vSphere 6.0 Pt. 13: VMware Directory Svc Certificate
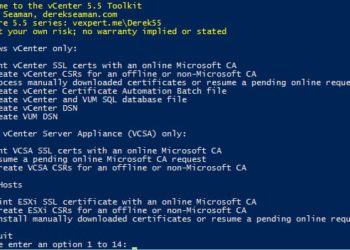
One of the lesser known SSL certificates in the vSphere 6.0 product is called the VMware Directory Service certificate. This is used by the built-in LDAP server for authentication and encryption. It's most an internal use only certificate, and one that some customers may not worry about replacing. In fact, per...