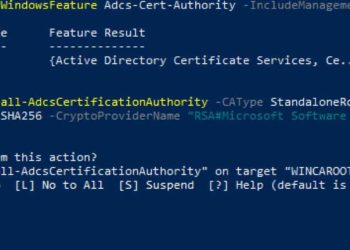
Windows Server 2019 Two-Tier PKI CA Pt. 1
Its been quite some time since I wrote up how to setup a Microsoft Windows two-tier certificate authority (CA). While Windows Server 2019 is not new, I did want to write up how to set a two-tier certificate authority (CA). I'm building out a new home lab, and thought this...