This session was presented by Mark Simos, Aaron Margosis from Microsoft. Pass the hash (PtH) is an extremely common method that companies become owned by the bad guys. This session covered what PtH is, how it works, and some mitigation techniques. Microsoft recently released an extensive whitepaper on mitigating PtH attacks, which is well worth a read. Microsoft is releasing an updated version this week, so check for the 2013 version if you already have looked at the December 2012 version. The download link is in the session notes.
Background
- The problem is that the internet is a source of a lot of good, with easy and instant IP connectivity.
- The information that is worth money is stored on a computer (criminal organization, intelligence agency are after your data)
- A lot of different organizations hack for various reasons. A logging company in Brazil hacked a rainforest quota system so they could log more and make more money.
- Hackers use your own systems against you. They take your admin credentials and the consequences can be deadly. 99% of the time they hack you for data/IP theft.
- The bad guys have the power to completely erase your data and render PCs unbootable if they wanted. An example was shared of a middle east oil company where 75% of the company’s 30,000 PCs were completely wiped and data files replaced with an animated gif of a burning American flag.
- Lateral movement: A attacker uses the credentials obtained from a compromised computer to gain access to another computer of the same value to the organization.
- Privilege escalation: The attacker uses the credentials obtained from a compromised computer to gain access to another computer of a higher value to the organization.
Attacks
- Typical pass the has attack:
- 1) Starts in a phishing email or watering hole attack (find a place users already goes, and stake it out by compromising the website) and targets workstations in masse. System needs to be compromised at the system-level, not just in the user space.
- 2) Running as local admin the bad guys takes credentials for lateral traversal
- 3) Bad guy acquires domain admin credentials
- 4) Bad guy has direct or indirect access to read/write/destroy data and systems in the environment
- If all computers have the same local admin password, then one compromised PC has compromised all PCs
- Removing admin rights from users significantly raises the bar on compromising a PC. Zero day exploit, unpatched application, etc.
- Most pass the hash attacks are human speed attacks (not automated malware) using a remote human controller (remote shell)
- Windows credential editor v1.4 beta by Amplia Security (download link)
- wce -w can also display plain text password as well
- wce has early code for using “pass the ticket” (Kerberos) attacks, but very uncommon
- pwdump7.exe was also demoed
- Easily can recompile the wce binary to hide from A/V software
- In real world attacks a complete domain can be compromised in 6 minutes to 24 hours
- Why can’t Microsoft just patch this? Local admins own the box, so they can look at any aspect of the OS and dump the passwords. MS should change the entry points, encryption, etc. and hackers will quickly release new tools. Microsoft hinted something was coming down the pipeline in the future to help, but was extremely vague.
Practical Mitigations
- Download the full Microsoft whitepaper for PtH mitigation here. Check back for the June 2013 version, as a new version will be released shortly.
- Mitigation 1: Restrict and protect high privileged domain accounts. Excellent effectiveness. Medium effort required.
- Don’t allow domain admins to logon to workstations
- Don’t create service accounts that use domain admin creds
- Mitigation 2: Restrict and protect local accounts with admin privileges. Excellent effectiveness. Low effort required.
- Explicitly deny network and remote desktop logon rights for all administrative local accounts
- Create random passwords for local accounts with administrative privileges
- Mitigation 3: Restrict inbound traffic using the Windows firewall. Excellent effectiveness, medium effort required.
- “Local account token filter policy” should be enabled (don’t set this to 1) as it opens up to pass the hash attack
- Whitepaper updated this week for Lync peer-to-peer considerations
- If you implement these three mitigations, then you are head and shoulders above nearly all other organizations. Attackers will have a much harder time in compromising your systems. Certainly doable, but these raise the bar significantly.
Other Mitigations (that don’t help that much)
- Disable NTLM (very costly in terms of implementing and testing. Likely break A LOT of software/hardware like printers)
- Smart cards and multifactor authentication (random password hashes are still stored and used in the background. They are static hashes that never expire, so almost worse than password hashes that require regular changing)
- Jump servers (has good value for other reasons, not just pass the hash). Keystroke loggers and other malware reduce their effectiveness for PtH attacks.
- Rebooting workstations and servers. Many service accounts and services may use domain credentials, so they are cached upon reboot.
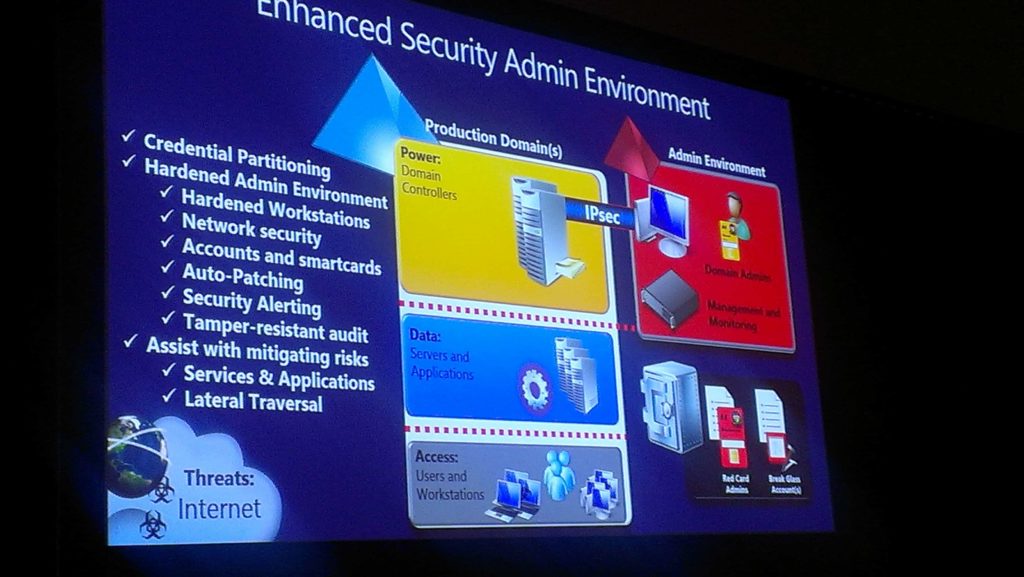
Microsoft also showed off a high level diagram of a security architecture that drastically mitigates PtH attacks. Microsoft professional services. The slide below shows the high level enhanced security environment.






Thanks for making this printable cheers will download PDF!