Accepted TLSv1 128 bits RC4-SHA
Accepted TLSv1 128 bits RC4-MD5
Failed TLSv1 40 bits EXP-RC4-MD5
Failed TLSv1 0 bits NULL-SHA
Failed TLSv1 0 bits NULL-MD5
-Sam O
[email protected]
Hi Derek,
I just stumbled on your blog while trying to resolve an issue (upgrading to TLS 1.2) on Windows Server 2008 R2. I have already run the first line of the commands to create the TLS key, but have not been successful in running the second and subsequent lines of command. I will appreciate any assistance you could render to resolving this issue. Also, advise me on any possible challenge(s) that could arise and the solution.
Use this tools to setup the protocol and algorithm. _https://www.nartac.com/Products/IISCrypto/
Do you need "DisabledByDefault" in the "Server" key? I thought "Enabled" was for the "Server" key and "DisabledByDefault" for the "Client" key. That was my interpretation of http://support.microsoft.com/kb/245030 at least.
I am looking for a similar solution but to Windows XP and Windows NT. Any help please.
Thanks Derek!!!
Yeah, yeah, we’re still nursing a 2010 Exchange server and 10+ years later this page came in handy. Thank you for the correct solution.
Hi Derek,
I have a requirement to implement TLS 1.2 support in our .net winforms application which uses raw sockets. I have tried creating the registry keys that you suggested but still it’s not working. Do I need to modify my application as well in order for it to communicate with a meter which has a TLS 1.2 compliant firmware and expecting the client applications to have the same? Please suggest.
Thanks,
Rajaiah.