Problem Solved: Can’t login to the vCenter Appliance
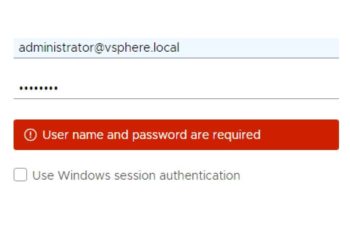
I was doing some testing in my lab with vCenter 7 (VCSA), using snapshots. I rolled back a test vCenter instance and was unable to subsequently login. The error I got was: User name and password are required. I also noticed that the windows session authentication was also check-able, even...